Question: Exercise: Encrypting Text with a Substitution Cipher (pair) This is a pair exercise to complete with your lab partner. Write a C program substitution.c which
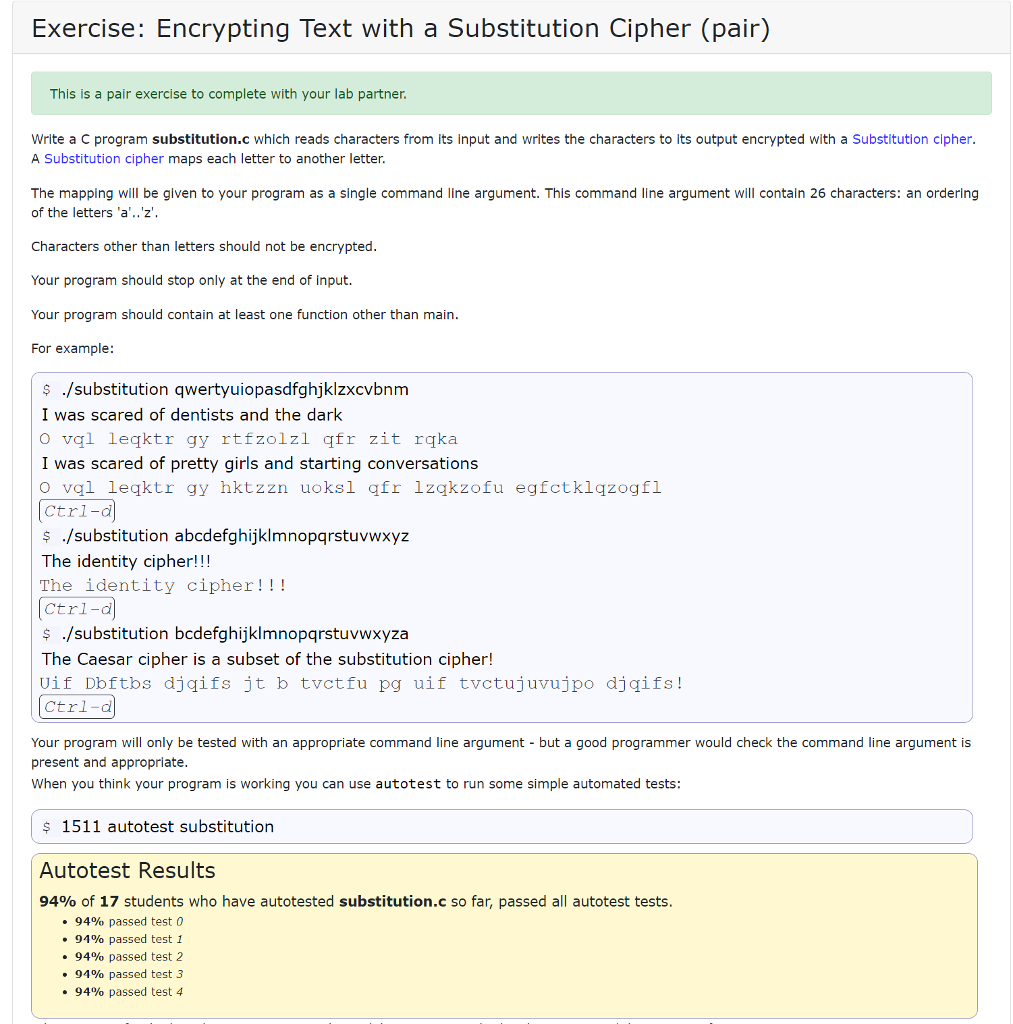
Exercise: Encrypting Text with a Substitution Cipher (pair) This is a pair exercise to complete with your lab partner. Write a C program substitution.c which reads characters from its input and writes the characters to its output encrypted with a substitution cipher. A Substitution cipher maps each letter to another letter. The mapping will be given to your program as a single command line argument. This command line argument will contain 26 characters: an ordering of the letters 'a'..'z'. Characters other than letters should not be encrypted. Your program should stop only at the end of input. Your program should contain at least one function other than main. For example: $ ./ substitution qwertyuiopasdfghjklzxcvbnm I was scared of dentists and the dark O val leqktr gy rtfzolzl qfr zit raka I was scared of pretty girls and starting conversations o val leqktr gy hktzzn uoksl qfr lzqkzofu egfctklqzogfl Ctrl-d] $ ./substitution abcdefghijklmnopqrstuvwxyz The identity cipher!!! The identity cipher! ! ! Ctrl-d] $ ./substitution bcdefghijklmnopqrstuvwxyza The Caesar cipher is a subset of the substitution cipher! Uif Dbftbs djqifs jt b tvctfu pg uif tvctujuvujpo djqifs! Ctrl-d Your program will only be tested with an appropriate command line argument - but a good programmer would check the command line argument is present and appropriate. When you think your program is working you can use autotest to run some simple automated tests: $ 1511 autotest substitution Autotest Results 94% of 17 students who have autotested substitution.c so far, passed all autotest tests. 94% passed test 0 94% passed test 1 94% passed test 2 94% passed test 3 94% passed test 4
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


