Question: Explain the handshake and encryption processes used to establish the SSH session, transfer content between the client and server, and terminate the session. Provide specifics
Explain the handshake and encryption processes used to establish the SSH session, transfer content between the client and server, and terminate the session. Provide specifics regarding session keys, protocols used, and sequence of events.
Illustrate the process, similar to the illustration of the SSL process in illustrated in Figure 1.
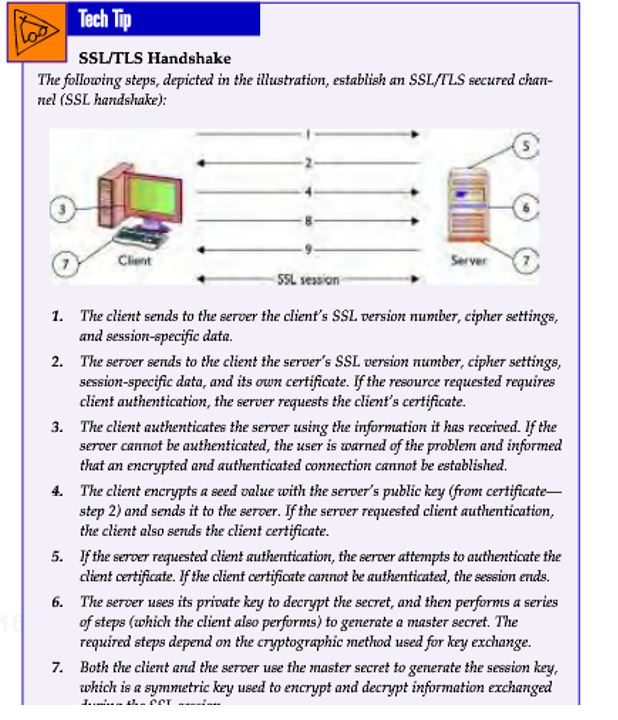
Figure 1: SSL/TLS Handshake
Tech Tip SSLTLS Handshake The following steps, depicted in the illustration, establish an SSL/TLS secured chan- nel (SSL handshake) Client Server 55L session The client sends to the server the client's SSL version number, cipher settings, and session-specific data. The server sends to the client the server's SSL version number, cipher settings, session-specific data, and its own certificate. Ifthe resource requested requires client authentication, the server requests the client's certificate. The client authenticates the server using the information it has received. If the server cannot be authenticated, the user is warned of the problem and informed that an encrypted and authenticated connection cannot be established. The client encrypts a seed value with the server's public key from certificate- step 2) and sends it to the server. If the server requested client authentication, the client also sends the client certificate. 1. 2. 3. 4. 5. If the server requested client authentication, the server attempts to authenticoate the client certificate. If the client certifioate cannot be authenticated, the session ends. 6. The server uses its private key to decrypt the ecret, and then performs a series of steps (which the client also performs) to generate a master secret. The required steps depend on the cryptographic method used for key exchange. Both the client and the server use the master secret to generate the session key, which is a symmetric key used to encrypt and decrypt information exchanged 7
Step by Step Solution
There are 3 Steps involved in it
SSH Handshake and Encryption Process The SSH protocol is designed to provide secure communication over an unsecured network Heres a detailed stepbyste... View full answer

Get step-by-step solutions from verified subject matter experts


