Question: Figure 1 : Communication network G shown on the left. The lightly shaded nodes are the operators, the dark shaded nodes are the spies, and
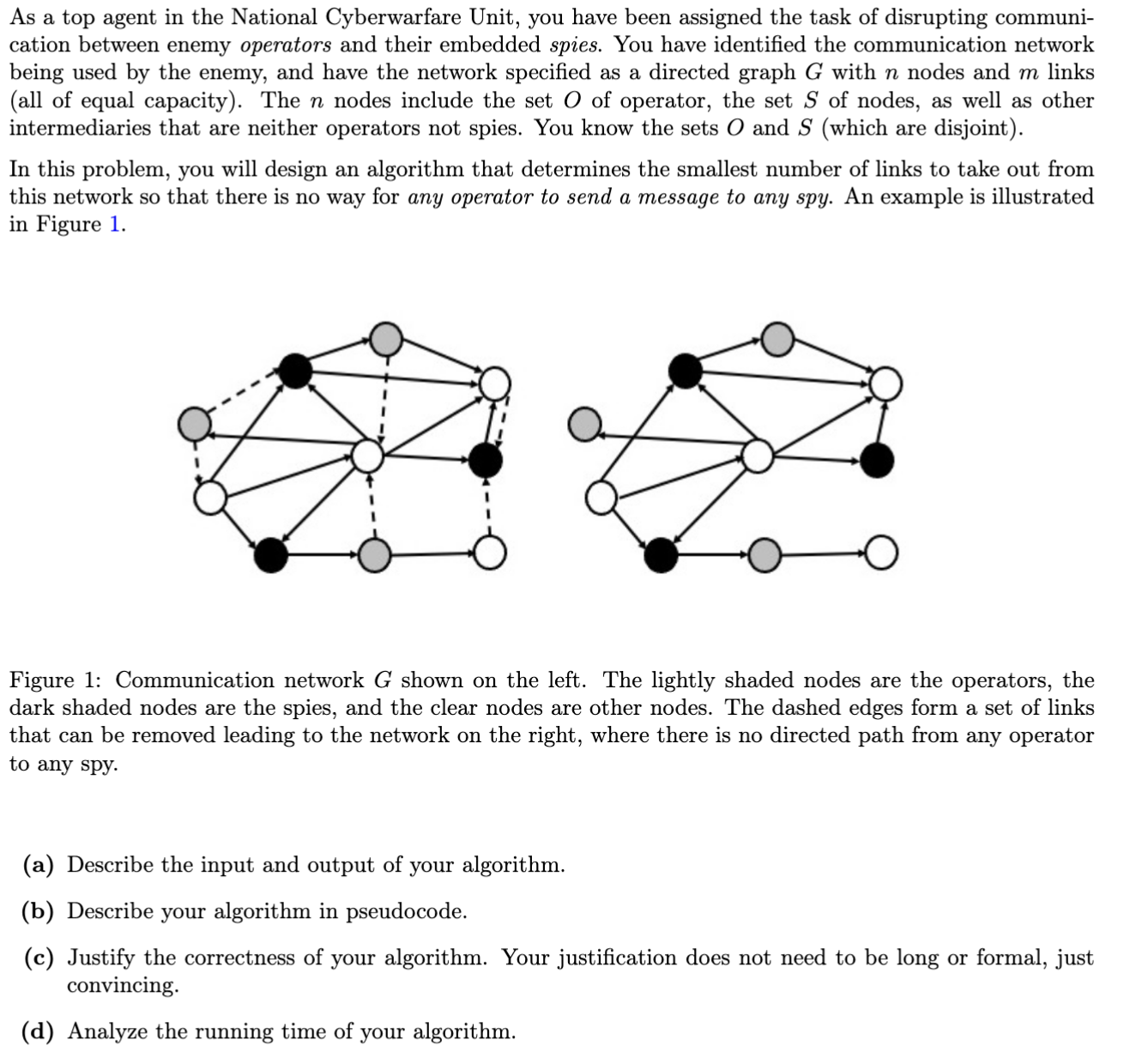
Figure : Communication network shown on the left. The lightly shaded nodes are the operators, the
dark shaded nodes are the spies, and the clear nodes are other nodes. The dashed edges form a set of links
that can be removed leading to the network on the right, where there is no directed path from any operator
to any spy
a Describe the input and output of your algorithm.
b Describe your algorithm in pseudocode.
c Justify the correctness of your algorithm. Your justification does not need to be long or formal, just
convincing.
d Analyze the running time of your algorithm.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


