Question: FIGURE 1 NEED HELP WITH Wireless Security QUESTIONS 1. Which of the following would best address Social Engineering attacks? a. Better firewalls b. Reverse Proxy




FIGURE 1
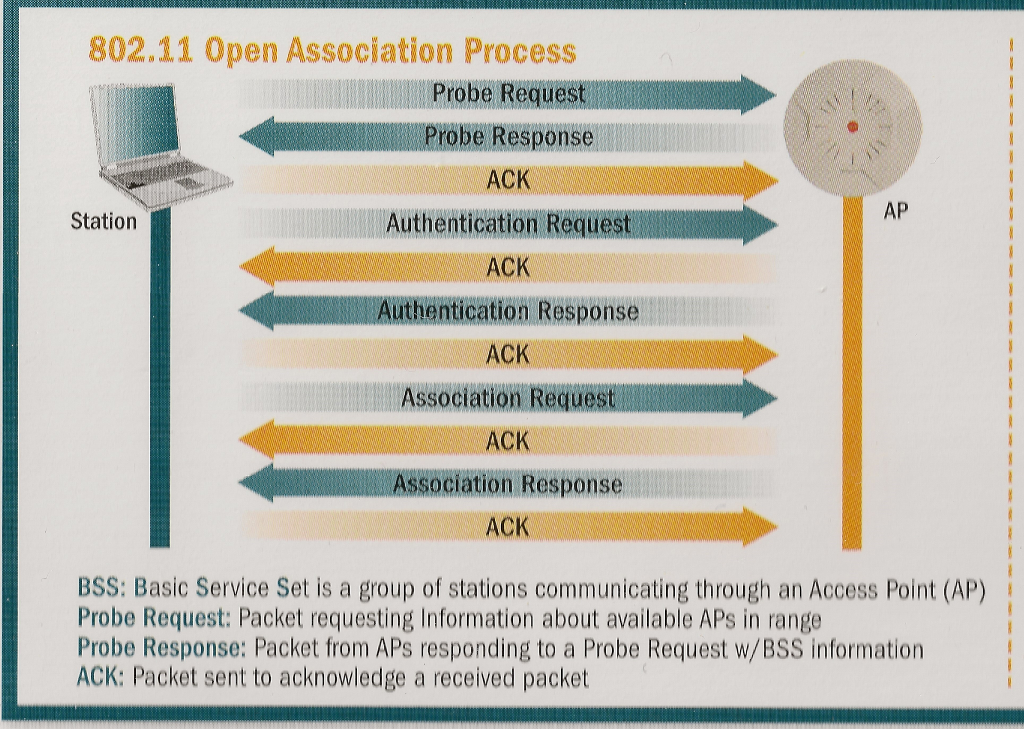
NEED HELP WITH Wireless Security QUESTIONS
1. Which of the following would best address Social Engineering attacks? a. Better firewalls b. Reverse Proxy servers c. Improved virus protection d. User training 2. Which is a common source of information that could be used to learn about your organization's executives? a. A packet analyzer b. Google.com c. An application layer analyzer d. NetStumbler 3. In an ESS wireless environment which makes the decision as to when to roam? a. The STA b. The AP c. Both the STA and AF d. Stations don't roam in an ESS environment
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


