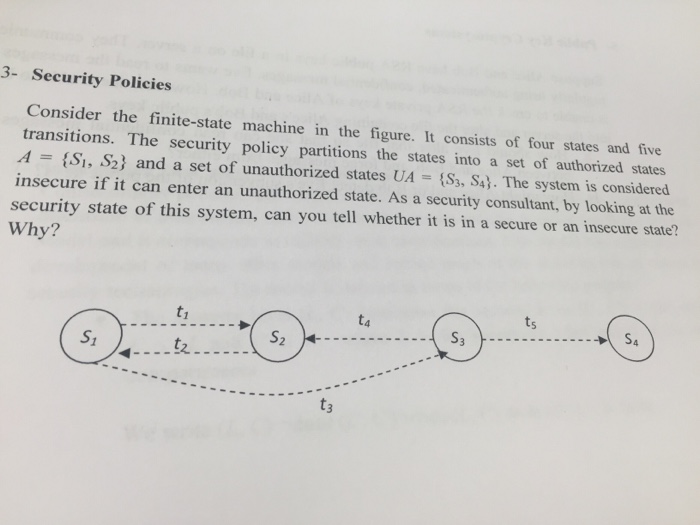
Question: Figure 4-1 A simple finite state machine .In this example ,the authorized states are s1 and s2. In Figure 4-1 .suppose that edge t3 went
| Figure 4-1 A simple finite state machine .In this example ,the authorized states are s1 and s2. In Figure 4-1 .suppose that edge t3 went from s1 to s4. Would the resulting system be secure
|
3- Security Policies Consider the finite-state machine in the figure. It consists of four states and five transitions. The security policy partitions the states into a set of authorized states AA (SI, S2) and a set of unauthorized states UA tS3, Sl. The system is considered insecure if it can enter an unauthorized state. As a security consultant, by looking at the security state of this system, can you tell whether it is in a secure or an insecure state? Why
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts