Question: File 2 File 3 1. Given the following access control model File 1 Read Read Jack Write Write Own Read Write Ali Write Own A.
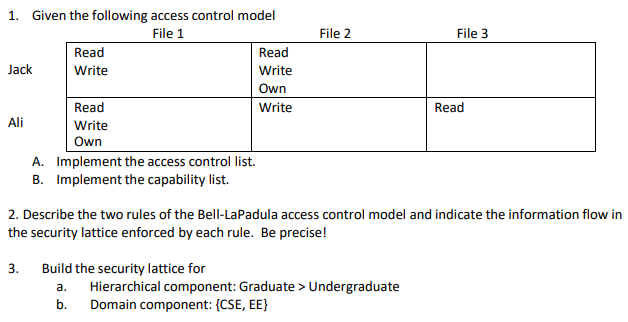
File 2 File 3 1. Given the following access control model File 1 Read Read Jack Write Write Own Read Write Ali Write Own A. Implement the access control list. B. Implement the capability list. Read 2. Describe the two rules of the Bell-LaPadula access control model and indicate the information flow in the security lattice enforced by each rule. Be precise! 3. Build the security lattice for Hierarchical component: Graduate > Undergraduate b. Domain component: CSE, EE} a
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


