Question: Final Project Instructions Name: Your employer, TonTon Tech, recently experienced a data security incident that took down its network. TonTon Tech hired an outside forensic



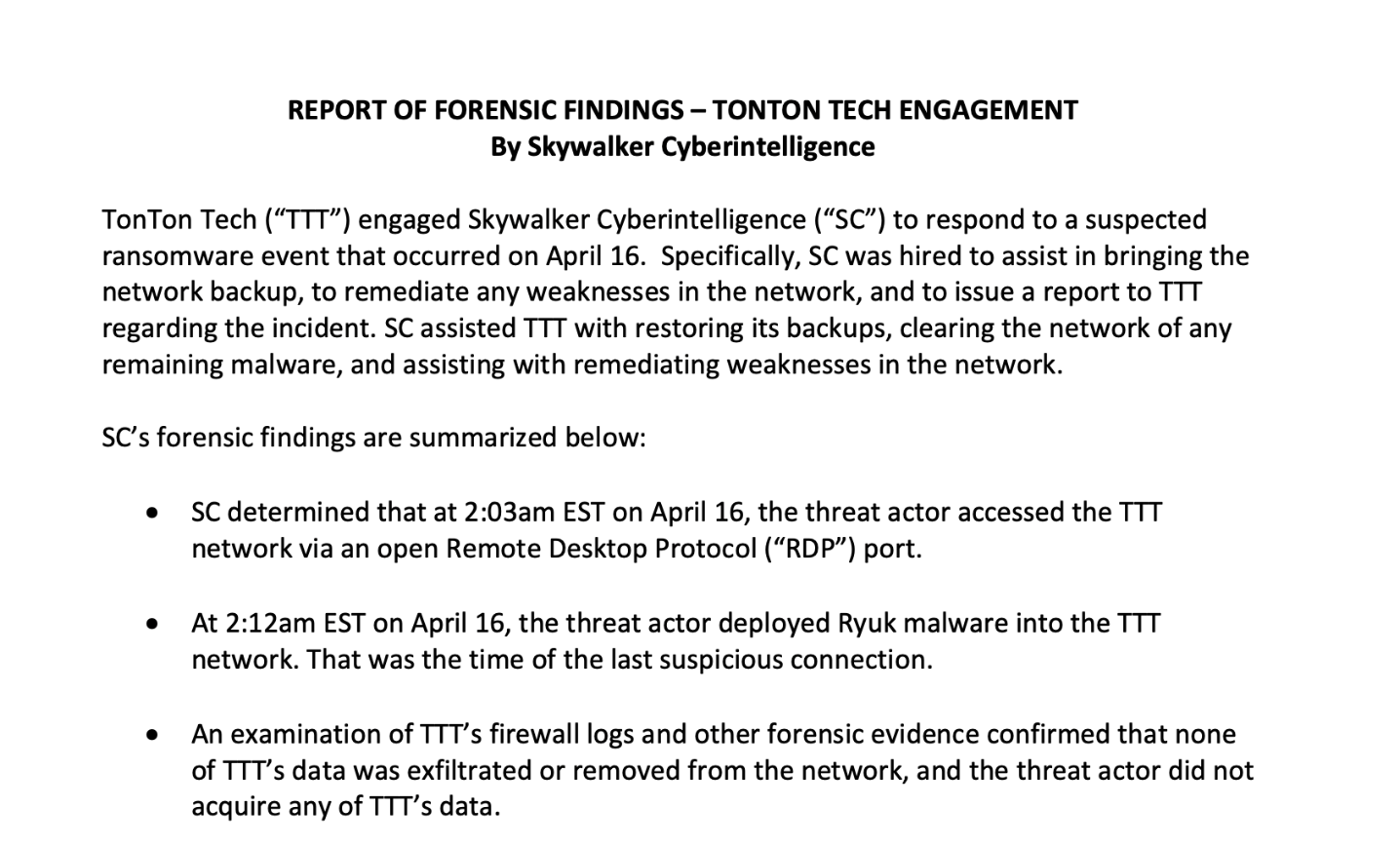
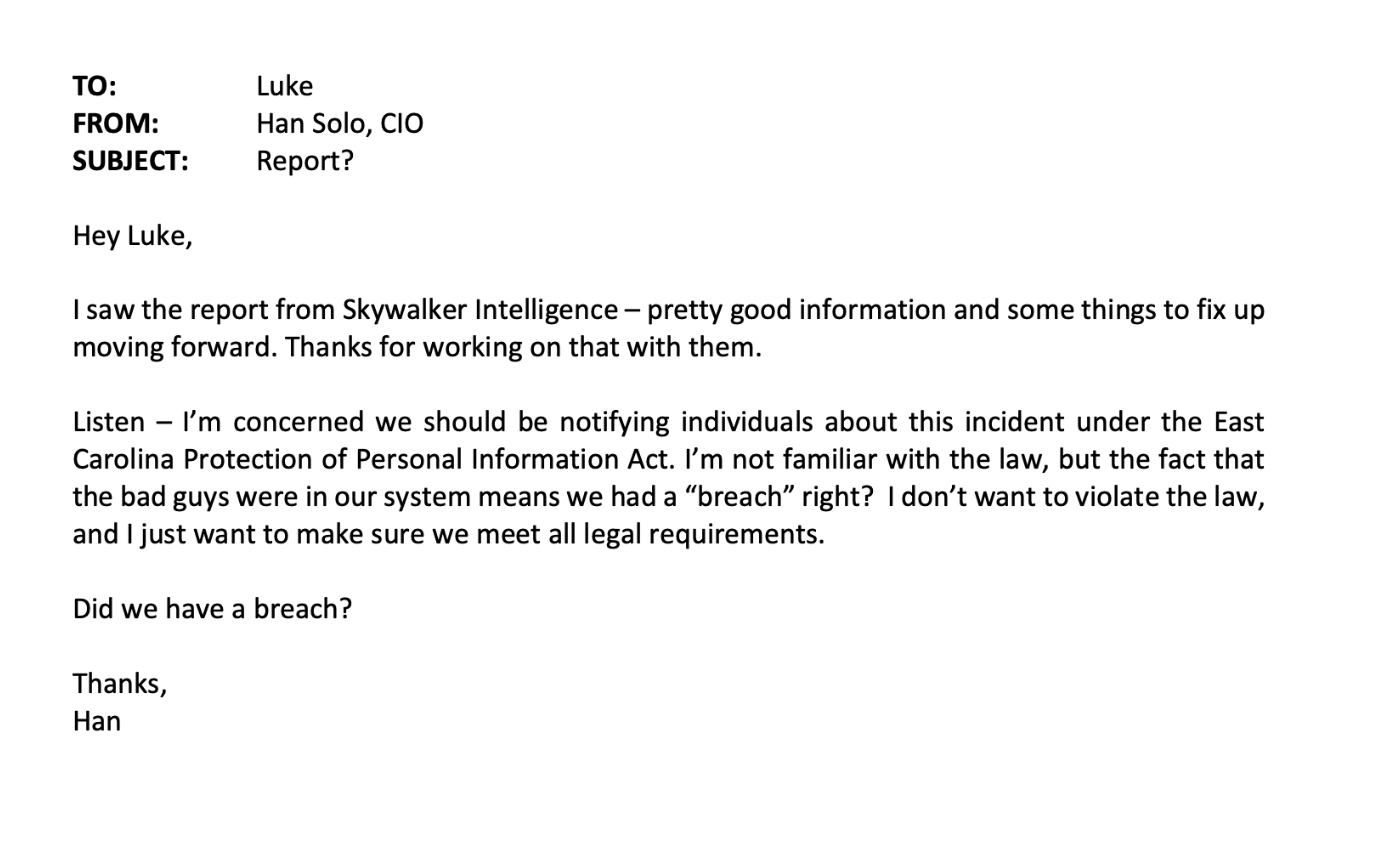
Final Project Instructions Name: Your employer, TonTon Tech, recently experienced a data security incident that took down its network. TonTon Tech hired an outside forensic firm to assist with bringing the network backup, to remediate any weaknesses in the network, and to issue a report to TonTon Tech regarding the incident. The General Counsel requires your assistance in determining the scope of the incident and responding appropriately. Review the materials in the case file and answer the following questions. 1. Review the summary email that you received from the IT employee, Leia Organa, describing the incident. Draft a fact summary of the legally relevant facts for the General Counsel at TonTon Tech. 2. The General Counsel pulled the statute that could potentially apply to the situation and sent it to you for your review. Under East Carolina law, individuals must be notified in the event of a "breach of the security of a system.\" Review the statute defining a "breach of the security of a system.\" Is the applicable rule an elemental test or a factor test? Please list the elements or factors. 3. The General Counsel has had a busy day at the moisture farm and needs you to take a preliminary look at the forensic report and provide an analysis as to whether there was a "breach of the security of the system.\" Review the forensic report from Skywalker Cyberintelligence. and apply the rule for a \"breach" to the findings of the report. Draft a brief legal analysis in IRAC form, concluding whether there was a \"breach of security of the system\" at TonTon Tech. 4. Review the email from Han Solo, Chief Information Officer. Draft an appropriate and persuasive response. Utilize the IRAC analysis from #3 in your response, as well as the legislative history for the applicable statute. TO: Luke FROM: Leia Organa, |T SUBJECT: Incident Hi Luke: Hope you're doing well! The General Counsel asked me to send over a summary of what happened earlier this week. It's been totally crazy! Here's what I remember. I came into the office at 7 am and saw that my computer screen was dark. Usually I don't leave it dark like that, | just let it sit so you usually see the lock screen. I also had some trouble turning it on. I called up to Han, the CIO, and told him that I wasn't able to access my computer normally. Once it came up and started running, there was a note sitting on my desktop titled \"READ ME" and it said something like we needed to contact a group to decrypt our data, and that they would require payment. Han told me that he suspected sometime the night before, the night of April 15th to the 16'\EAST CAROLINA PROTECTION OF PERSONAL INFORMATION ACT (in relevant pa rt) E.C. Stat. 72-4: (2) A "breach of the security of the system\" or \"breach\" is the unauthorized acquisition or exfiltration of unencrypted and unredacted personal information maintained by an entity. LEGISLATIVE HISTORY OF THE EAST CAROLINA PROTECTION OF PERSONAL INFORMATION ACT, including E.C. Sta. 72-4: The East Carolina Protection of Personal Information Act (the \"Act") was introduced by East Carolina Senator Lando Calrissian. The purpose of the Act is to require companies to notify East Carolina residents in the event that there is a breach of the security of the system involving their information. Senator Calrissian's main concern when drafting the Act was cybersecurity events in which personal information was exfiltrated, or removed from, the network. "Too many compromises occur in which information is taken from the systems of East Carolina companies, and I want to make sure that East Carolina citizens are aware of those types of situations," said Senator Calrissian. REPORT OF FORENSIC FINDINGS - TONTON TECH ENGAGEMENT By Skywalker Cyberintelligence TonTon Tech ("TTT") engaged Skywalker Cyberintelligence ("SC") to respond to a suspected ransomware event that occurred on April 16. Specifically, SC was hired to assist in bringing the network backup, to remediate any weaknesses in the network, and to issue a report to TTT regarding the incident. SC assisted TTT with restoring its backups, clearing the network of any remaining malware, and assisting with remediating weaknesses in the network. SC's forensic findings are summarized below: . SC determined that at 2:03am EST on April 16, the threat actor accessed the TTT network via an open Remote Desktop Protocol ("RDP") port. . At 2:12am EST on April 16, the threat actor deployed Ryuk malware into the TTT network. That was the time of the last suspicious connection. . An examination of TTT's firewall logs and other forensic evidence confirmed that none of TTT's data was exfiltrated or removed from the network, and the threat actor did not acquire any of TTT's data.T0: Luke FROM: Han Solo, CIO SUBJECT: Report? Hey Luke, I saw the report from Skywalker Intelligence pretty good information and some things to fix up moving forward. Thanks for working on that with them. Listen I'm concerned we should be notifying individuals about this incident under the East Carolina Protection of Personal Information Act. I'm not familiar with the law, but the fact that the bad guys were in our system means we had a \"breach\" right? Idon't want to violate the law, and | just want to make sure we meet all legal requirements. Did we have a breach? Thanks, Han
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


