Question: for q3 its both first and second pic. thank you ES QUESTIONS And Date .nantander Question Completion Status: as a firewall between a honeypot and


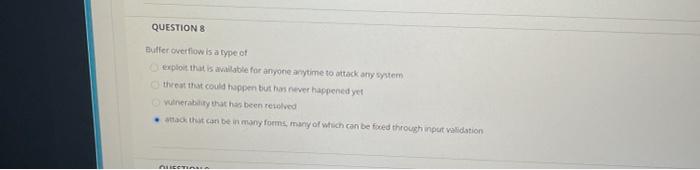
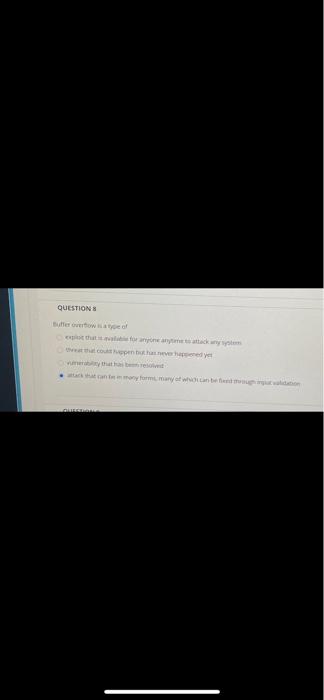


ES QUESTIONS And Date .nantander Question Completion Status: as a firewall between a honeypot and a production network. as a way to attract attacks and collect information about them. keep attackers out of their organization's networks as intrusion prevention system (IPS). QUESTIONS Buffer overflow is a type of exploit that is able for anyone anytime to attack any system threat that could happen but has never happened yet Vulnerability that has been resolved attack that can be in many forms, many of which can be fored through input validation TE QUESTIONS Butterwowane QUESTION 3 An organization deploys a demilitarized zone (DMZ) in order to as a firewall between a honeypot and a production network. as a way to attract attacks and collect information about them. Click Save and Submit to save and submit. Click Save All Answers to save as a firewall between a honeypot and a production network. as a way to attract attacks and collect information about them. keep attackers out of their organization's networks as intrusion prevention system (IPS)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


