Question: For this assignment we will attempt to propose a practical process by which uncertainty could be identified within a project. To help give this assignment
For this assignment we will attempt to propose a practical process by which uncertainty could be identified within a project. To help give this assignment context, you can assume that the project we are working on is a Dream House Project with a Work Breakdown Structure (WBS) that is similar to what is shown below:
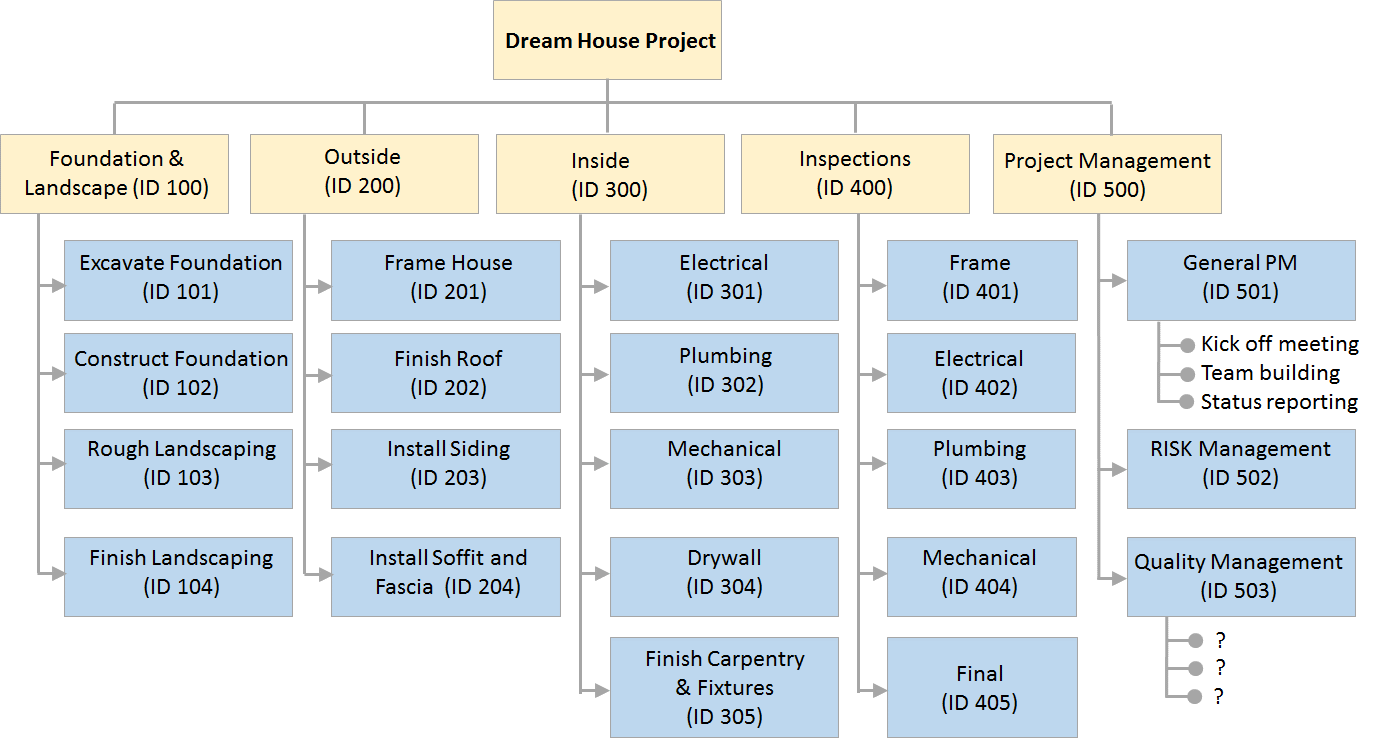
Part 1: Create a Risk Breakdown Structure (RBS) for this project (see Glossary of Terms). Tailor the RBS to the Dream House Project. The RBS can either be done in diagram form (see Glossary of Terms) or in table form (if you dont have access to a diagramming software application).
Part 2 : Develop a risk identification strategy (process) that explains how you would use industry best practices to identify risks (uncertainties) that might be associated with this project. Consider how you might use the risk identification techniques found in the Glossary of Terms in developing this process.
Select two different risk identification tools and techniques (see Glossary of Terms)and explain how you could practically use them on a Dream House construction project to identify project uncertainty (risks).
Part 3: Provide two practical examples of uncertainty that might exist on this project. Specify what risk identification tool might have allowed you to uncover this type of uncertainty.
Part 4 : Understanding Threat Strategies
Consider the following scenario - prior to starting your construction project, you have been offered a contract to demolish (tear down) the old and condemned building that is currently in the location where your project plans to build.
While you are considering accepting this new (and separate) contract to demolish the old building, you are concerned that there might be a risk that asbestos is in the building. If your workers are exposed to asbestos, there is a possibility that they could develop lung cancer, potentially even years after the project is over.
Your team lacks the proper disposal tools and necessary training to deal with hazardous material like asbestos. You are worried that, if asbestos is found and that if your untrained and ill-equipped workers are the ones who clean it up, then your company could be liable for health problems that the workers might encounter years in the future. If this were to happen, then these lawsuits have the potential to bankrupt your company.
What do you do? How do you handle this risk?
Study the various threat strategies outlined in the Glossary of Terms and then specify (in a short sentence or two) (1) how you could use each of the following four strategies for addressing this potential risk, and (2) what you think would be the most viable risk management strategy for this scenario.
Threat strategies: Acceptance, transfer, avoidance, mitigation
GLOSSARY OF TERMS: Use / demonstrate the following terms in this assignment:
RISK IDENTIFICATION METHODS
- Assumption and constraint analysis: Every project and its project management plan are conceived and developed based on a set of assumptions and within a series of constraints. These are often incorporated in the scope baseline and project estimates. Assumptions and constraint analysis explores the validity of assumptions and constraints to determine which pose a risk to the project.
- Uncertainty within the plan may be identified from the inaccuracy, instability, inconsistency, or incompleteness of assumptions. Essentially, your projects assumptions might be invalid.
- Constraints may give rise to opportunities through removing or replacing a limiting factor that affects the execution of the project.
- Expert judgment: Experts are individuals or groups with specialized knowledge of similar projects or business areas. Such experts should be identified by the project manager and invited to consider all aspects of individual project risks as well as sources of overall project risk, based on their previous experience and areas of expertise. The experts bias should be taken into account in this process.
- SWOT analysis: This technique examines the project from perspectives of its Strengths, Weaknesses, Opportunities and Threats (SWOT). For risk identification, it is used to increase the breadth of identified risks by including internally generated risks.
- A SWOT analysis identifies opportunities for the project that may arise from strengths and any threats resulting from weaknesses.
- The analysis also examines the degree to which organizational strengths may offset threats, and determine if weaknesses might hinder opportunities.
- Brainstorming: The goal of brainstorming is to obtain a comprehensive list of individual project risks and sources of overall project risk. The project team usually performs brainstorming, often with a multidisciplinary set of experts who are not part of the project team. Ideas are generated under the guidance of the facilitator, either in a free-form session or one that uses more structured techniques.
- Interviews: Individual project risks and sources of overall project risk can be identified by interviewing experienced project participants, stakeholders and subject matter experts.
- Checklists: A checklist is a list of items, actions, or points to be considered. It is often used as a reminder. Risk checklists are developed based on historical information and knowledge that has been accumulated from similar projects and from other sources of information. They are an effective way to capture lessons learned from similar completed projects, listing specific individual project risks that have occurred previously and that may be relevant to this project. The organization may maintain a risk checklist based on its own completed projects or may use generic risk checklists from industry. While a checklist may be quick and simple to use, it is impossible to build an exhaustive one, and care should be taken to ensure that the checklist is not used to avoid the effort of proper risk identification.
- Root cause analysis: Root cause analysis is typically used to discover the underlying causes that lead to problems, and to develop preventive actions. It can be used to identify threats by starting with a problem and exploring which threats might result in that problem occurring.
- Document analysis: Risks may be identified from a structured review of project documents, including (but not limited to) plans, assumptions, constraints, previous project files, contracts, agreements and technical documentation. Uncertainty in project documents, as well as inconsistencies within a document or between different documents, may be indicators of risk on the project.
RISK: An uncertain event or condition that, if it occurs, has a positive or negative effect on one or more project objectives. Projects frequently encounter uncertainty due to their underlying assumptions, estimates or dependencies.
Risk strategy specifies what strategy will be used to address the risk. For example:
- Avoid risk: The risk is eliminated to protect the project from its impact.
- Reduce or mitigate risk: Actions are taken to reduce the probability or impact of a risk.
- Transfer risk: Risk is transferred to a new owner (a 3rd party).
- Accept risk: Risk is acknowledged, but no proactive action is taken.
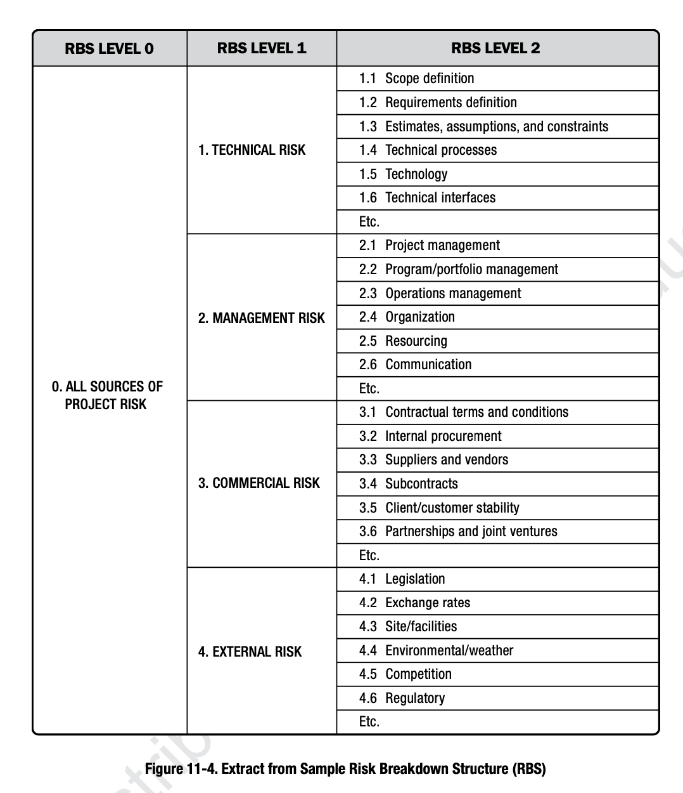
| Risk Breakdown Structure: Provides a means for grouping individual project risk sources. A common way to structure risk categories is with a risk breakdown structure (RBS), which is a hierarchical representation of potential sources of risks on the project. |
Risk breakdown structure (PMBOK Guide, 6th edition) |
\begin{tabular}{|c|c|c|} \hline RBS LEVEL 0 & RBS LEVEL 1 & RBS LEVEL 2 \\ \hline \multirow{28}{*}{0.ALLSOURCESOFPROJECTRISK} & \multirow{7}{*}{ 1. TECHNICAL RISK } & 1.1 Scope definition \\ \hline & & 1.2 Requirements definition \\ \hline & & 1.3 Estimates, assumptions, and constraints \\ \hline & & 1.4 Technical processes \\ \hline & & 1.5 Technology \\ \hline & & 1.6 Technical interfaces \\ \hline & & Etc. \\ \hline & \multirow{7}{*}{ 2. MANAGEMENT RISK } & 2.1 Project management \\ \hline & & 2.2 Program/portfolio management \\ \hline & & 2.3 Operations management \\ \hline & & 2.4 Organization \\ \hline & & 2.5 Resourcing \\ \hline & & 2.6 Communication \\ \hline & & Etc. \\ \hline & \multirow{7}{*}{ 3. COMMERCIAL RISK } & 3.1 Contractual terms and conditions \\ \hline & & 3.2 Internal procurement \\ \hline & & 3.3 Suppliers and vendors \\ \hline & & 3.4 Subcontracts \\ \hline & & 3.5 Client/customer stability \\ \hline & & 3.6 Partnerships and joint ventures \\ \hline & & Etc. \\ \hline & \multirow{7}{*}{ 4. EXTERNAL RISK } & 4.1 Legislation \\ \hline & & 4.2 Exchange rates \\ \hline & & 4.3 Site/facilities \\ \hline & & 4.4 Environmental/weather \\ \hline & & 4.5 Competition \\ \hline & & 4.6 Regulatory \\ \hline & & Etc. \\ \hline \end{tabular} Figure 11-4. Extract from Sample Risk Breakdown Structure (RBS)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts