Question: For this problem, let's suppose that instead of using a simple monoalphabetic substitution cipher (MSC), I decided to be more creative and use two such
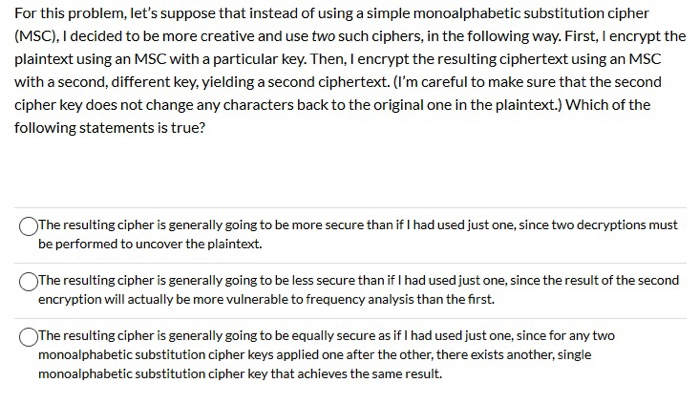
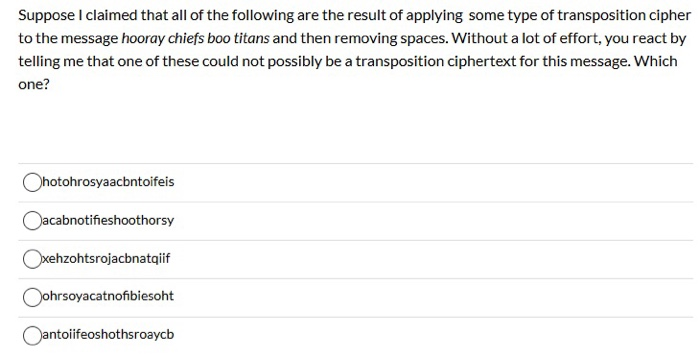
For this problem, let's suppose that instead of using a simple monoalphabetic substitution cipher (MSC), I decided to be more creative and use two such ciphers, in the following way. First, I encrypt the plaintext using an MSC with a particular key. Then, I encrypt the resulting ciphertext using an MSC with a second, different key, yielding a second ciphertext. (I'm careful to make sure that the second cipher key does not change any characters back to the original one in the plaintext.) Which of the following statements is true? The resulting cipher is generally going to be more secure than if I had used just one, since two decryptions must be performed to uncover the plaintext. The resulting cipher is generally going to be less secure than if I had used just one, since the result of the second encryption will actually be more vulnerable to frequency analysis than the first. The resulting cipher is generally going to be equally secure as if I had used just one, since for any two monoalphabetic substitution cipher keys applied one after the other, there exists another, single monoalphabetic substitution cipher key that achieves the same result. Suppose I claimed that all of the following are the result of applying some type of transposition cipher to the message hooray chiefs boo titans and then removing spaces. Without a lot of effort, you react by telling me that one of these could not possibly be a transposition ciphertext for this message. Which one? hotohrosyaacbntoifeis acabnotifieshoothorsy xehzohtsrojacbnatqiif ohrsoyacatnofibiesoht antoiifeoshothsroaycb
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


