Question: From a Windows client, what would you type to map a drive lettter K to a server called SRV-01 and a network share called TopSecret?
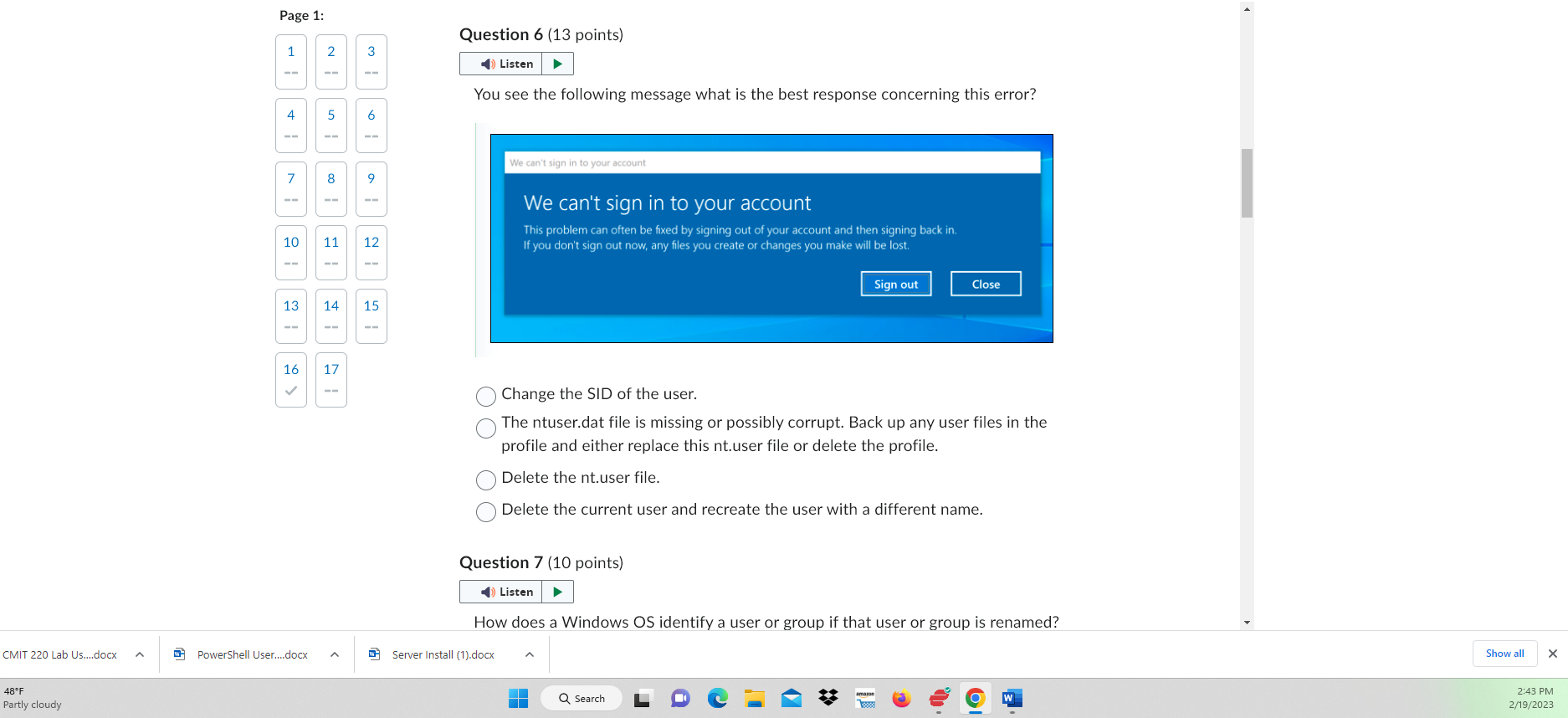
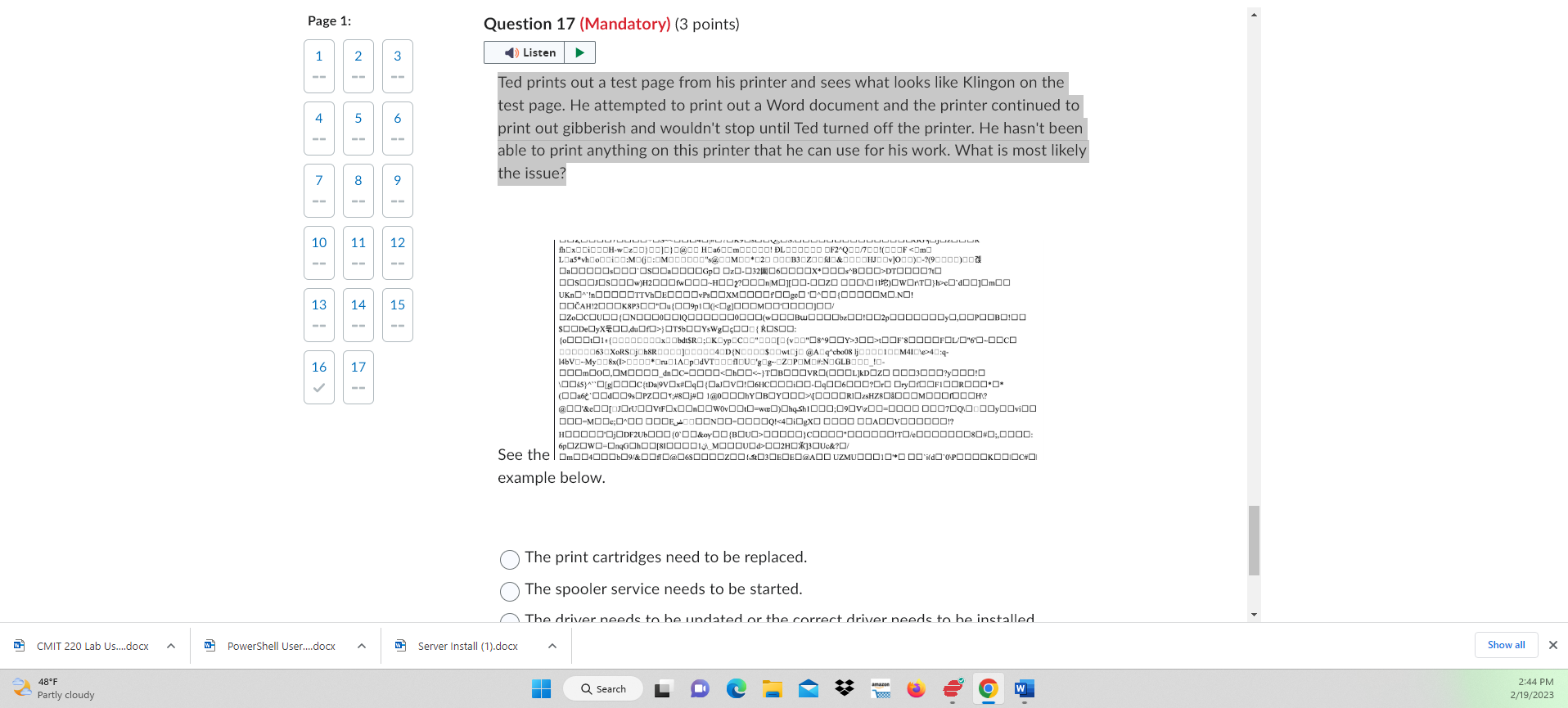
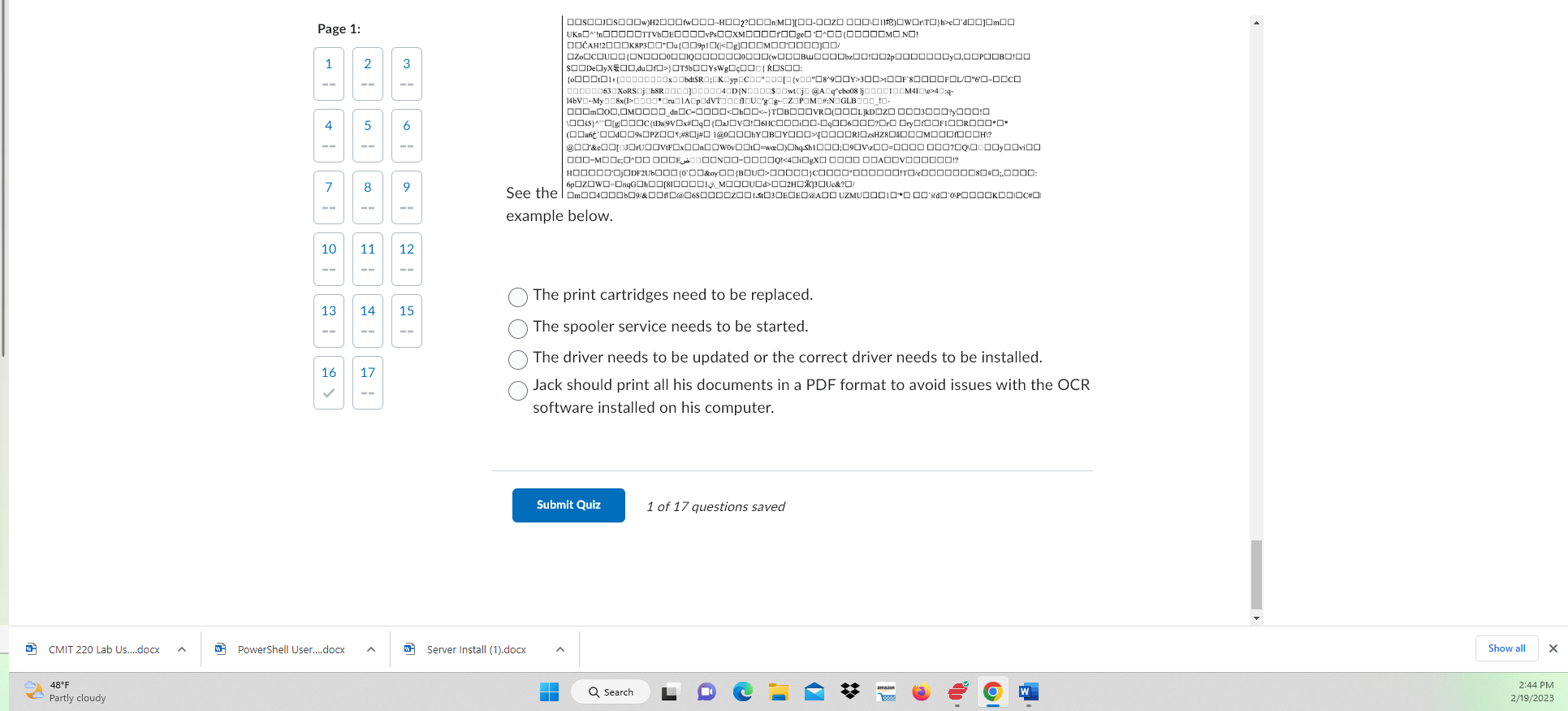
From a Windows client, what would you type to map a drive lettter K to a server called SRV-01 and a network share called TopSecret? net use K:\\SRV01\TopSecret net use K: \SSRV01 TopSecret map K: \\SRV01\ TopSecret net use K: //SRV-01/TopSecret Question 2 (10 points) Which of the following is a SID? 16 180699209-877415012-3182924384-1004 S-1-5-21-1180699209-877415012-3182924384-1004 S-II-81180699209-877415012-3182924384-1004 2000-1180699209-877415012-3182924384-1004 Question 3 (10 points) From a Windows client, how do you connect to a printer on a server called DC-01 and a nrinter ralled HP-NIJRO5? 1 4 From a Windows client, how do you connect to a printer on a server called DC-01 and a printer called HP-NURO5? Install a local printer on the workstation then use the UNC path of \\DC 01 HPNUR05 Use the UNC path of \\DC01\HPNUR05 Use the UNC path of //DC-01/HP-NUR05 Map a drive using the UNC path of DC01 \HPNUR05 Question 4 (Mandatory) (3 points) This software allows for communication between the OS and a device. Question 5 (15 points) Where is your profile stored in a Windows OS? Where is your profile stored in a Windows OS? C:\users\windows C: \ home \ users C:\users\\%username\% C:Iwindows \ system32 Question 6 (13 points) You see the following message what is the best response concerning this error? Page 1: 1 Question 6 (13 points) You see the following message what is the best response concerning this error? 4 13 \begin{tabular}{|l|l} 16 & 17 \\ = \end{tabular} 15 Change the SID of the user. The ntuser.dat file is missing or possibly corrupt. Back up any user files in the profile and either replace this nt.user file or delete the profile. Delete the nt.user file. Delete the current user and recreate the user with a different name. Delete the current user and recreate the user with a different name. Question 7 (10 points) How does a Windows OS identify a user or group if that user or group is renamed? The OS identifies the object by the user or group name. The OS identifies the object by the profile. The OS identifies the object by the SID. The OS can't identify objects unless the name renames the same. Question 8 (10 points) Where is the registry stored in Windows? C: \system 32\ config C:\windows \ system 32\ config C: \windows \ system 32\ ini C: \windows \ system 32\ registry The NTUSER.DAT is loaded into the registry when a user logs into the workstation. True False Question 10 (10 points) When is a user account created in a Windows OS? When the account is created a profile is created. It must be created manually when the account is created. The profile is not automatically created. When the user logs off of the Windows OS. The first time a user logs into the Windows OS. Question 11 (Mandatory) (3 points) It has been detected that someone has installed malware that only runs under Ben's profile. You need to remove this from the registry. Select the best answer where this malware most likely is set to run at login. Page 1: It has been detected that someone has installed malware that only runs under Ben's profile. You need to remove this from the registry. Select the best answer where this malware most likely is set to run at login. \begin{tabular}{c|c|c|c} 7 & 8 & 9 \\ & & \end{tabular} HKEY_LOCAL_MACHINEISoftwarelMicrosoftlWindows \ CurrentVersion|Run \begin{tabular}{l|l|l|l} 13 & 14 & 15 & HKEY_LOCAL_MACHINEISoftwarelMicrosoft Windows \ CurrentVersioniRunOnce \end{tabular} HKEY_CURRENT_USERISoftwarelMicrosoftIWindows \ _CrrentVersion \ Run \begin{tabular}{l|l|l|} 16 & 17 \\ & \\ \hline \end{tabular} HKEY_CURRENT_USERISoftwarelMicrosoft Windows I CurrentVersion\RunIRunOnce Question 12 (Mandatory) (3 points) Ryan is creating an image for the company which will be rolled out to all departments. He has been asked to ensure that the company handbook is stored on the desktop for every user who logs into any computer within the enterprise. Ryan uses Microsoft Word to convert the company handbook into a PDF format. He makes a copy of the PDF file and stores this in the following location: Ryan is creating an image for the company which will be rolled out to all departments. He has been asked to ensure that the company handbook is stored on the desktop for every user who logs into any computer within the enterprise. Ryan uses Microsoft Word to convert the company handbook into a PDF format. He makes a copy of the PDF file and stores this in the following location: True False Question 13 (10 points) Registry keys are Select the best answer. values that are located under the instruction hive. files that categorize permissions and settings in the system drive. are folders that hold information or data in several registry hives. All of the answers are correct. Registry keys are Select the best answer. values that are located under the instruction hive. files that categorize permissions and settings in the system drive. are folders that hold information or data in several registry hives. All of the answers are correct. Question 14 (Mandatory) (3 points) Which tool would you use to migrate user data to a new installation of Windows? IMAGEX.EXE Copy the files manually. USMT The answer isn't listed. Question 15 (Mandatory) (3 points) A user has accidentally installed malware on their computer. You need to remove the profile. You go to C:\ users and delete the profile. This action completely removes all data and infarmation ralatad ta tha wear A user has accidentally installed malware on their computer. You need to remove the profile. You go to C:\ \users and delete the profile. This action completely removes all data and information related to the user. True False Question 16 (10 points) Saved Before modifying registry what task should you perform? Run Windows Updates. Reboot the computer. Backup the registry. Delete the administrator's profile. Question 17 (Mandatory) (3 points) Ted prints out a test page from his printer and sees what looks like Klingon on the test page. He attempted to print out a Word document and the printer continued to print out gibberish and wouldn't stop until Ted turned off the printer. He hasn't been Ted prints out a test page from his printer and sees what looks like Klingon on the test page. He attempted to print out a Word document and the printer continued to print out gibberish and wouldn't stop until Ted turned off the printer. He hasn't been able to print anything on this printer that he can use for his work. What is most likely the issue? See the example below. See the example below. The print cartridges need to be replaced. The spooler service needs to be started. The driver needs to be updated or the correct driver needs to be installed. Jack should print all his documents in a PDF format to avoid issues with the OCR software installed on his computer
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


