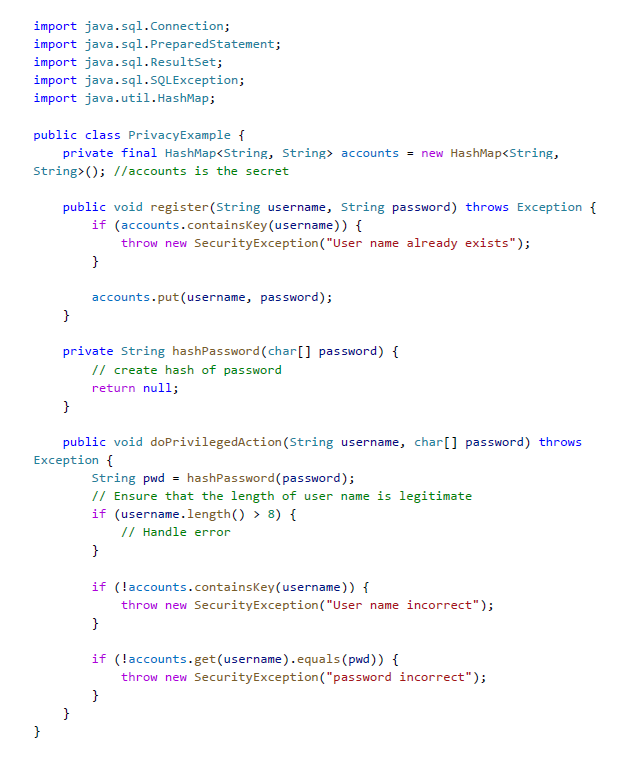
Question: Given PrivacyExample.java, assume that whatever in accounts are secret (or privacy) and assume that the attacker is able to monitor whether some exception has been
Given PrivacyExample.java, assume that whatever in accounts are secret (or privacy) and assume that the attacker is able to monitor whether some exception has been thrown.
Is there any information leakage in doPrivilegedAction()? Explain how taint analysis is used to derive the answer..
import java.sql.Connection;
import java.sql.PreparedStatement;
import java.sql.ResultSet;
import java.sql.SQLException;
import java.util.HashMap;
public class PrivacyExample {
private final HashMap
public void register(String username, String password) throws Exception {
if (accounts.containsKey(username)) {
throw new SecurityException("User name already exists");
}
accounts.put(username, password);
}
private String hashPassword(char[] password) {
// create hash of password
return null;
}
public void doPrivilegedAction(String username, char[] password) throws Exception {
String pwd = hashPassword(password);
// Ensure that the length of user name is legitimate
if (username.length() > 8) {
// Handle error
}
if (!accounts.containsKey(username)) {
throw new SecurityException("User name incorrect");
}
if (!accounts.get(username).equals(pwd)) {
throw new SecurityException("password incorrect");
}
}
}
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


