Question: Given the risks assessment results listed in the table in Section 5. Construct a risk register, adding the risk response column and populate with what
Given the risks assessment results listed in the table in Section 5. Construct a risk register, adding the risk response column and populate with what you think is an appropriate risk response action (e.g. accept, mitigate, etc.)
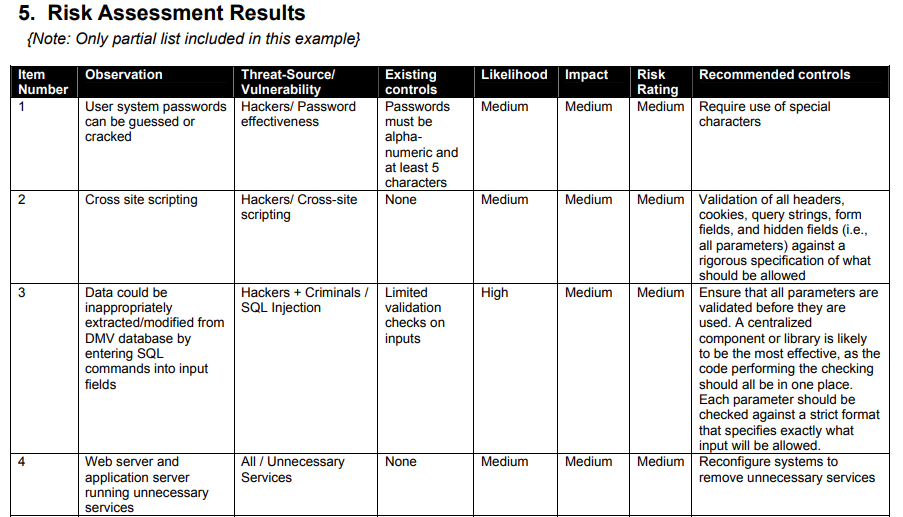

5. Risk Assessment Results {Note: Only partial list included in this example} Likelihood Impact Item Number 1 Observation Threat-Source Vulnerability User system passwords Hackers/ Password can be guessed or effectiveness cracked Risk Recommended controls Rating Medium Require use of special characters Medium Medium Existing controls Passwords must be alpha- numeric and at least 5 characters None N Cross site scripting Hackers/ Cross-site scripting Medium Medium 3 High Medium Data could be inappropriately extracted/modified from DMV database by entering SQL commands into input fields Hackers + Criminals / Limited SQL Injection validation checks on inputs Medium Validation of all headers, cookies, query strings, form fields, and hidden fields (i.e., all parameters) against a rigorous specification of what should be allowed Medium Ensure that all parameters are validated before they are used. A centralized component or library is likely to be the most effective, as the code performing the checking should all be in one place. Each parameter should be checked against a strict format that specifies exactly what input will be allowed. Medium Reconfigure systems to remove unnecessary services 4 None All / Unnecessary Services Medium Medium Web server and application server running unnecessary services Observation Likelihood Impact Item Number 5 Threat-Sourcel Vulnerability Environment / Disaster Recovery Existing controls Weekly backup only Medium Risk Recommended controls Rating Medium Develop and test a disaster recovery plan Disaster recovery plan has not been established High 5. Risk Assessment Results {Note: Only partial list included in this example} Likelihood Impact Item Number 1 Observation Threat-Source Vulnerability User system passwords Hackers/ Password can be guessed or effectiveness cracked Risk Recommended controls Rating Medium Require use of special characters Medium Medium Existing controls Passwords must be alpha- numeric and at least 5 characters None N Cross site scripting Hackers/ Cross-site scripting Medium Medium 3 High Medium Data could be inappropriately extracted/modified from DMV database by entering SQL commands into input fields Hackers + Criminals / Limited SQL Injection validation checks on inputs Medium Validation of all headers, cookies, query strings, form fields, and hidden fields (i.e., all parameters) against a rigorous specification of what should be allowed Medium Ensure that all parameters are validated before they are used. A centralized component or library is likely to be the most effective, as the code performing the checking should all be in one place. Each parameter should be checked against a strict format that specifies exactly what input will be allowed. Medium Reconfigure systems to remove unnecessary services 4 None All / Unnecessary Services Medium Medium Web server and application server running unnecessary services Observation Likelihood Impact Item Number 5 Threat-Sourcel Vulnerability Environment / Disaster Recovery Existing controls Weekly backup only Medium Risk Recommended controls Rating Medium Develop and test a disaster recovery plan Disaster recovery plan has not been established High
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


