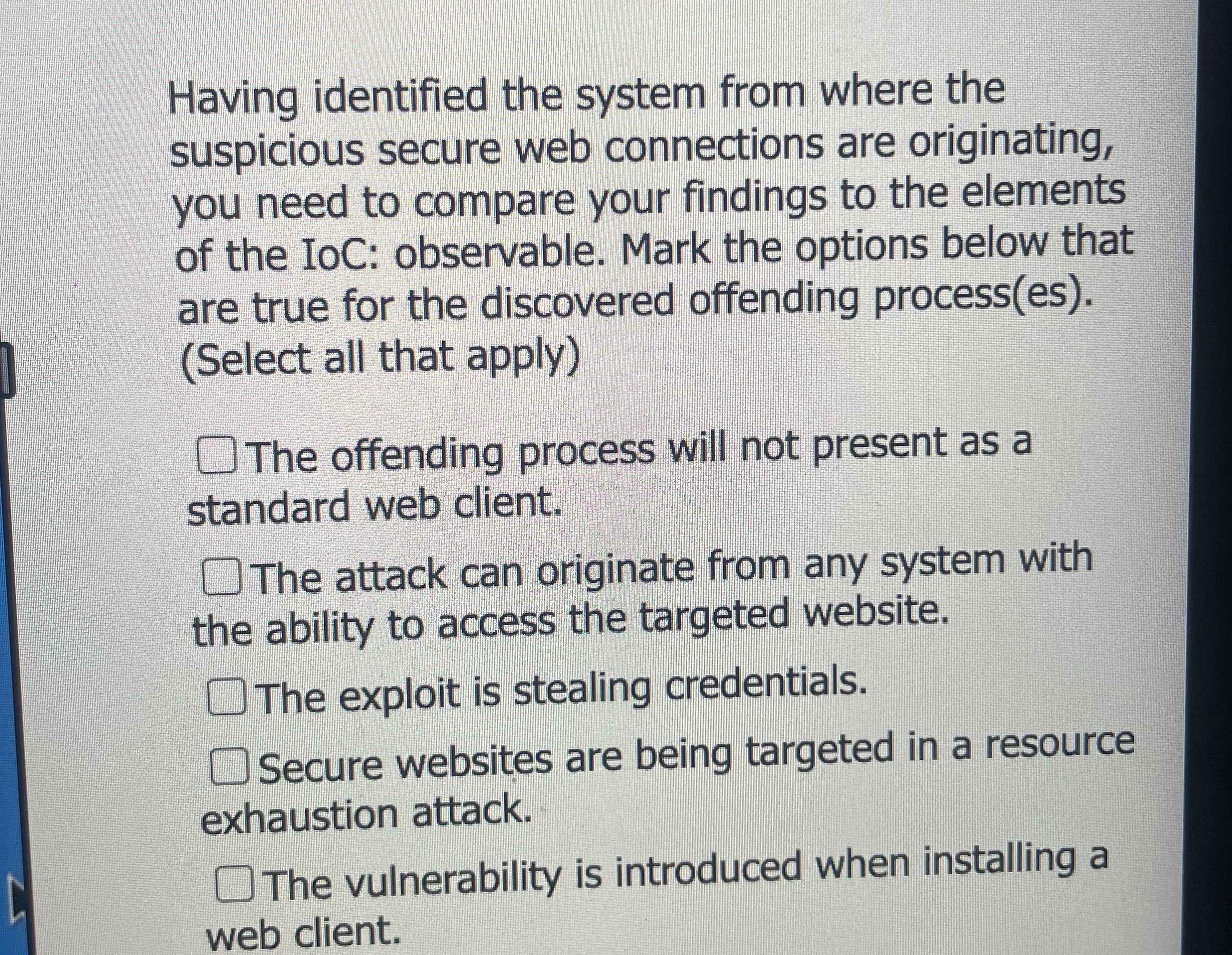
Question: Having identified the system from where the suspicious secure web connections are originating, you need to compare your findings to the elements of the IoC:
Having identified the system from where the
suspicious secure web connections are originating,
you need to compare your findings to the elements
of the IoC: observable. Mark the options below that
are true for the discovered offending processes
Select all that apply
The offending process will not present as a
standard web client.
The attack can originate from any system with
the ability to access the targeted website.
The exploit is stealing credentials.
Secure websites are being targeted in a resource
exhaustion attack.
The vulnerability is introduced when installing a
web client.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


