Question: having some trouble on question 2 please help The likelihood reters to the probability of a successful attack. This often comes down to the number
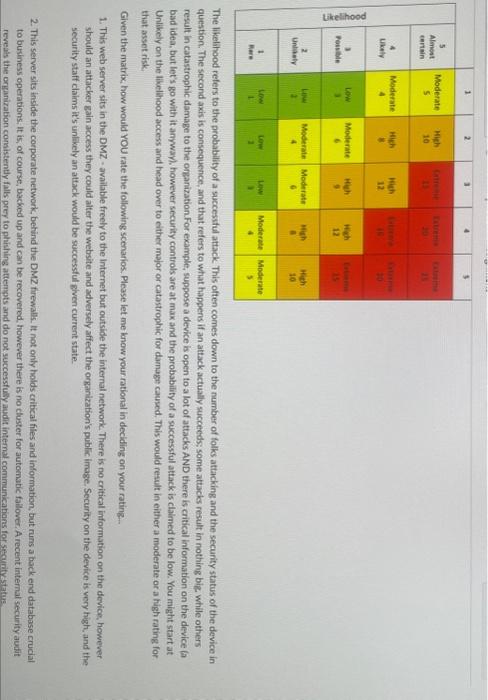
The likelihood reters to the probability of a successful attack. This often comes down to the number of folks attacking and the security status of the device in question. The second axis is consequence, and that refers to what happens if an attack actually succeeds some attacks result in nothing big. while others result in catastrophic damage to the organization. For example, suppose a device is open to a lot of attacks AND there is critical information on the device fa bad idea, but lets go with it anyway, however security controls are at max and the probability of a successful attack is claimed to be low. You might start at Unlikely on the likelihood access and head over to either major or catastrophic for damage cawsed. This would result in either a moderate or a high rating for. that asset risk: Given the matrix, how would YoU rate the following scenarios. Please let me know your rational in deciding on your rating. 1. This web server sits in the DMZ - available freely to the internet but outside the internal network. There is no critical information on the device. however should an attacker gain access they could alter the website and adversely affect the organization's public image. Security on the device is very high, and the security staff claims it's unlikely an attack would be successful given current state. 2. This server sits inside the corporate network, behind the DMZ frewalls. It not only halds critical files and information, but runs a back end database crucal to business operations, It is, of course, backed up and can be recovered, however there is no cluster for autornatic fallover. A recent internal security audit reveals the organization comistently falls prey to phishing attempts and do not successtuly audit intemat communications for securitystatus
Step by Step Solution
There are 3 Steps involved in it
To assess the risk for each scenario using the given risk matrix we need to analyze both the likelih... View full answer

Get step-by-step solutions from verified subject matter experts


