Question: Hello, for question 4.1 only what flaws can be identified from the diagram above Many law firms utilize case-tracking systems. Big law firms utilize such
Hello, for question 4.1 only what flaws can be identified from the diagram above
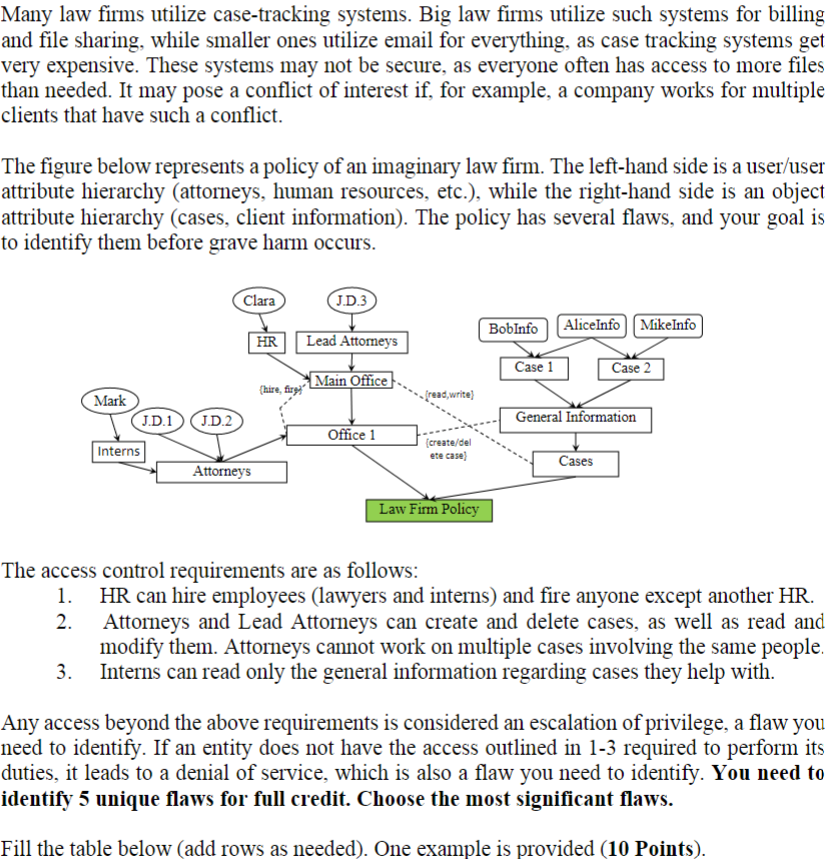
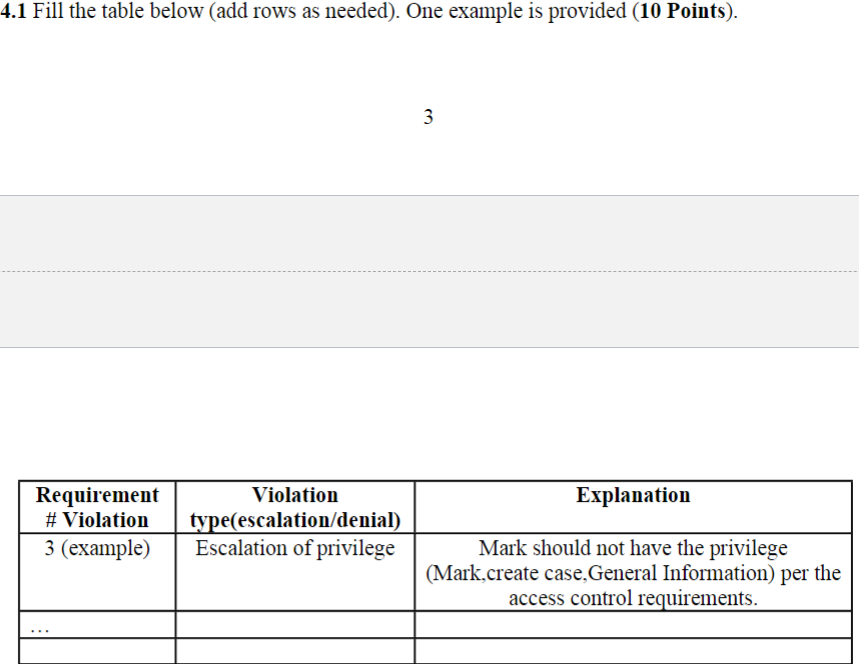
Many law firms utilize case-tracking systems. Big law firms utilize such systems for billing and file sharing, while smaller ones utilize email for everything, as case tracking systems get very expensive. These systems may not be secure, as everyone often has access to more files than needed. It may pose a conflict of interest if, for example, a company works for multiple clients that have such a conflict. The figure below represents a policy of an imaginary law firm. The left-hand side is a user/user attribute hierarchy (attorneys, human resources, etc.), while the right-hand side is an object attribute hierarchy (cases, client information). The policy has several flaws, and your goal is to identify them before grave harm occurs. The access control requirements are as follows: 1. HR can hire employees (lawyers and interns) and fire anyone except another HR. 2. Attorneys and Lead Attorneys can create and delete cases, as well as read and modify them. Attorneys cannot work on multiple cases involving the same people. 3. Interns can read only the general information regarding cases they help with. Any access beyond the above requirements is considered an escalation of privilege, a flaw you need to identify. If an entity does not have the access outlined in 1-3 required to perform its duties, it leads to a denial of service, which is also a flaw you need to identify. You need to identify 5 unique flaws for full credit. Choose the most significant flaws. Fill the table below (add rows as needed). One example is provided (10 Points). 4.1 Fill the table below (add rows as needed). One example is provided (10 Points)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


