Question: Hello I need help answering these 5 questions for Computer Networking Please answer all 5 questions and give a proper response to each part of
Hello I need help answering these 5 questions for Computer Networking
Please answer all 5 questions and give a proper response to each part of each question. Thanks.
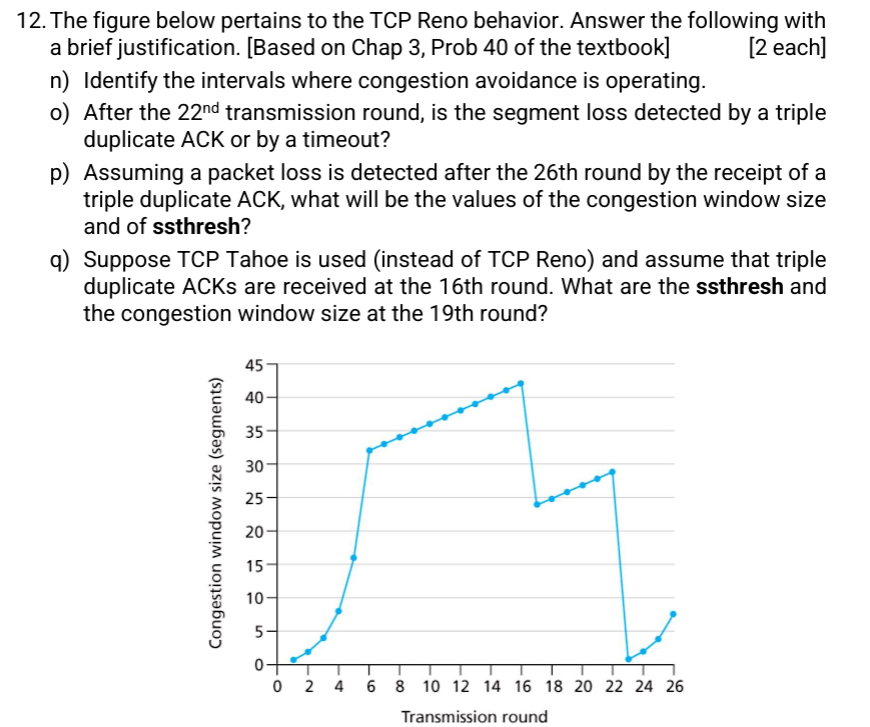
8. To set up a connection, TCP uses a 3-way handshake using segments with the following flags SYN, SYN-ACK and ACK set as required. [20] j) What is the sequence in which these flags are used in the handshake process? k) What feature of TCP handshake makes TCP vulnerable to DoS attack known as SYN flooding? I) During the handshake, the server sends an Initial Sequence Number (ISN) with the SYN-ACK. Why is this number randomly generated? m ) If the attacker can steal a large number of ISNs sent by the server, can the attacker cause server to create many fully open connections by sending ACKs using those ISNs? What can server do to prevent such an attack? 9. Host A sends data segments to B and receives ACKs for correctly received data segments. If the timeout value is large enough such that 5 consecutive data segments can be received by B and their ACKs can be received by A, if none of these are lost. Suppose host A sends 5 segments to B and the 2nd segment is lost. In the next attempt all 5 data segments are correctly received by B. Based on the given information, answer the following for both GBN and SR. [10] a) How many segments does A have to send in all and how many ACKs does B send? b) What are their sequence numbers? 10. The hypothetical data transfer protocol (HDTP) uses only negative ACKs. If you were the sender and transfer data only infrequently, would you prefer HDTP over the normal implementations of TCP that use ACKs? Explain your answer. If you have a lot of data to send and the end-to-end connection experiences few losses. Would you still prefer HDTP? Explain your answer. [10] 12. The figure below pertains to the TCP Reno behavior. Answer the following with a brief justification. [Based on Chap 3, Prob 40 of the textbook] [2 each] n) Identify the intervals where congestion avoidance is operating. o) After the 22nd transmission round, is the segment loss detected by a triple duplicate ACK or by a timeout? p) Assuming a packet loss is detected after the 26th round by the receipt of a triple duplicate ACK, what will be the values of the congestion window size and of ssthresh? q) Suppose TCP Tahoe is used (instead of TCP Reno) and assume that triple duplicate ACKs are received at the 16th round. What are the ssthresh and the congestion window size at the 19th round
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


