Question: help please. actual python code preferred W 6.16 LAB: Cryptographic Hashing Algorithms Encrypting text allows us to encrypt and decrypt the text using a special
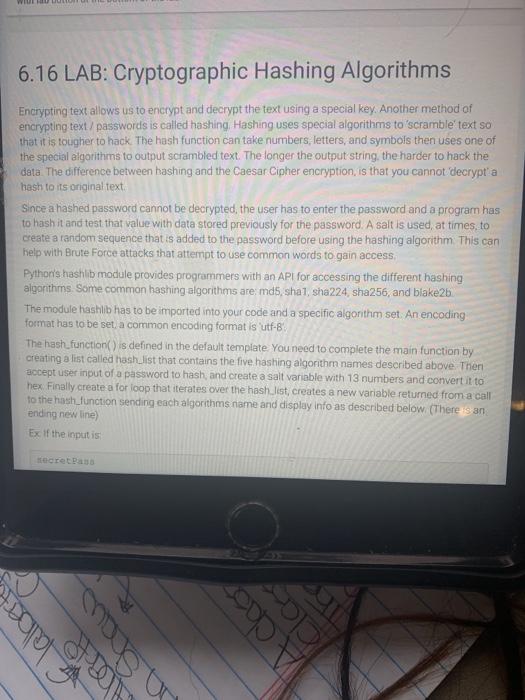
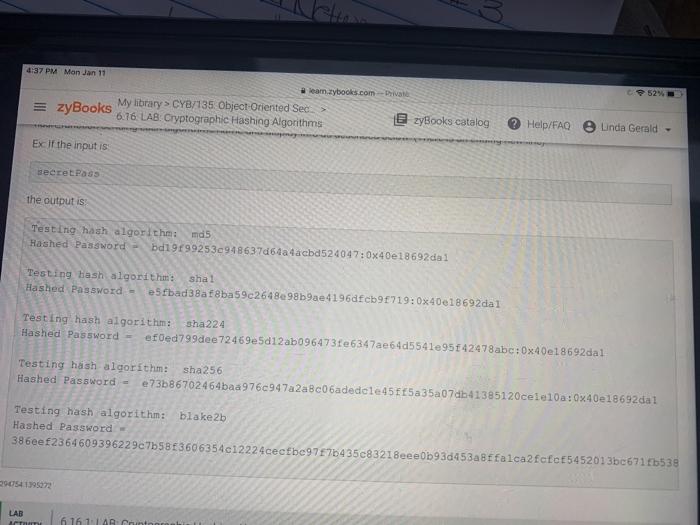
W 6.16 LAB: Cryptographic Hashing Algorithms Encrypting text allows us to encrypt and decrypt the text using a special key. Another method of encrypting text/passwords is called hashing, Hashing uses special algorithms to scramble' text so that it is tougher to hack. The hash function can take numbers, letters, and symbols then uses one of the special algorithms to output scrambled text. The longer the output string the harder to hack the data The difference between hashing and the Caesar Cipher encryption is that you cannot decrypta hash to its original text Since a hashed password cannot be decrypted, the user has to enter the password and a program has to hash it and test that value with data stored previously for the password. A salt is used at times, to create a random sequence that is added to the password before using the hashing algorithm. This can help with Brute Force attacks that attempt to use common words to gain access, Python's hashlib module provides programmers with an API for accessing the different hashing algorithms Some common hashing algorithms are md5, shal, sha224, sha256, and blake2b The module hashlib has to be imported into your code and a specific algorithm set. An encoding format has to be set, a common encoding format is 'utf-8' The hash_function() is defined in the default template You need to complete the main function by creating a list called hash_list that contains the five hashing algorithm names described above. Then accept user input of a password to hash and create a salt variable with 13 numbers and convert it to hex Finally create a for loop that iterates over the hash Jist, creates a new variable retured from a call to the hash_function sending each algorithms name and display info as described below. (There is an ending new line) ExcIf the input is + cho clar for laber in Show 4:37 PM Mon Jan 11 eam.xybooks.com My library > CYB/135 Object Oriented Sec = zyBooks 6.76 LAB Cryptographic Hashing Algorithms 52% zyBooks catalog Help/FAQ e Linda Gerald - Exif the input is secretPass the output is Testing hash algorithms mds Hashed Password bd19199253c948637d64a 4acbd524047:0x40e18692 dal Testing tash algorithm: shal Hashed Password e5fbad 38af8ba59c264898b9ae4196dfcb9719:0x40018692 dal Testing hash algorithm: sha224 Hashed Password ef0ed799dee 72469e5d12ab096473fe6347ae64d5541e95142478abc:0x40e18692dal Testing hash algorithm: sha256 Hashed Password = e73b86702464baa976c947a2a8c06adedcle45165a35a07db41385120 celel0a: 0x40018692da1 Testing hash algorithm: blake2b Hashed Password 386eef2364609396229c76583606354c12224cecfbe97576435c8321 Beee0b93d453a8ffalca2fcfce5452013bc671fb538 2005195272 LAB HT 6.161 LAR W 6.16 LAB: Cryptographic Hashing Algorithms Encrypting text allows us to encrypt and decrypt the text using a special key. Another method of encrypting text/passwords is called hashing, Hashing uses special algorithms to scramble' text so that it is tougher to hack. The hash function can take numbers, letters, and symbols then uses one of the special algorithms to output scrambled text. The longer the output string the harder to hack the data The difference between hashing and the Caesar Cipher encryption is that you cannot decrypta hash to its original text Since a hashed password cannot be decrypted, the user has to enter the password and a program has to hash it and test that value with data stored previously for the password. A salt is used at times, to create a random sequence that is added to the password before using the hashing algorithm. This can help with Brute Force attacks that attempt to use common words to gain access, Python's hashlib module provides programmers with an API for accessing the different hashing algorithms Some common hashing algorithms are md5, shal, sha224, sha256, and blake2b The module hashlib has to be imported into your code and a specific algorithm set. An encoding format has to be set, a common encoding format is 'utf-8' The hash_function() is defined in the default template You need to complete the main function by creating a list called hash_list that contains the five hashing algorithm names described above. Then accept user input of a password to hash and create a salt variable with 13 numbers and convert it to hex Finally create a for loop that iterates over the hash Jist, creates a new variable retured from a call to the hash_function sending each algorithms name and display info as described below. (There is an ending new line) ExcIf the input is + cho clar for laber in Show 4:37 PM Mon Jan 11 eam.xybooks.com My library > CYB/135 Object Oriented Sec = zyBooks 6.76 LAB Cryptographic Hashing Algorithms 52% zyBooks catalog Help/FAQ e Linda Gerald - Exif the input is secretPass the output is Testing hash algorithms mds Hashed Password bd19199253c948637d64a 4acbd524047:0x40e18692 dal Testing tash algorithm: shal Hashed Password e5fbad 38af8ba59c264898b9ae4196dfcb9719:0x40018692 dal Testing hash algorithm: sha224 Hashed Password ef0ed799dee 72469e5d12ab096473fe6347ae64d5541e95142478abc:0x40e18692dal Testing hash algorithm: sha256 Hashed Password = e73b86702464baa976c947a2a8c06adedcle45165a35a07db41385120 celel0a: 0x40018692da1 Testing hash algorithm: blake2b Hashed Password 386eef2364609396229c76583606354c12224cecfbe97576435c8321 Beee0b93d453a8ffalca2fcfce5452013bc671fb538 2005195272 LAB HT 6.161 LAR
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


