Question: How to achive task 1, 2, 3 ? If you review rules found in the /etc/snort/rules directory, you will see that rules have the general
How to achive task 1, 2, 3 ?
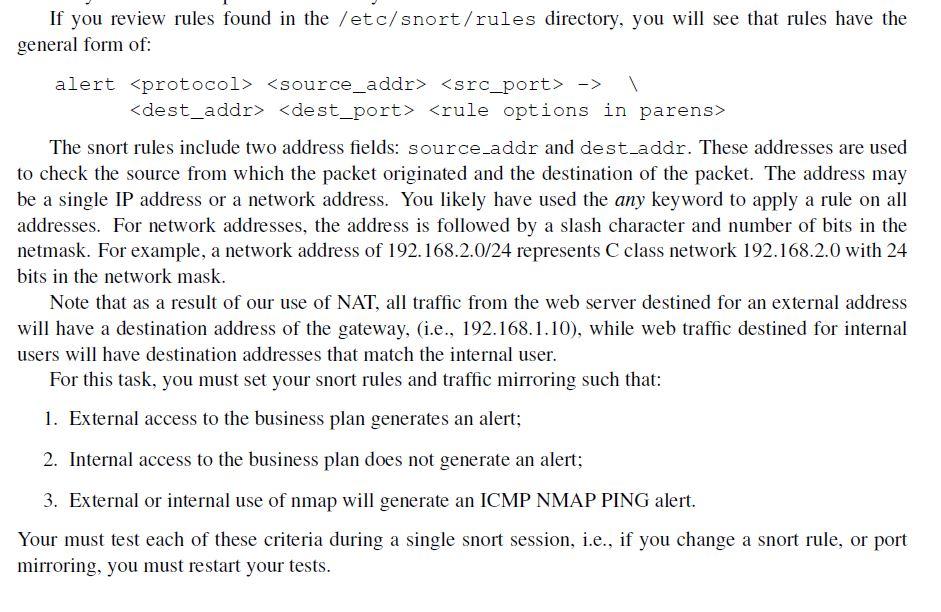
If you review rules found in the /etc/snort/rules directory, you will see that rules have the general form of: alert -> The snort rules include two address fields: source_addr and dest_addr. These addresses are used to check the source from which the packet originated and the destination of the packet. The address may be a single IP address or a network address. You likely have used the any keyword to apply a rule on all addresses. For network addresses, the address is followed by a slash character and number of bits in the netmask. For example, a network address of 192.168.2.0/24 represents C class network 192.168.2.0 with 24 bits in the network mask. Note that as a result of our use of NAT, all traffic from the web server destined for an external address will have a destination address of the gateway, (i.e., 192.168.1.10), while web traffic destined for internal users will have destination addresses that match the internal user. For this task, you must set your snort rules and traffic mirroring such that: 1. External access to the business plan generates an alert; 2. Internal access to the business plan does not generate an alert; 3. External or internal use of nmap will generate an ICMP NMAP PING alert. Your must test each of these criteria during a single snort session, i.e., if you change a snort rule, or port mirroring, you must restart your tests. If you review rules found in the /etc/snort/rules directory, you will see that rules have the general form of: alert -> The snort rules include two address fields: source_addr and dest_addr. These addresses are used to check the source from which the packet originated and the destination of the packet. The address may be a single IP address or a network address. You likely have used the any keyword to apply a rule on all addresses. For network addresses, the address is followed by a slash character and number of bits in the netmask. For example, a network address of 192.168.2.0/24 represents C class network 192.168.2.0 with 24 bits in the network mask. Note that as a result of our use of NAT, all traffic from the web server destined for an external address will have a destination address of the gateway, (i.e., 192.168.1.10), while web traffic destined for internal users will have destination addresses that match the internal user. For this task, you must set your snort rules and traffic mirroring such that: 1. External access to the business plan generates an alert; 2. Internal access to the business plan does not generate an alert; 3. External or internal use of nmap will generate an ICMP NMAP PING alert. Your must test each of these criteria during a single snort session, i.e., if you change a snort rule, or port mirroring, you must restart your tests




