Question: I. Block Chain Irue / False: Blockchains are centralized databases, meaning a central body stores and controls its data. ( ) Bitcoin's blockchain achieves a
I. Block Chain
IrueFalse:
Blockchains are centralized databases, meaning a central body stores and controls its data.
Bitcoin's blockchain achieves a decentralized ledger through a consensus method known as Proofof
Work
A Bitcoin block is divided into the data section transactions and the block header
Multiple Choice:
How is the winner determined in the proofofwork race aka mining
a The participant with the slowest computer
b The participant who accumulates the most Bitcoins
c The participant who finds a nonce that outputs a valid block hash
d The participant who digitally signs all transactions first
How is Bitcoin transaction authenticity accomplished?
a Digital Signatures
b Decentralization
c ProofofWork
d ProofofStake
How is the block hash generated in Bitcoin?
a Hashing all of the transactions on the block using the SHA hash function
b Hashing the digital signatures of each transaction using the SHA hash function
c Hashing only the nonce in each block header using the SHA hash function
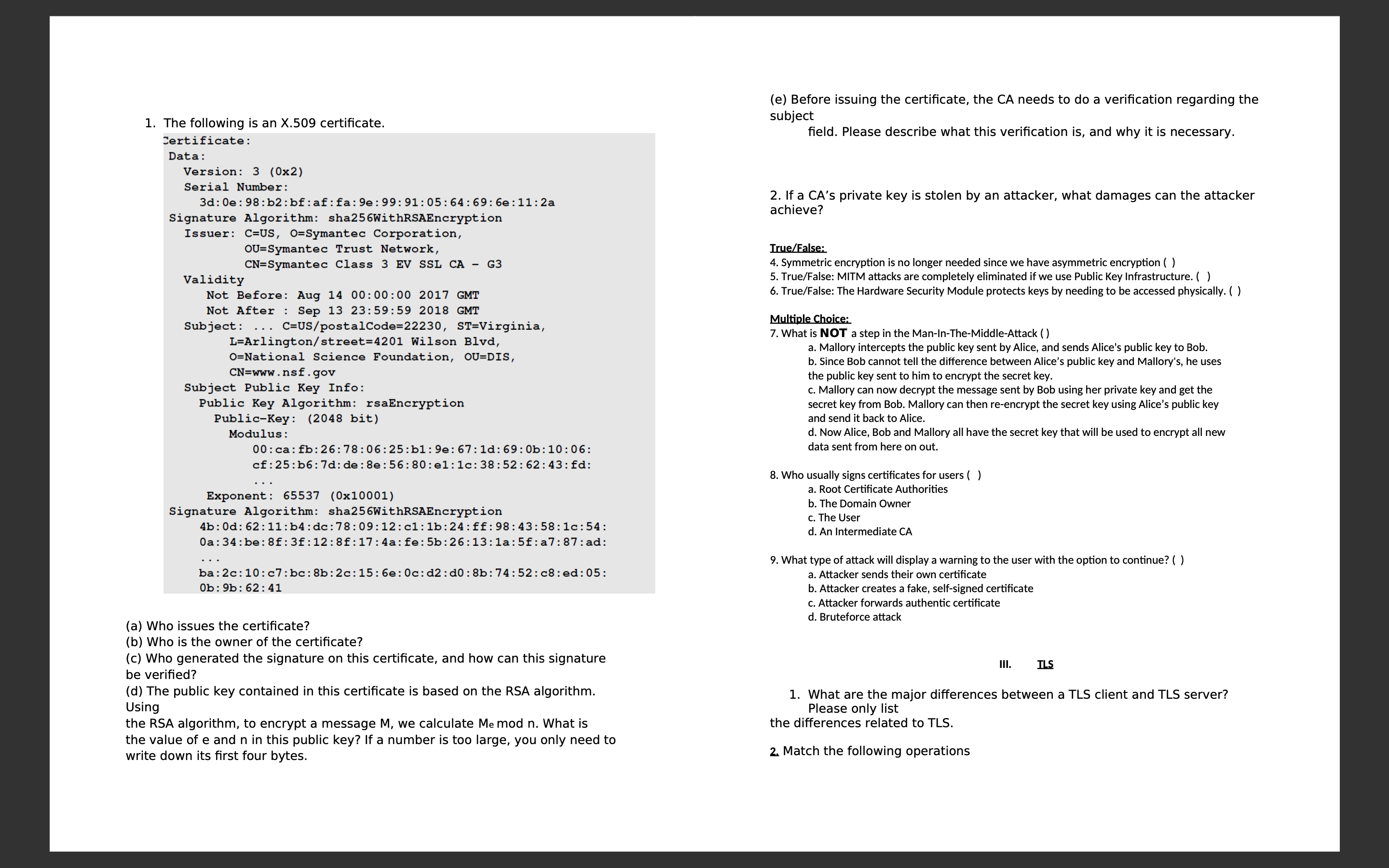
d Hashing the block header using the SHA hash functionThe following is an X certificate.
a Who issues the certificate?
b Who is the owner of the certificate?
c Who generated the signature on this certificate, and how can this signature
be verified?
d The public key contained in this certificate is based on the RSA algorithm.
Using
the RSA algorithm, to encrypt a message we calculate mod What is
the value of and in this public key? If a number is too large, you only need to
write down its first four bytes.
e Before issuing the certificate, the CA needs to do a verification regarding the
subject
field. Please describe what this verification is and why it is necessary.
If a CA's private key is stolen by an attacker, what damages can the attacker
achieve?
IrueFalse:
Symmetric encryption is no longer needed since we have asymmetric encryption
TrueFalse: MITM attacks are completely eliminated if we use Public Key Infrastructure.
TrueFalse: The Hardware Security Module protects keys by needing to be accessed physically.
Multiple Choice:
What is NOT a step in the ManInTheMiddleAttack
a Mallory intercepts the public key sent by Alice, and sends Alice's public key to Bob.
b Since Bob cannot tell the difference between Alice's public key and Mallory's, he uses
the public key sent to him to encrypt the secret key.
c Mallory can now decrypt the message sent by Bob using her private key and get the
secret key from Bob. Mallory can then reencrypt the secret key using Alice's public key
and send it back to Alice.
d Now Alice, Bob and Mallory all have the secret key that will be used to encrypt all new
data sent from here on out.
Who usually signs certificates for users
a Root Certificate Authorities
b The Domain Owner
c The User
d An Intermediate CA
What type of attack will display a warning to the user with the option to continue?
a Attacker sends their own certificate
b Attacker creates a fake, selfsigned certificate
c Attacker forwards authentic certificate
d Bruteforce attack
III. ILS
What are the major differences between a TLS client and TLS server?
Please only list
the differences related to TLS
Match the following operations
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


