Question: i . Discuss the key difference between random - access protocols and controlled - access protocols. State two examples for each type, excluding any ALOHA
i Discuss the key difference between randomaccess protocols and controlledaccess
protocols. State two examples for each type, excluding any ALOHA protocols. marks
ii Determine the vulnerable periods and throughputs for both the pure Aloha network and the
slotted Aloha network, given a frame size of Kbits a data rate of Mbps the average
number of frames G generated by the system during one frame transmission time is
Which Aloha protocol demonstrates superior efficiency? Justify your answer. marks
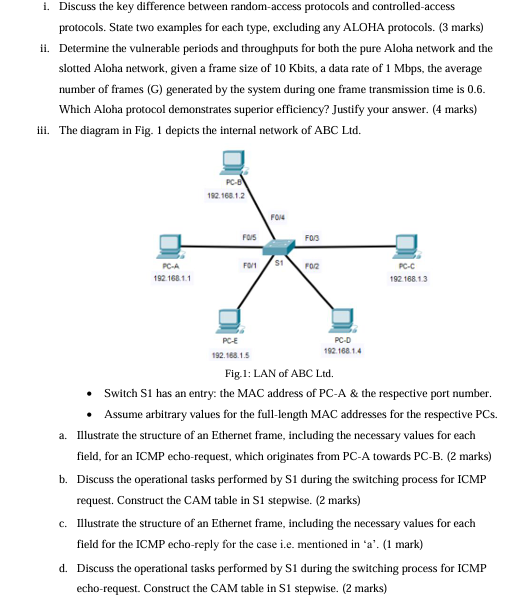
iii. The diagram in Fig. depicts the internal network of ABC Ltd
Switch S has an entry: the MAC address of PCA & the respective port number.
Assume arbitrary values for the fulllength MAC addresses for the respective PCs
a Illustrate the structure of an Ethernet frame, including the necessary values for each
field, for an ICMP echorequest, which originates from PCA towards PCB marks
b Discuss the operational tasks performed by S during the switching process for ICMP
request. Construct the CAM table in S stepwise. marks
c Illustrate the structure of an Ethernet frame, including the necessary values for each
field for the ICMP echoreply for the case ie mentioned in mark
d Discuss the operational tasks performed by S during the switching process for ICMP
echorequest. Construct the CAM table in S stepwise. marks
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


