Question: *I don't want a code. Also, make sure to show your work* The decryption function used in the receiver side is summarized as shown below:
*I don't want a code. Also, make sure to show your work*
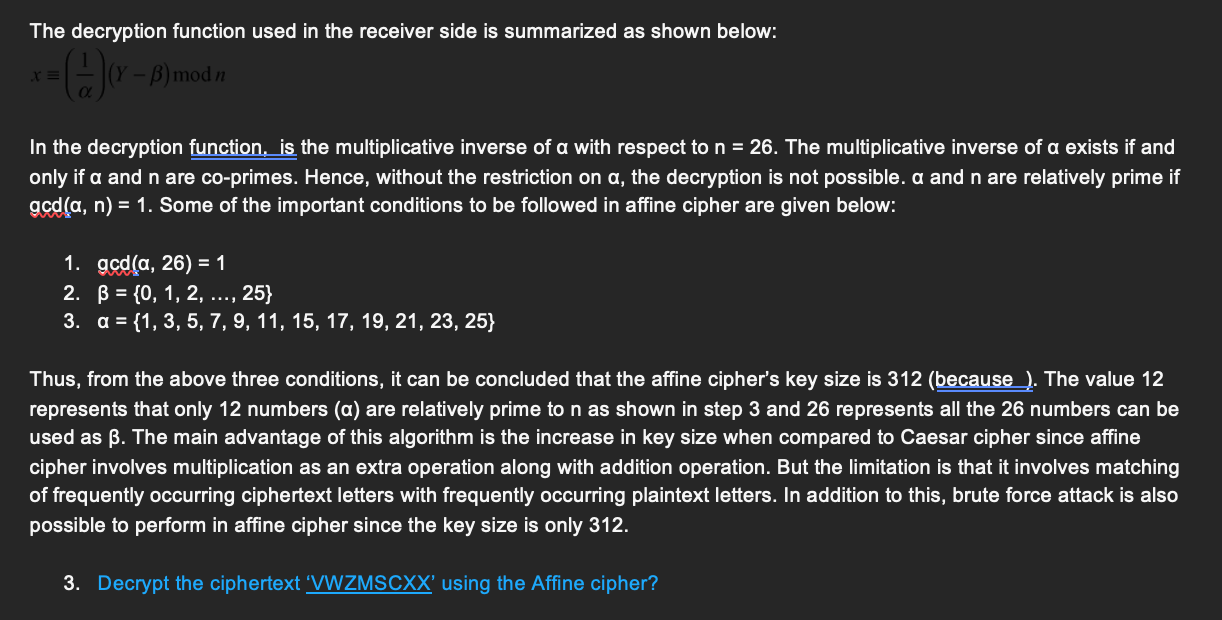
The decryption function used in the receiver side is summarized as shown below: x(1)(Y)modn In the decryption function, is the multiplicative inverse of with respect to n=26. The multiplicative inverse of exists if and only if and n are co-primes. Hence, without the restriction on , the decryption is not possible. and n are relatively prime if gcd(,n)=1. Some of the important conditions to be followed in affine cipher are given below: 1. gcd(,26)=1 2. ={0,1,2,,25} 3. ={1,3,5,7,9,11,15,17,19,21,23,25} Thus, from the above three conditions, it can be concluded that the affine cipher's key size is 312 (because). The value 12 represents that only 12 numbers ( ) are relatively prime to n as shown in step 3 and 26 represents all the 26 numbers can be used as . The main advantage of this algorithm is the increase in key size when compared to Caesar cipher since affine cipher involves multiplication as an extra operation along with addition operation. But the limitation is that it involves matching of frequently occurring ciphertext letters with frequently occurring plaintext letters. In addition to this, brute force attack is also possible to perform in affine cipher since the key size is only 312 . 3. Decrypt the ciphertext 'VWZMSCXX' using the Affine cipher
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


