Question: I hope to answer as soon as possible examples for question 1 Question 1: (8 points) One of the buffer overflow attack causes is Ineffective
I hope to answer as soon as possible


 examples for question 1
examples for question 1
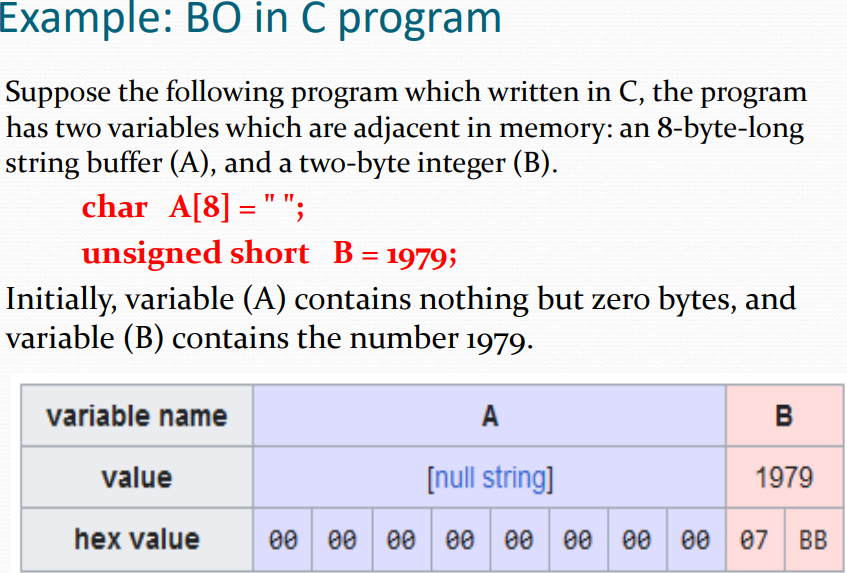
Question 1: (8 points) One of the buffer overflow attack causes is "Ineffective or lacking of input validation"; explain this cause in details, with mentioning an example that clarify this cause other than the example in the slides. Question 2: (8 points) Establishing a backup strategy of a particular system could act as a defense mechanism against malware damages (e.g. files deletion). Explain in details this statement, and provide an example. Question 3: (9 points) There are three main reasons that could facilitate the mechanism of malware installation, list them, and provide an example of each reason that clarifies the concept. Question 4: (15 points) By using one of the free search engines, search for an example of (other than the ones in the slides): Virus, Worm, Trojan, and Rootkit And explain briefly the operation (e.g. mechanism, targets, and damages) of each example. Example: BO in C program, Cont'd Now, the program attempts to store the "excessive" string terminated by null character (null-terminated string) in ASCII encoding in the (A) buffer, by using: strcpy(A, "excessive"); "excessive" is 9 characters long and encodes to 10 bytes including the null terminator, but (A) can take only 8 bytes. By failing to check the length of the string, it also overwrites the value of (B): Suppose the following program which written in C, the program has two variables which are adjacent in memory: an 8-byte-long string buffer (A), and a two-byte integer (B). char A[8]= " "; unsigned short B=1979; Initially, variable (A) contains nothing but zero bytes, and variable (B) contains the number 1979
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


