Question: i need the correct answers from the options Question 1 (1 point) Saved Which type of intrusion detection system (IDs) can be considered an expert

i need the correct answers from the options
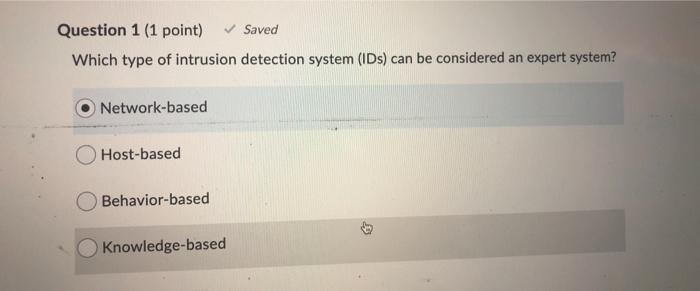
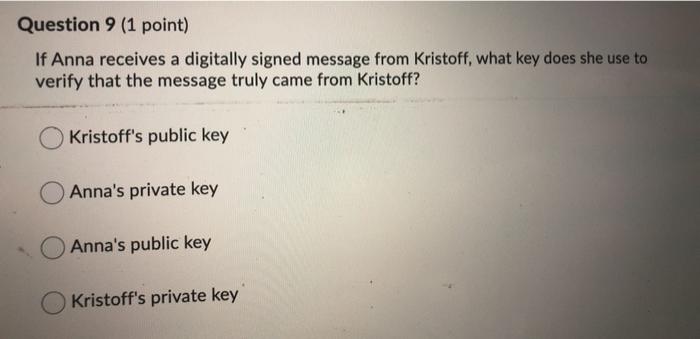
Question 1 (1 point) Saved Which type of intrusion detection system (IDs) can be considered an expert system? Network-based Host-based Behavior-based Knowledge-based Question 4 (1 point) What is the first step of the business impact assessment process? Risk identification Resource prioritization Likelihood assessment Identification of priorities Saved Question 9 (1 point) If Anna receives a digitally signed message from Kristoff, what key does she use to verify that the message truly came from Kristoff? Kristoff's public key Anna's private key Anna's public key Kristoff's private key
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


