Question: I Symmetric Cryptosystem In this programming Assignment, students are asked to implement a toy symmetric cryptosystem based on the following method. a. Keys are b.
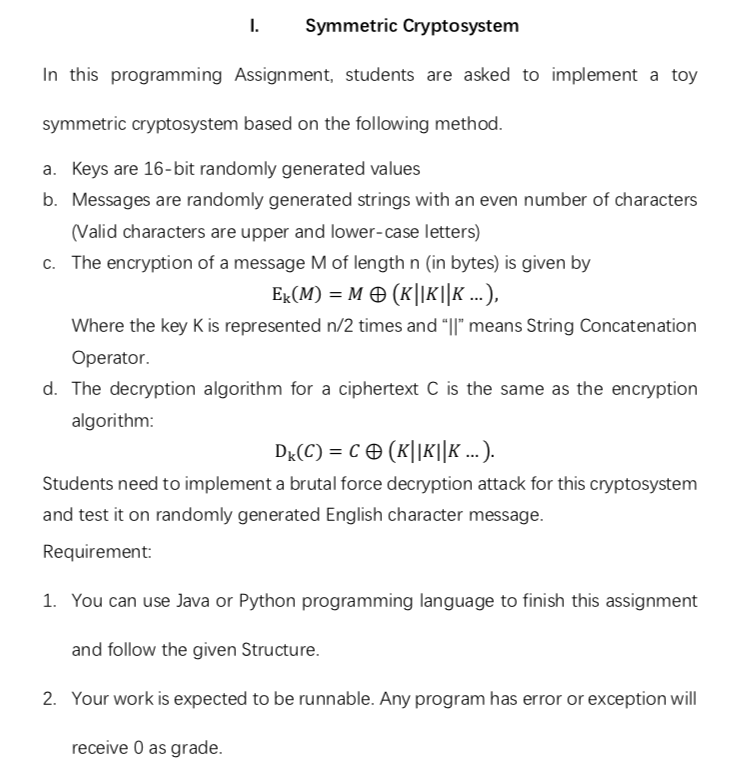
I Symmetric Cryptosystem In this programming Assignment, students are asked to implement a toy symmetric cryptosystem based on the following method. a. Keys are b. Messages are randomly generated strings with an even number of characters 16-bit randomly generated values Valid characters are upper and lower-case letters) The encryption of a message M of length n (in bytes) is given by c. Ek(M)-M (KI IKK ). Where the key K is represented n/2 times and "lI" means String Concatenation Operator. d. The decryption algorithm for a ciphertext C is the same as the encryption algorithm Students need to implement a brutal force decryption attack for this cryptosystem and test it on randomly generated English character message. Requirement: 1. You can use Java or Python programming language to finish this assignment and follow the given Structure. Your work is expected to be runnable. Any program has error or exception will receive 0 as grade. 2. I Symmetric Cryptosystem In this programming Assignment, students are asked to implement a toy symmetric cryptosystem based on the following method. a. Keys are b. Messages are randomly generated strings with an even number of characters 16-bit randomly generated values Valid characters are upper and lower-case letters) The encryption of a message M of length n (in bytes) is given by c. Ek(M)-M (KI IKK ). Where the key K is represented n/2 times and "lI" means String Concatenation Operator. d. The decryption algorithm for a ciphertext C is the same as the encryption algorithm Students need to implement a brutal force decryption attack for this cryptosystem and test it on randomly generated English character message. Requirement: 1. You can use Java or Python programming language to finish this assignment and follow the given Structure. Your work is expected to be runnable. Any program has error or exception will receive 0 as grade. 2
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


