Question: * Identify Controls: Provide guidelines, and practices that illustrate a method to achieve the outcomes of each Subcategory. Once you identify the control (methods, controls),
* Identify Controls:
Provide guidelines, and practices that illustrate a method to achieve the outcomes of each Subcategory. Once you identify the control (methods, controls), you have to indicate if it is preventative, detective, or corrective.
Tasks:
* Provide 10 controls throughout the spreadsheet.
* Must do at least 4 of the 6 Categories.
* No more than one control per chosen subcategory.
*No more than 5 Administrative controls across the spreadsheet.
*No more than 2 physical controls across the spreadsheet.
* Provide at least 3 Technical controls to apply across the spreadsheet.
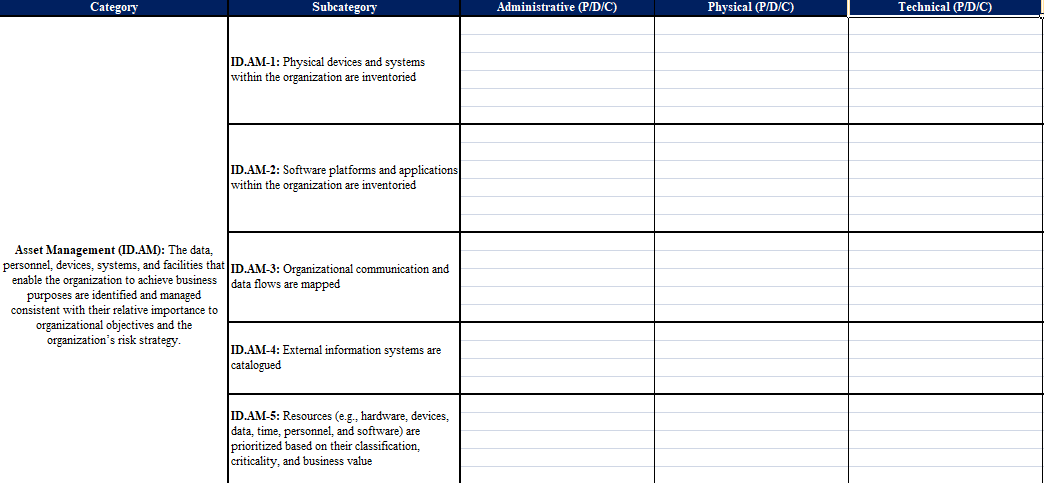

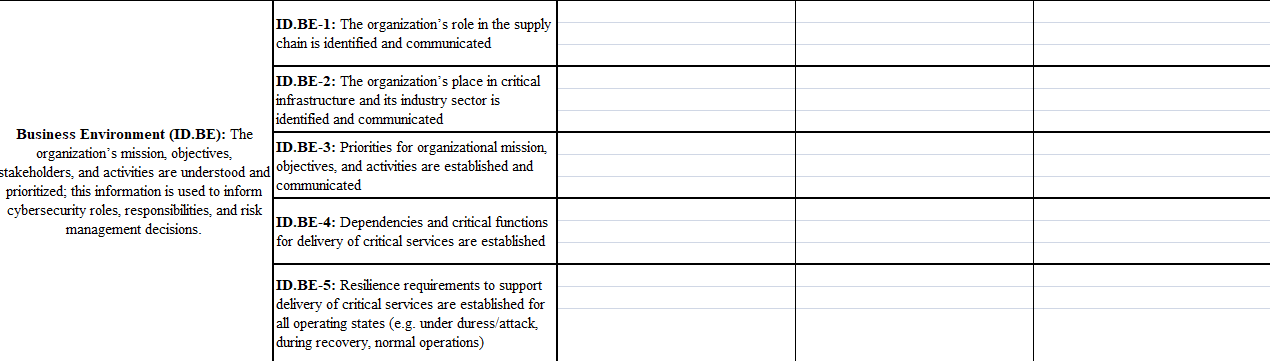
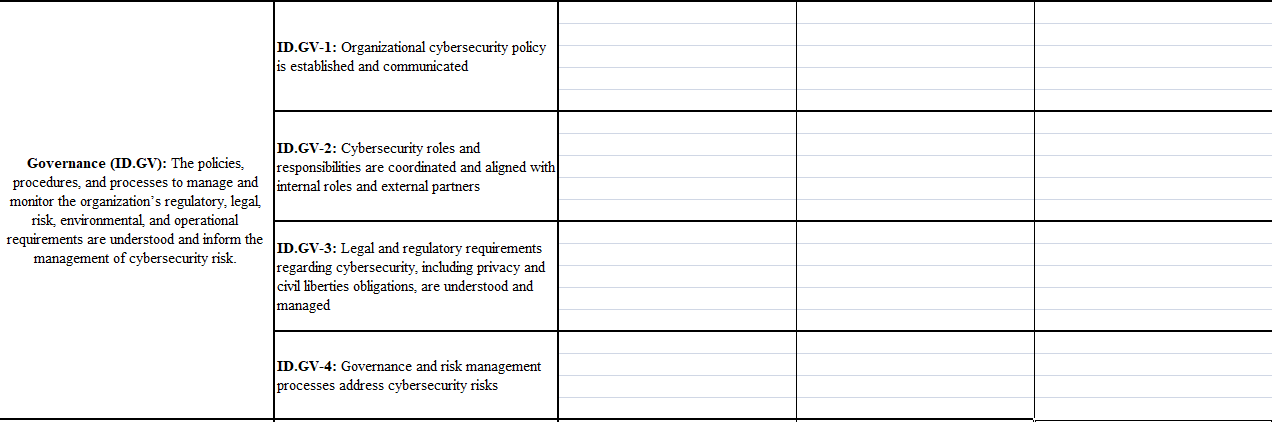
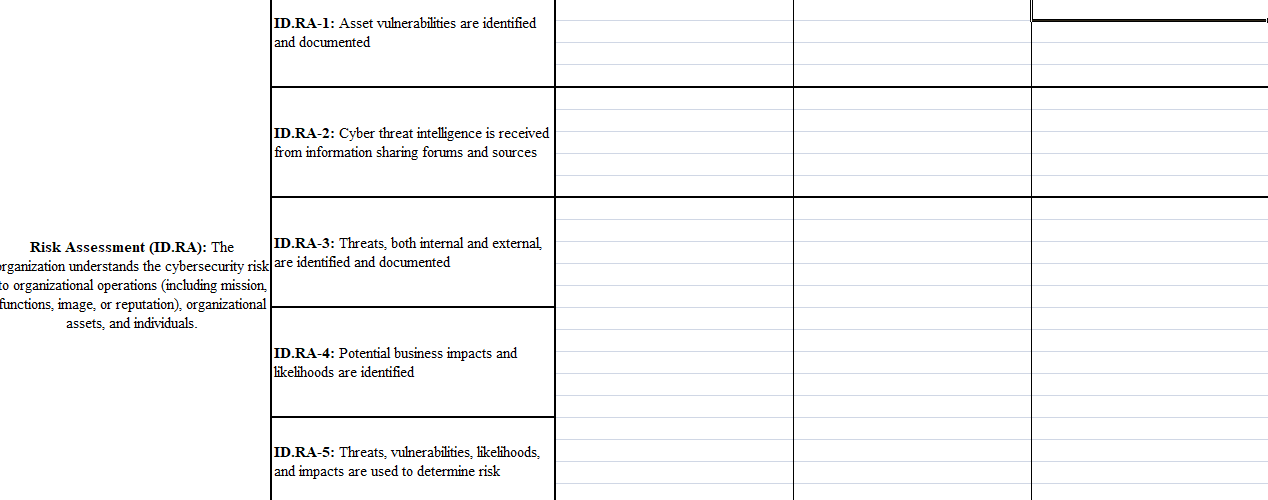
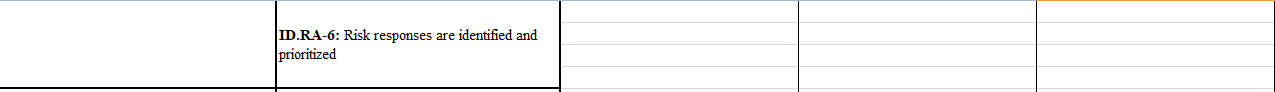

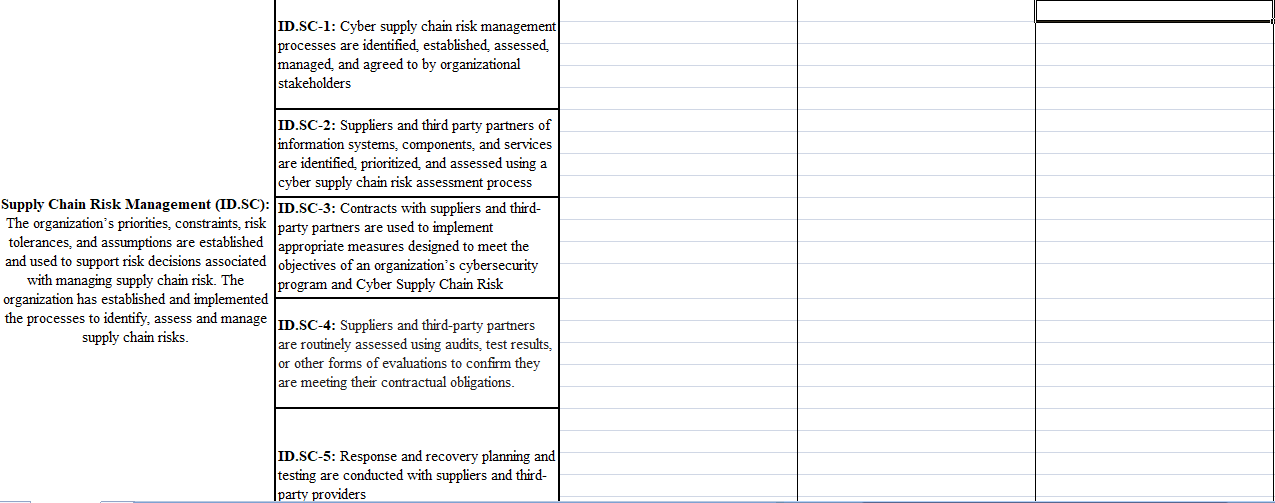
Category Subcategory Administrative (P/D/C) Physical (P/D/C) Technical (P/D/C) ID.AM-1: Physical devices and systems within the organization are inventoried ID.AM-2: Software platforms and applications within the organization are inventoried Asset Management (ID.AM): The data, personnel, devices, systems, and facilities that ID.AM-3: Organizational communication and enable the organization to achieve business data flows are mapped purposes are identified and managed consistent with their relative importance to organizational objectives and the organization's risk strategy. ID.AM-4: External information systems are catalogued ID.AM-5: Resources (e.g., hardware, devices, data, time, personnel, and software) are prioritized based on their classification, criticality, and business value ID.AM-6: Cybersecurity roles and responsibilities for the entire workforce and third-party stakeholders (e.g., suppliers, customers, partners) are established ID.BE-1: The organization's role in the supply chain is identified and communicated ID.BE-2: The organization's place in critical infrastructure and its industry sector is identified and communicated Business Environment (ID.BE): The organization's mission, objectives, ID.BE-3: Priorities for organizational mission, stakeholders, and activities are understood and objectives, and activities are established and prioritized; this information is used to inform communicated cybersecurity roles, responsibilities, and risk management decisions. ID.BE-4: Dependencies and critical functions for delivery of critical services are established ID.BE-5: Resilience requirements to support delivery of critical services are established for all operating states (e.g. under duress/attack, during recovery, normal operations) ID.GV-1: Organizational cybersecurity policy is established and communicated ID.GV-2: Cybersecurity roles and Governance (ID.GV): The policies, responsibilities are coordinated and aligned with procedures, and processes to manage and internal roles and external partners monitor the organization's regulatory, legal risk, environmental and operational requirements are understood and inform the ID.GV-3: Legal and regulatory requirements management of cybersecurity risk. regarding cybersecurity, including privacy and civil liberties obligations, are understood and managed ID.GV-4: Governance and risk management processes address cybersecurity risks ID.RA-1: Asset vulnerabilities are identified and documented ID.RA-2: Cyber threat intelligence is received from information sharing forums and sources Risk Assessment (ID.RA): The ID.RA-3: Threats, both internal and external organization understands the cybersecurity risk are identified and documented to organizational operations including mission, functions, image, or reputation), organizational assets, and individuals ID.RA-4: Potential business impacts and likelihoods are identified ID.RA-5: Threats, vulnerabilities, likelihoods, and impacts are used to determine risk ID.RA-6: Risk responses are identified and prioritized ID.RM-1: Risk management processes are established, managed and agreed to by organizational stakeholders Risk Management Strategy (ID.RM): The organization's priorities, constraints, risk tolerances, and assumptions are established ID.RM-2: Organizational risk tolerance is and used to support operational risk decisions. determined and clearly expressed ID.RM-3: The organization's determination of risk tolerance is informed by its role in critical infrastructure and sector specific risk analysis ID.SC-1: Cyber supply chain risk management processes are identified, established, assessed, managed and agreed to by organizational stakeholders ID.SC-2: Suppliers and third party partners of information systems, components, and services are identified prioritized and assessed using a cyber supply chain risk assessment process Supply Chain Risk Management (ID.SC): ID.SC-3: Contracts with suppliers and third- The organization's priorities, constraints, risk party partners are used to implement tolerances, and assumptions are established appropriate measures designed to meet the and used to support risk decisions associated objectives of an organization's cybersecurity with managing supply chain risk. The program and Cyber Supply Chain Risk organization has established and implemented the processes to identify, assess and manage ID.SC-4: Suppliers and third-party partners supply chain risks. are routinely assessed using audits, test results, or other forms of evaluations to confirm they are meeting their contractual obligations. ID.SC-5: Response and recovery planning and testing are conducted with suppliers and third- Iparty providers Category Subcategory Administrative (P/D/C) Physical (P/D/C) Technical (P/D/C) ID.AM-1: Physical devices and systems within the organization are inventoried ID.AM-2: Software platforms and applications within the organization are inventoried Asset Management (ID.AM): The data, personnel, devices, systems, and facilities that ID.AM-3: Organizational communication and enable the organization to achieve business data flows are mapped purposes are identified and managed consistent with their relative importance to organizational objectives and the organization's risk strategy. ID.AM-4: External information systems are catalogued ID.AM-5: Resources (e.g., hardware, devices, data, time, personnel, and software) are prioritized based on their classification, criticality, and business value ID.AM-6: Cybersecurity roles and responsibilities for the entire workforce and third-party stakeholders (e.g., suppliers, customers, partners) are established ID.BE-1: The organization's role in the supply chain is identified and communicated ID.BE-2: The organization's place in critical infrastructure and its industry sector is identified and communicated Business Environment (ID.BE): The organization's mission, objectives, ID.BE-3: Priorities for organizational mission, stakeholders, and activities are understood and objectives, and activities are established and prioritized; this information is used to inform communicated cybersecurity roles, responsibilities, and risk management decisions. ID.BE-4: Dependencies and critical functions for delivery of critical services are established ID.BE-5: Resilience requirements to support delivery of critical services are established for all operating states (e.g. under duress/attack, during recovery, normal operations) ID.GV-1: Organizational cybersecurity policy is established and communicated ID.GV-2: Cybersecurity roles and Governance (ID.GV): The policies, responsibilities are coordinated and aligned with procedures, and processes to manage and internal roles and external partners monitor the organization's regulatory, legal risk, environmental and operational requirements are understood and inform the ID.GV-3: Legal and regulatory requirements management of cybersecurity risk. regarding cybersecurity, including privacy and civil liberties obligations, are understood and managed ID.GV-4: Governance and risk management processes address cybersecurity risks ID.RA-1: Asset vulnerabilities are identified and documented ID.RA-2: Cyber threat intelligence is received from information sharing forums and sources Risk Assessment (ID.RA): The ID.RA-3: Threats, both internal and external organization understands the cybersecurity risk are identified and documented to organizational operations including mission, functions, image, or reputation), organizational assets, and individuals ID.RA-4: Potential business impacts and likelihoods are identified ID.RA-5: Threats, vulnerabilities, likelihoods, and impacts are used to determine risk ID.RA-6: Risk responses are identified and prioritized ID.RM-1: Risk management processes are established, managed and agreed to by organizational stakeholders Risk Management Strategy (ID.RM): The organization's priorities, constraints, risk tolerances, and assumptions are established ID.RM-2: Organizational risk tolerance is and used to support operational risk decisions. determined and clearly expressed ID.RM-3: The organization's determination of risk tolerance is informed by its role in critical infrastructure and sector specific risk analysis ID.SC-1: Cyber supply chain risk management processes are identified, established, assessed, managed and agreed to by organizational stakeholders ID.SC-2: Suppliers and third party partners of information systems, components, and services are identified prioritized and assessed using a cyber supply chain risk assessment process Supply Chain Risk Management (ID.SC): ID.SC-3: Contracts with suppliers and third- The organization's priorities, constraints, risk party partners are used to implement tolerances, and assumptions are established appropriate measures designed to meet the and used to support risk decisions associated objectives of an organization's cybersecurity with managing supply chain risk. The program and Cyber Supply Chain Risk organization has established and implemented the processes to identify, assess and manage ID.SC-4: Suppliers and third-party partners supply chain risks. are routinely assessed using audits, test results, or other forms of evaluations to confirm they are meeting their contractual obligations. ID.SC-5: Response and recovery planning and testing are conducted with suppliers and third- Iparty providers
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


