Question: Identify Data Feeds 1. Email Server Compromise a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed
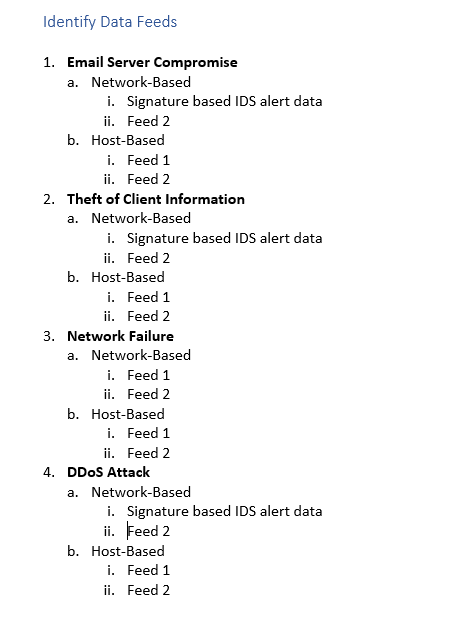
Identify Data Feeds 1. Email Server Compromise a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 2. Theft of Client Information a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 3. Network Failure a. Network-Based i. Feed 1 ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 4. DDoS Attack a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 Identify Data Feeds 1. Email Server Compromise a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 2. Theft of Client Information a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 3. Network Failure a. Network-Based i. Feed 1 ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2 4. DDoS Attack a. Network-Based i. Signature based IDS alert data ii. Feed 2 b. Host-Based i. Feed 1 ii. Feed 2
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


