Question: If anybody can help. Have no idea how to do it. As a reminder, a diagram showing the workings of CBC-MAC over a block cipher
If anybody can help. Have no idea how to do it.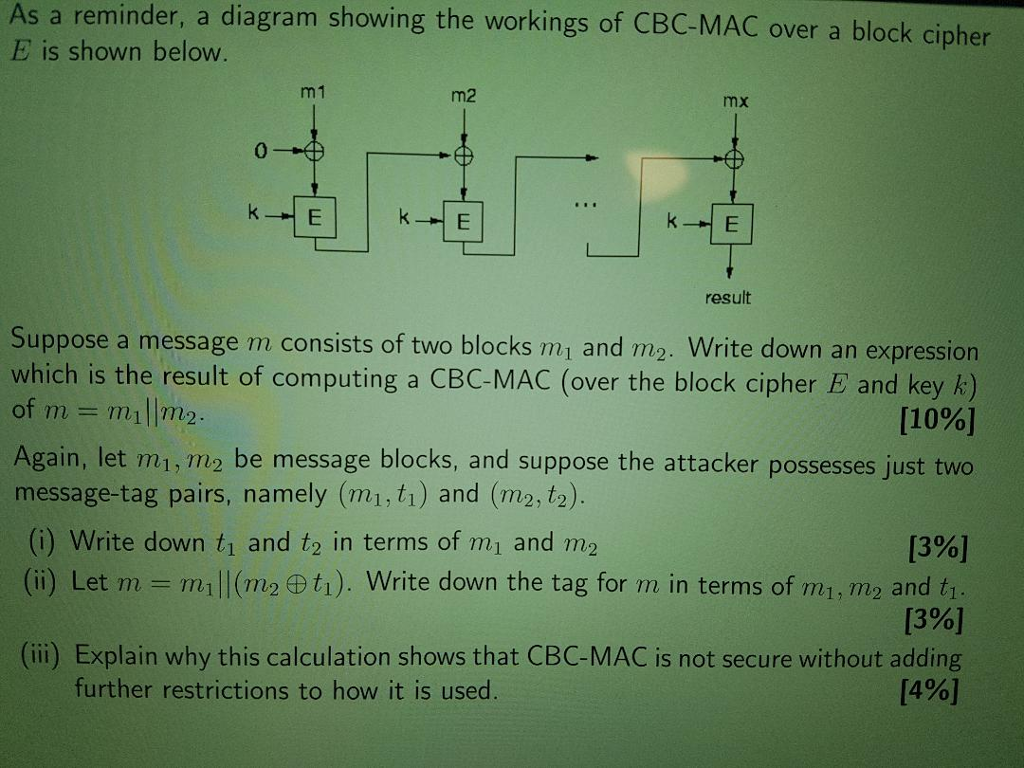
As a reminder, a diagram showing the workings of CBC-MAC over a block cipher E is shown below m1 m2 mx 0 k-E result Suppose a message m consists of two blocks mi and m2. Write down an expression which is the result of computing a CBC-MAC (over the block cipher E and key k) [1096] Again, let mi, 77m2 be message blocks, and suppose the attacker possesses just two of m = millm2 message-tag pairs, namely (mi,t1) and (m2, t2). (i) Write down t1 and t2 in terms of mi and m2 [3%] (ii) Let m = mill (mp@t). Write down the tag for n in terms of m, m2 and t1 [396] (ii) Explain why this calculation shows that CBC-MAC is not secure without adding [4%) further restrictions to how it is used. As a reminder, a diagram showing the workings of CBC-MAC over a block cipher E is shown below m1 m2 mx 0 k-E result Suppose a message m consists of two blocks mi and m2. Write down an expression which is the result of computing a CBC-MAC (over the block cipher E and key k) [1096] Again, let mi, 77m2 be message blocks, and suppose the attacker possesses just two of m = millm2 message-tag pairs, namely (mi,t1) and (m2, t2). (i) Write down t1 and t2 in terms of mi and m2 [3%] (ii) Let m = mill (mp@t). Write down the tag for n in terms of m, m2 and t1 [396] (ii) Explain why this calculation shows that CBC-MAC is not secure without adding [4%) further restrictions to how it is used
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


