Question: I'm really confused how to do this problem. Any help is appreciated. UserA UserC Routerl Router2 Network1 Network2 UserD UserB Attacker 3 Figure 1: Reference
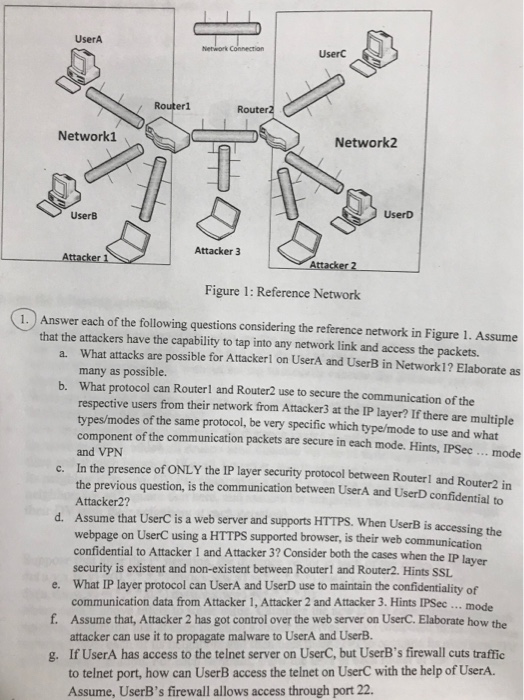
UserA UserC Routerl Router2 Network1 Network2 UserD UserB Attacker 3 Figure 1: Reference Network 1.) Answer each of the following questions considering the reference network in Figure 1. Assume that the attackers have the capability to tap into any network link and access the packets. What attacks are possible for Attackerl on UserA and UserB in Network 1? Elaborate as many as possible. What protocol can Routerl and Router2 use to secure the communication of the respective users from their network from Attacker3 at the IP layer? If there are multiple types/modes of the same protocol, be very specific which type/mode to use and what component of the communication packets are secure in each mode. Hints, IPSec mode and VPN a. b. c. In the presence of ONLY the IP layer security protocol between Routerl and Router2 in the previous question, is the communication between UserA and UserD confidential to Attacker2? Assume that UserC is a web server and supports HTTPS. When UserB is accessing the webpage on UserC using a HTTPS supported confidential to Attacker 1 and Attacker 3? Consider both the cases when the IP security is existent and non-existent between Routerl and Router2. Hints SSL d. browser, is their web communication layer e. What IP layer protocol can UserA and UserD use to maintain the confidentiality of f. Assume that, Attacker 2 has got control over the web server on UserC. Elaborate how the g. If UserA has access to the telnet server on UserC, but UserB's firewall cuts traffic mode communication data from Attacker 1, Attacker 2 and Attacker 3. Hints IPSec attacker can use it to propagate malware to UserA and UserB. to telnet port, how can UserB access the telnet on UserC with the help of UserA Assume, UserB's firewall allows access through port 22
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


