Question: In cryptography, a Caesar1 cipher is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which
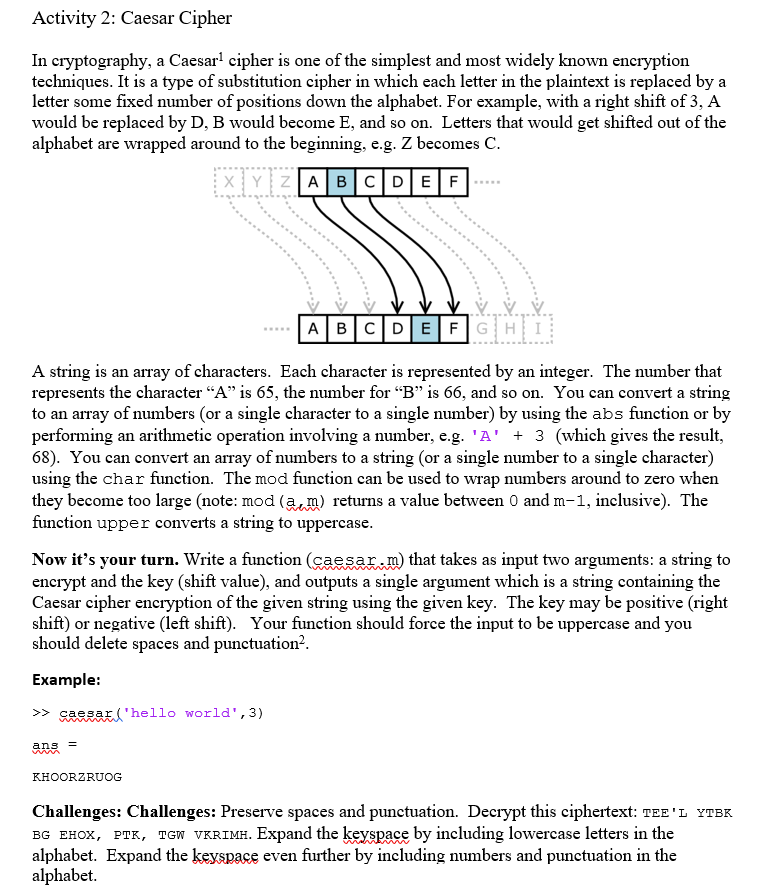
In cryptography, a Caesar1 cipher is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a right shift of 3, A would be replaced by D. B would become E, and so on. Letters that would get shifted out of the alphabet are wrapped around to the beginning, e.g. Z becomes C. A string is an array of characters. Each character is represented by an integer. The number that represents the character "A" is 65, the number for "B" is 66, and so on. You can convert a string to an array of numbers (or a single character to a single number) by using the abs function or by performing an arithmetic operation involving a number, e.g. ' A' + 3 (which gives the result, 68). You can convert an array of numbers to a string (or a single number to a single character) using the char function. The mod function can be used to wrap numbers around to zero when they become too large Now it's your turn. Write a function (caesar.m) that takes as input two arguments: a string to encrypt and the key (shift value), and outputs a single argument which is a string containing the Caesar cipher encryption of the given string using the given key. The key may be positive (right shift) or negative (left shift). Your function should force the input to be uppercase and you should delete spaces and punctuation^2. Example: >> caesar('hello world',3) ans = KHOORZRUOG Challenges: Challenges: Preserve spaces and punctuation. Decrypt this ciphertext: TEE'L YTBK BG EHOX, PTK, TGW VKRIMH. Expand the keyspace by including lowercase letters in the alphabet. Expand the keyspace even further by including numbers and punctuation in the alphabet. In cryptography, a Caesar1 cipher is one of the simplest and most widely known encryption techniques. It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. For example, with a right shift of 3, A would be replaced by D. B would become E, and so on. Letters that would get shifted out of the alphabet are wrapped around to the beginning, e.g. Z becomes C. A string is an array of characters. Each character is represented by an integer. The number that represents the character "A" is 65, the number for "B" is 66, and so on. You can convert a string to an array of numbers (or a single character to a single number) by using the abs function or by performing an arithmetic operation involving a number, e.g. ' A' + 3 (which gives the result, 68). You can convert an array of numbers to a string (or a single number to a single character) using the char function. The mod function can be used to wrap numbers around to zero when they become too large Now it's your turn. Write a function (caesar.m) that takes as input two arguments: a string to encrypt and the key (shift value), and outputs a single argument which is a string containing the Caesar cipher encryption of the given string using the given key. The key may be positive (right shift) or negative (left shift). Your function should force the input to be uppercase and you should delete spaces and punctuation^2. Example: >> caesar('hello world',3) ans = KHOORZRUOG Challenges: Challenges: Preserve spaces and punctuation. Decrypt this ciphertext: TEE'L YTBK BG EHOX, PTK, TGW VKRIMH. Expand the keyspace by including lowercase letters in the alphabet. Expand the keyspace even further by including numbers and punctuation in the alphabet
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


