Question: In JAVA PLEASE. Follow the UML. Thank you so much. CryptogramClient.java (fully implemented) // Cryptogram Client // YOUR NAME // 11/1/2017 import java.util.*; import java.io.*;

![import java.io.*; public class CryptogramClient { public static void main(String[] args) throws](https://dsd5zvtm8ll6.cloudfront.net/si.experts.images/questions/2024/09/66f3d6a356684_22666f3d6a2edf07.jpg)

In JAVA PLEASE. Follow the UML. Thank you so much.
CryptogramClient.java (fully implemented)
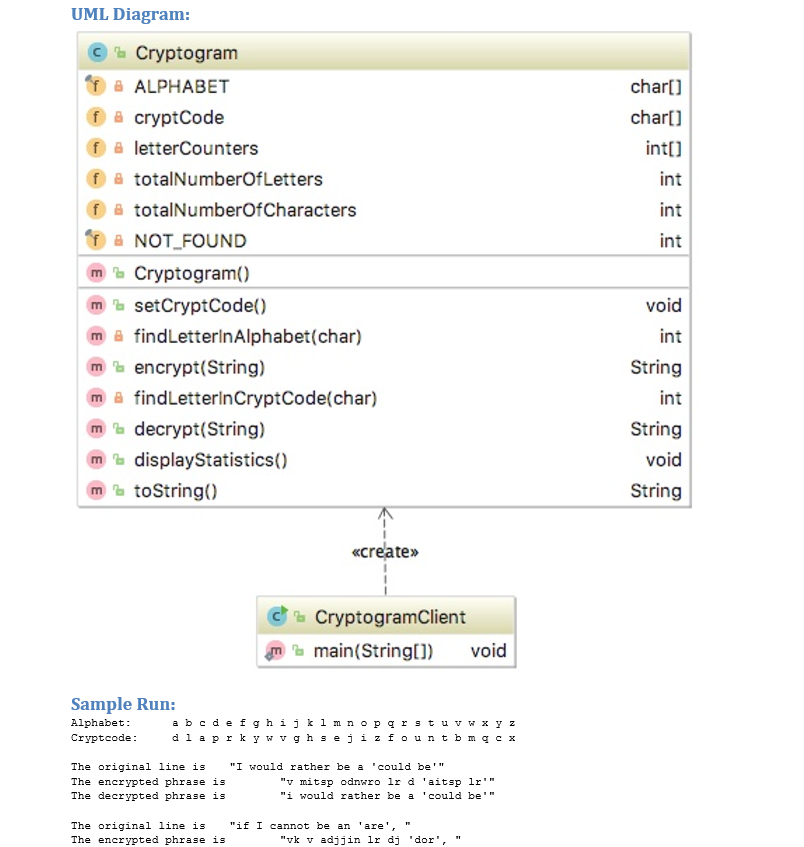
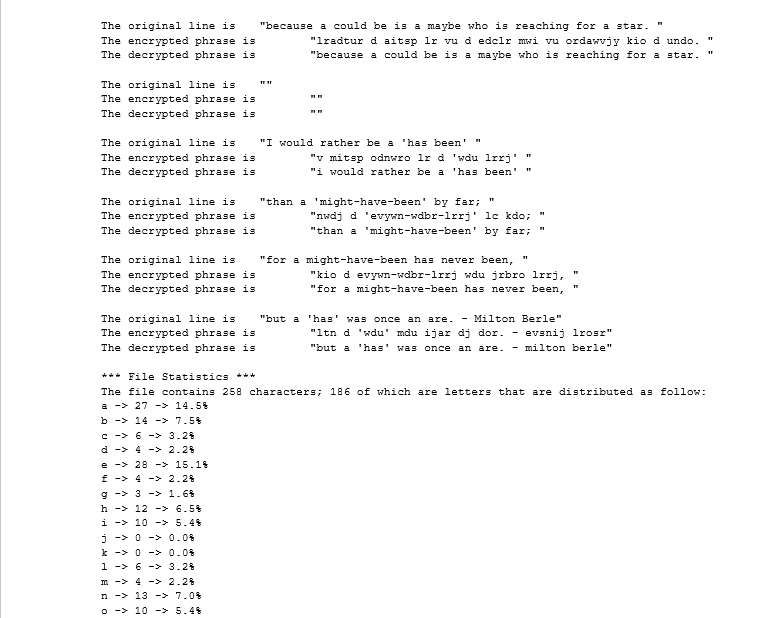
// Cryptogram Client // YOUR NAME // 11/1/2017 import java.util.*; import java.io.*; public class CryptogramClient { public static void main(String[] args) throws IOException { Cryptogram cryptogram = new Cryptogram(); System.out.println(cryptogram); // print alphabet and substitution code Scanner fromFile = new Scanner(new File("src/wish.txt")); while (fromFile.hasNext()) { String phrase = fromFile.nextLine(); System.out.println(" The original line is \t \"" + phrase + "\""); String code = cryptogram.encrypt(phrase); System.out.println("The encrypted phrase is \t \"" + code + "\""); String plainText = cryptogram.decrypt(code); System.out.println("The decrypted phrase is \t \"" + plainText + "\""); } System.out.println(); cryptogram.displayStatistics(); } }Security is an important feature of information systems. Often text is encrypted before being sent, and then decrypted upon receipt. For this project, encrypting consists of translating each character into another character. For instance, if we consider the English alphabet, including characters a through z, each character is going to be encrypted based on its mapping given by the cryptogram code. To support this concept, you need to implement Cryptogram.java class, the client class called CryptogramClient.java where the main method is located is fully implemented. See the UML Diagram and the sample run below. crypltogram class has four instant variables: ALPHABET - an array of 26 chars (lowercase letters a to z) which is final lettercounters - an array of ints, that is the same size as the ALPHABET array and will contain the frequencies of each letter in the processed file. The constructor creates the array, so initially the counters will be all 0 totalNumberofLetters - int holding the sum of all letters in the file cryptCode - an array of chars, that is the same size as the ALPHABET array and contains the same values as the ALPHABET array but arranged randomly. This array needs to be generated by the setCryptCode method which would be called by the constructor. For example, we could have 1. 2. 4. ALPHABET cryptCode To encrypt a phrase, a new String is produced where each letter in the phrase is replaced by the corresponding letter in the cryptcode. For example, the word Caged would be encrypted as huzsa(please note that the algorithm converts all the letters to lower case first). To decrypt an
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


