Question: In Java: You will be writing a simple Java program that implements ROT-13 encryption ROT-13 is a very simple encryption scheme that can be used
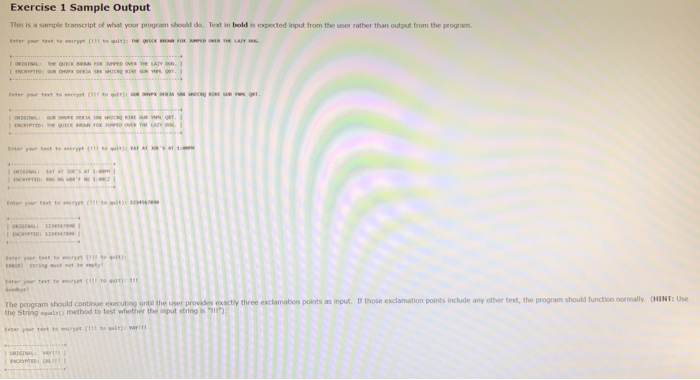
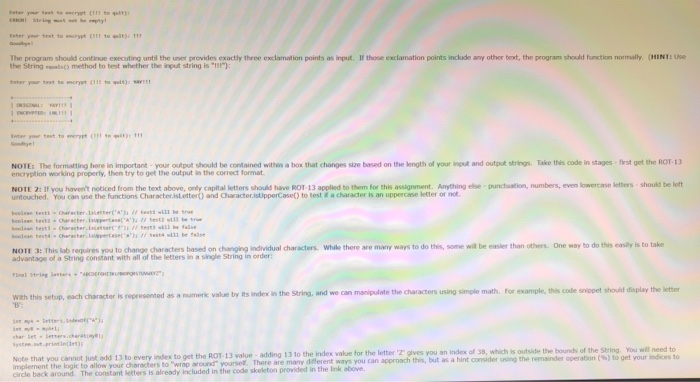
You will be writing a simple Java program that implements ROT-13 encryption ROT-13 is a very simple encryption scheme that can be used to obfuscate text and is based on a very old encryption technique called a Caesar cipher (after Julius Caesar, who reportedly used it to send messages to his armies) or a shift cipher. In a Caesar cipher, the letters in a message are replaced by the letters of a "shifted alphabet. So for example if we had a shift of 3 we might have the following replacements: Punctuation numbers, and other non-alphabetic characters are unaffected by the shrt. So the me sage EAT AT OES AT 1:00" becomes Dw ,Rrv 1:00. ROT-13 is a special cme of the Corsar cither where e characters of the new alphabet are shifted (or "rotated") by 13 positions from the orignal alphabet: So in the case of ROT-13, the message "EAT AT JOE'S AT 1:00 becomes "RNG NG WBRY NG 1:00 Unlke the general case of the Caesar cipher, ROT-13 has a special property that an encrypted message can be decrypted by applying ROT- 13 a second time. So the message "RNG NG WBRy NG 1:00 becomes "EAT AT JOE'S AT 1:00 when passed through a ROT-13 encrvption. You will be writing a Java program that takes an arbitrary string as input, applys ROT13 to the string, and displays the results in a specific format The code must work for uppercase and lowercase letters and must work correctly punctuation and numbers are included in the message. A "skeleton of this code is provided in the Ele given in the instruxctions above. You will see that there are three methods dedlared in this file with no code provided. You must fil in the appropriate code Pay close attention to what each method should be doing based on the information given in the comments before the method. You may add more methods to this skeleton if you feel that it would be useful, but you MUST incdlude code for all of the methods in the skeleton to recelve full t. Exercise 1 Sample Output This is a sample transcript of what your program should do. Text in bold is expected input from the user rather than output from the program
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


