Question: In Lab 5 students will employ password cracking tools in Kali to create word lists and perform different types of offline password cracking activities. There
In Lab 5 students will employ password cracking tools in Kali to create word lists and perform different types of offline password cracking activities. There are multiple tools that assist with password cracking. When answering the assigned questions, ensure that the differences between them are discussed. Answers the following questions (2 points each):
1. What are the main features of cewl tool?
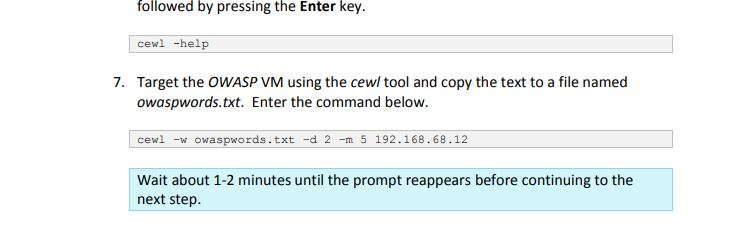
2. What is accomplished with the command in Step 1.7?
3. What are the main features of crunch tool?
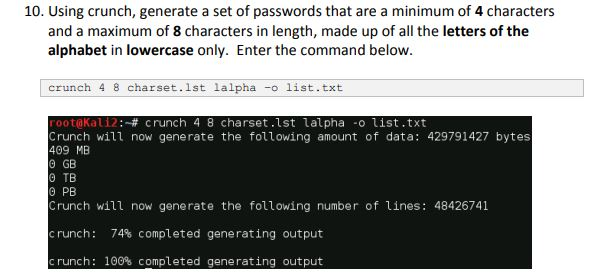
4. What is accomplished with the command in Step 1.10?
5. What information is contained in the /etc/shadow file?
6. What hashing algorithm is used for storing of passwords in Linux?
7. What are the main features of the John tool?
8. What are the main features of the hashcat tool?
followed by pressing the Enter key. cewl -help 7. Target the OWASP VM using the cewl tool and copy the text to a file named owaspwords.txt. Enter the command below cewl -w owaspwords.txt -d 2 -m 5 192.168.68.12 Wait about 1-2 minutes until the prompt reappears before continuing to the next step
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


