Question: In the above program fragment, each process has a random integer key. Fill in the MPI code that will rotate the keys... int main int
In the above program fragment, each process has a random integer key. Fill in the MPI code that will rotate the keys...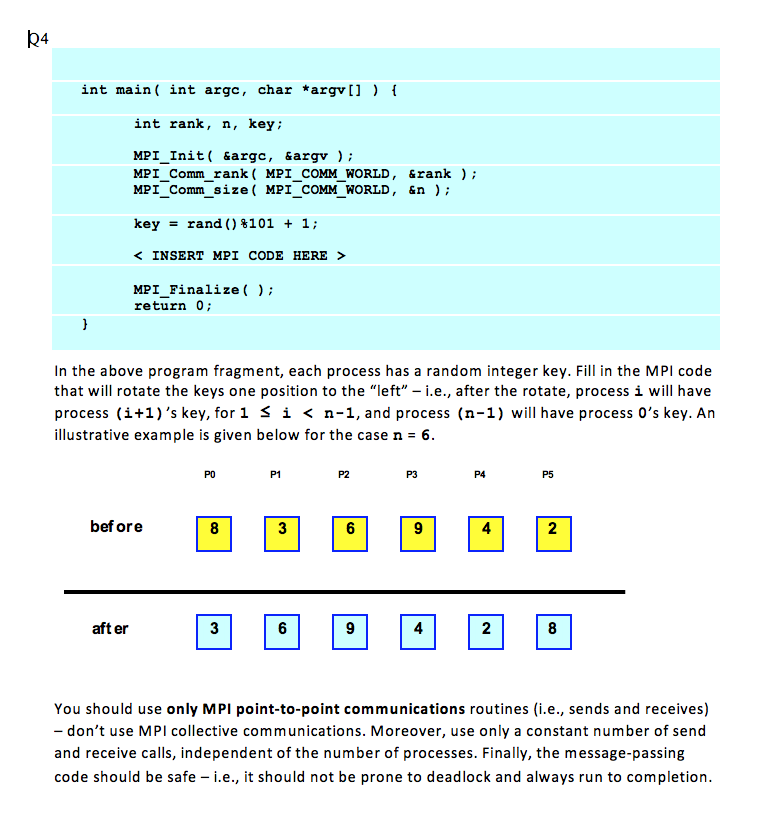
int main int argc, char argv [1 int rank, n, key MPI Init &argo, &argv) MPI Comm rank MPI COMM WORLD &rank MPI Comm size MPI COMM WORLD &n key rand 101 1 INSERT MPI CODE HERE MPI Finalize return 0 In the above program fragment, each process has a random integer key. Fill in the MPI code that will rotate the keys one position to the eft after the rotate, process i will have process (i+1) 's key, for 1 S i n-1, and process n-1) will have process O's key. An illustrative example is given below for the case n 6 P1 P5 before after You should use only MPI point-to-point communications routines (i.e., sends and receives don't use MPI collective communications. Moreover, use only a constant number of send and receive calls, independent of the number of processes. Finally, the message-passing code should be safe i e., t should not be prone to deadlock and always run to completion int main int argc, char argv [1 int rank, n, key MPI Init &argo, &argv) MPI Comm rank MPI COMM WORLD &rank MPI Comm size MPI COMM WORLD &n key rand 101 1 INSERT MPI CODE HERE MPI Finalize return 0 In the above program fragment, each process has a random integer key. Fill in the MPI code that will rotate the keys one position to the eft after the rotate, process i will have process (i+1) 's key, for 1 S i n-1, and process n-1) will have process O's key. An illustrative example is given below for the case n 6 P1 P5 before after You should use only MPI point-to-point communications routines (i.e., sends and receives don't use MPI collective communications. Moreover, use only a constant number of send and receive calls, independent of the number of processes. Finally, the message-passing code should be safe i e., t should not be prone to deadlock and always run to completion
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


