Question: In the situation described in the previous question, attack code must be placed on the stack. That attack code is: In the situation described in
In the situation described in the previous question, attack code must be placed on the stack. That attack code is:
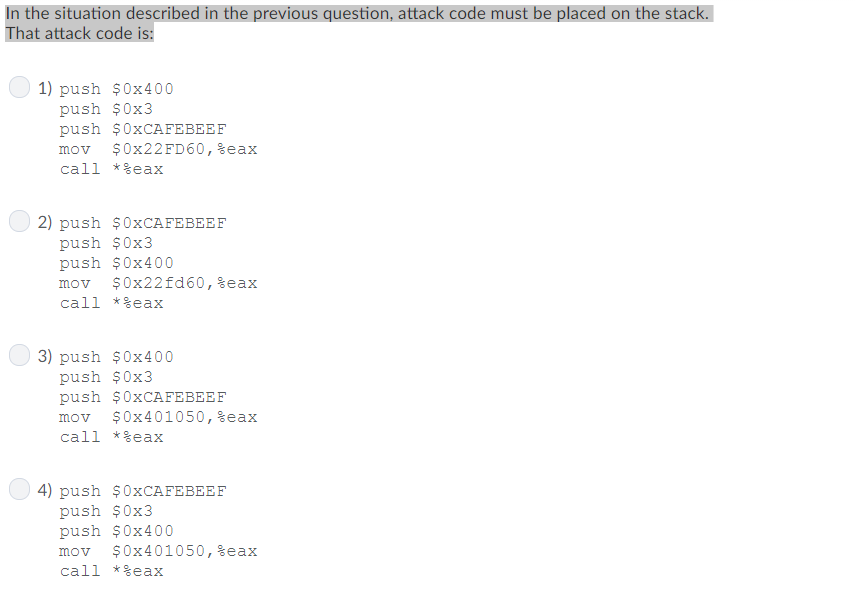
In the situation described in the previous question, attack code must be placed on the stack. That attack code is: 1) push $0x400 push $0x3 push $0xCAFEBEEF mov $0x22FD60,%eax call *%eax 2) push $0xCAFEBEEF push $0x3 push $0x400 mov $0x22fd60,%eax call *%eax 3) push $0x400 push $0x3 push $0xCAFEBEEF mov $0x401050,%eax call *%eax 4) push $0xCAFEBEEF push $0x3 push $0x400 mov $0x401050,%eax call *%eax In the situation described in the previous question, attack code must be placed on the stack. That attack code is: 1) push $0x400 push $0x3 push $0xCAFEBEEF mov $0x22FD60,%eax call *%eax 2) push $0xCAFEBEEF push $0x3 push $0x400 mov $0x22fd60,%eax call *%eax 3) push $0x400 push $0x3 push $0xCAFEBEEF mov $0x401050,%eax call *%eax 4) push $0xCAFEBEEF push $0x3 push $0x400 mov $0x401050,%eax call *%eax
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


