Question: In this project, you will need to implement the 1st round of encryption in Advanced Encryption Candard. More specifically, - Given a message with 128

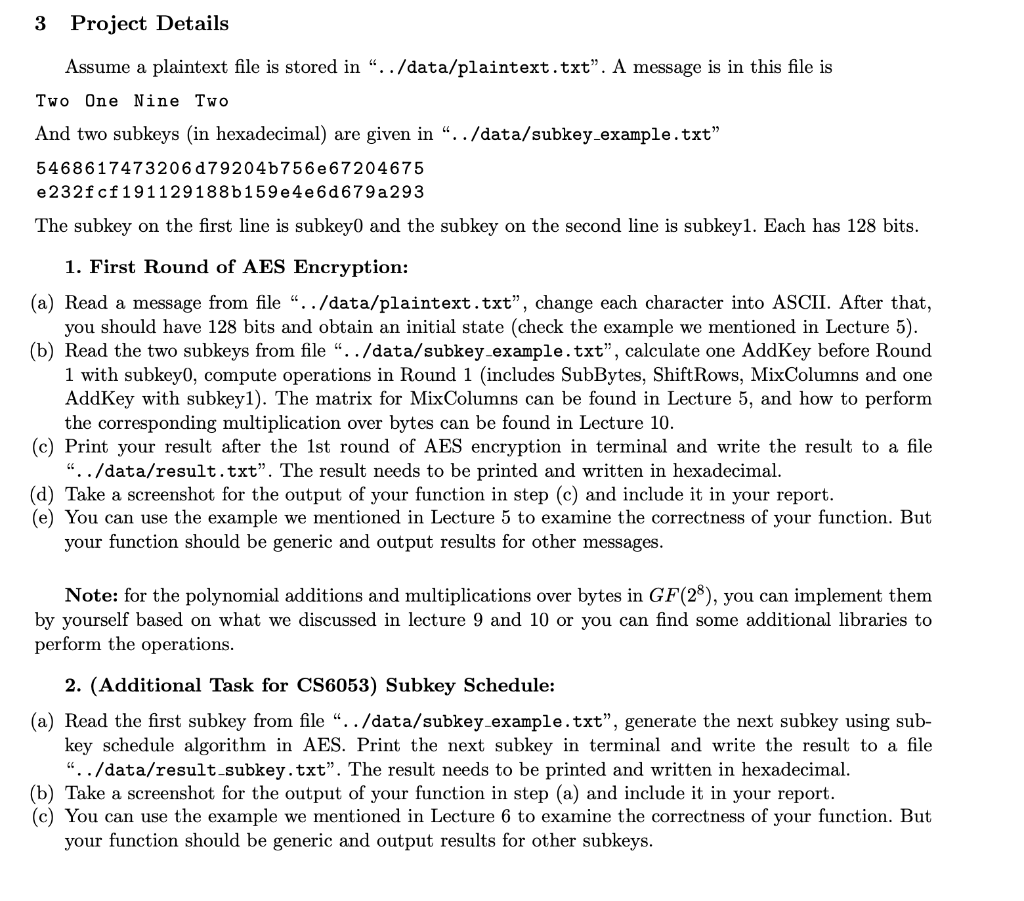
In this project, you will need to implement the 1st round of encryption in Advanced Encryption Candard. More specifically, - Given a message with 128 bits, two subkeys subkey0 and subkey1, your program should be able to perform one AddKey before Round 1 and the corresponding operations (SubBytes, ShiftRows, Mix- Columns, and AddKey) in Round 1, and output the result of the encryption after Round 1. (In this project, we assume S-box which is used in SubBytes is already given and you can find a copy of it from Lecture 5. We also assume an encryption key has 128 bits in this project.) Programming Language: You can use either C/C++, Python or Java. However, C/C++ or Python is preferred. You can choose any IDE you like, the code you submit should be able to compile and run in Linux or Windows. 3 Project Details Assume a plaintext file is stored in ../data/plaintext.txt". A message is in this file is Two One Nine Two And two subkeys (in hexadecimal) are given in ../data/subkey-example.txt" 54686174732060792046756 e 67204675 e232fcf191129188b159 e4e6d679 a 293 The subkey on the first line is subkey and the subkey on the second line is subkey1. Each has 128 bits. 1. First Round of AES Encryption: (a) Read a message from file ../data/plaintext.txt", change each character into ASCII. After that, you should have 128 bits and obtain an initial state (check the example we mentioned in Lecture 5). (b) Read the two subkeys from file" ./data/subkey.example.txt", calculate one AddKey before Round 1 with subkeyo, compute operations in Round 1 (includes SubBytes, Shift Rows, MixColumns and one AddKey with subkeyl). The matrix for MixColumns can be found in Lecture 5, and how to perform the corresponding multiplication over bytes can be found in Lecture 10. (c) Print your result after the 1st round of AES encryption in terminal and write the result to a file "../data/result.txt". The result needs to be printed and written in hexadecimal. (d) Take a screenshot for the output of your function in step (c) and include it in your report. (e) You can use the example we mentioned in Lecture 5 to examine the correctness of your function. But your function should be generic and output results for other messages. Note: for the polynomial additions and multiplications over bytes in GF(28), you can implement them by yourself based on what we discussed in lecture 9 and 10 or you can find some additional libraries to perform the operations. 2. (Additional Task for CS6053) Subkey Schedule: (a) Read the first subkey from file ../data/subkey_example.txt", generate the next subkey using sub- key schedule algorithm in AES. Print the next subkey in terminal and write the result to a file ../data/result subkey.txt". The result needs to be printed and written in hexadecimal. (b) Take a screenshot for the output of your function in step (a) and include it in your report. (c) You can use the example we mentioned in Lecture 6 to examine the correctness of your function. But your function should be generic and output results for other subkeys. In this project, you will need to implement the 1st round of encryption in Advanced Encryption Candard. More specifically, - Given a message with 128 bits, two subkeys subkey0 and subkey1, your program should be able to perform one AddKey before Round 1 and the corresponding operations (SubBytes, ShiftRows, Mix- Columns, and AddKey) in Round 1, and output the result of the encryption after Round 1. (In this project, we assume S-box which is used in SubBytes is already given and you can find a copy of it from Lecture 5. We also assume an encryption key has 128 bits in this project.) Programming Language: You can use either C/C++, Python or Java. However, C/C++ or Python is preferred. You can choose any IDE you like, the code you submit should be able to compile and run in Linux or Windows. 3 Project Details Assume a plaintext file is stored in ../data/plaintext.txt". A message is in this file is Two One Nine Two And two subkeys (in hexadecimal) are given in ../data/subkey-example.txt" 54686174732060792046756 e 67204675 e232fcf191129188b159 e4e6d679 a 293 The subkey on the first line is subkey and the subkey on the second line is subkey1. Each has 128 bits. 1. First Round of AES Encryption: (a) Read a message from file ../data/plaintext.txt", change each character into ASCII. After that, you should have 128 bits and obtain an initial state (check the example we mentioned in Lecture 5). (b) Read the two subkeys from file" ./data/subkey.example.txt", calculate one AddKey before Round 1 with subkeyo, compute operations in Round 1 (includes SubBytes, Shift Rows, MixColumns and one AddKey with subkeyl). The matrix for MixColumns can be found in Lecture 5, and how to perform the corresponding multiplication over bytes can be found in Lecture 10. (c) Print your result after the 1st round of AES encryption in terminal and write the result to a file "../data/result.txt". The result needs to be printed and written in hexadecimal. (d) Take a screenshot for the output of your function in step (c) and include it in your report. (e) You can use the example we mentioned in Lecture 5 to examine the correctness of your function. But your function should be generic and output results for other messages. Note: for the polynomial additions and multiplications over bytes in GF(28), you can implement them by yourself based on what we discussed in lecture 9 and 10 or you can find some additional libraries to perform the operations. 2. (Additional Task for CS6053) Subkey Schedule: (a) Read the first subkey from file ../data/subkey_example.txt", generate the next subkey using sub- key schedule algorithm in AES. Print the next subkey in terminal and write the result to a file ../data/result subkey.txt". The result needs to be printed and written in hexadecimal. (b) Take a screenshot for the output of your function in step (a) and include it in your report. (c) You can use the example we mentioned in Lecture 6 to examine the correctness of your function. But your function should be generic and output results for other subkeys
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


