Question: Information & Network Security Project 1 A secure chatting application Requirements : 1. A multi-client one server architecture. 2. Any two or more clients can
Information & Network Security Project 1 A secure chatting application
Requirements :
1. A multi-client one server architecture.
2. Any two or more clients can chat as long as they requested a key (for encryption) from server.
3. After Opening the chat GUI :
a. Each user (client) has the choice of which encryption technique to use.
i. Will send the chosen technique to receiver (to choose the same cipher in decryption).
b. User should have the choice between sending data as (plain text, hashed, or encrypted using (caesar cipher or Playfair or AES).
4. All Key exchanges & messages are authenticated.
5. Server is the responsible party for authentication and key generation.
Specifications :
1. Build a client-server architecture that could be deployed on different machine using sockets.
2. Server side :
a. Will generate encryption keys and distribute them among clients.
b. Will use a hashing technique to help authenticating key exchange
i. Hash key before sending it to clients.
c. Server wont read messages exchanged between clients, its only responsible to facilitate client-client connection.
3. Client side :
a. Each client has a GUI interface to chat with other clients :
i. Two fields
1. One to receive in-box messages.
2. To write out-box messages.
3. Drop down menu to choose which action to take in each field (ex: encrypt using AES while sending messages).
b. Each client code is composed of :
i. Class for encryption
1. Ceaser.
2. Playfair.
3. AES.
ii. Class for authentication
1. Hashing technique
a. Will hash key after receiving it from server.
2. Comparison
a. Will compare two hashes the one generated by client and the one received from server.
i. If true then key received correctly.
ii. If False then request a new key from server. Information & Network Security Project 1 A secure chatting application
Output Example Information & Network Security Project 1 A secure chatting application
Using the OOP is a necessary in this project.
The deadline to submit the code will be on Wednesday 25 April 2018 ( For All Students Registered in this Course ).
All students will submit there project as a one compressed folder. No submissions will be accepted after the deadline.
Discussion time will be posted on CSOCAL.
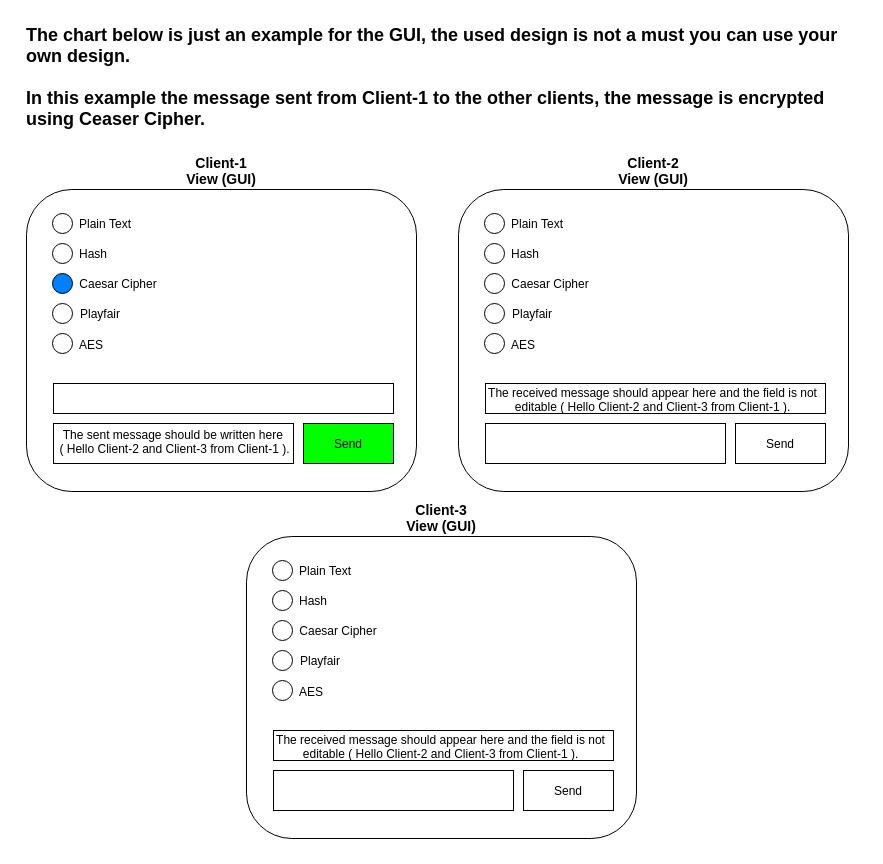
The chart below is just an example for the GUI, the used design is not a must you can use your own design In this example the message sent from Client-1 to the other clients, the message is encrypted using Ceaser Cipher. Client-1 View (GUI) Client-2 View (GUI) Plain Text Hash Caesar Cipher Playfair AES Plain Text Hash Caesar Cipher Playfair AES The received message should appear here and the field is not editable (Hello Client-2 and Client-3 from Client-1 The sent message should be written here (Hello Client-2 and Client-3 from Client-1) Send Send Client-3 View (GUI) Plain Text Hash Caesar Cipher Playfair AES The received message should appear here and the field is not editable (Hello Client-2 and Client-3 from Client-1 Send The chart below is just an example for the GUI, the used design is not a must you can use your own design In this example the message sent from Client-1 to the other clients, the message is encrypted using Ceaser Cipher. Client-1 View (GUI) Client-2 View (GUI) Plain Text Hash Caesar Cipher Playfair AES Plain Text Hash Caesar Cipher Playfair AES The received message should appear here and the field is not editable (Hello Client-2 and Client-3 from Client-1 The sent message should be written here (Hello Client-2 and Client-3 from Client-1) Send Send Client-3 View (GUI) Plain Text Hash Caesar Cipher Playfair AES The received message should appear here and the field is not editable (Hello Client-2 and Client-3 from Client-1 Send
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


