Question: **information security** write a code in NetBeans by using the language java: Create software that can encrypt and decrypt a text using Playfair algorithm. The
**information security**
write a code in NetBeans by using the language java:
Create software that can encrypt and decrypt a text using Playfair algorithm.
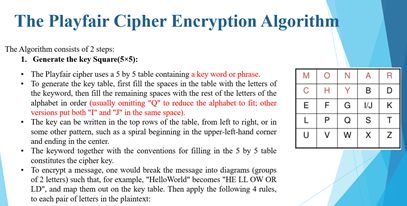
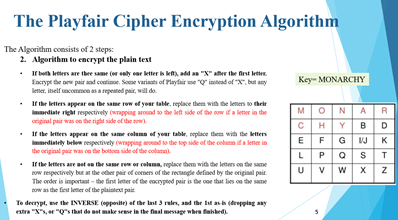
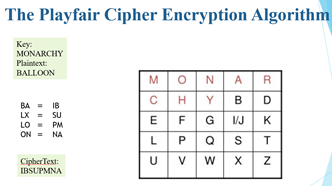
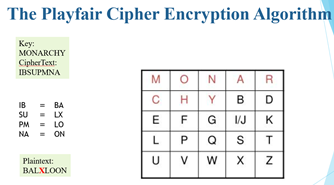
The Playfair Cipher Encryption Algorithm The Algorithm consists of 2 steps: 1. Generate the key Square(5x5): The Playfair cipher uses a 5 by 5 table containing a key word or phrase To generate the key table, first fill the spaces in the table with the letters of the keyword, then fill the remaining spaces with the rest of the letters of the alphabet in order (usually omitting "O" to reduce the alphabet to fit other versions put both "T" and "" in the same space). The key can be written in the top rows of the table, from left to right or in some other pattern, such as a spiral beginning in the upper-left-hand comer and ending in the center The keyword together with the conventions for filling in the 5 by 5 table constitutes the cipher key To encrypt a message, one would break the message into diagrams (groups of letters) such that, for example, "Hello World" becomes "HE LLOW OR LD". and map them out on the key table. Then apply the following 4 rules. to each pair of letters in the plaintext: MONA CHYB E E F G 10 LPOS U V W X NO The Playfair Cipher Encryption Algorithm Key MONARCHY The Algorithm consists of 2 steps: 2. Algorithm to encrypt the plain text If wetters are the same for a car letters eft, add a "X" after the first letter Encrype the new pair and come Sose variants of Payar seinad of "X", but any lenser, itself access a repeated pair, wall de Tribe letters appear on the same row of your table replace them with the lines to their Immediate right respectively wrapping around to the left side of the wow if a letter in the original pair was detergeside of the If the files appear on the same column of your table place them with the letters Immediately blow respectively wrapping and to the side of the columiin the original pair was the side of the com . If the Wetters are not the same row or coloms.replace them with the letters on the same now respectively but at the oder pair of comes of the rectangle defined by the original pait The order is important - the first letter of the encrypted pair is the one that lies on the same was the first leer of the plante pait To decrypt, the INVERSE opposite of the last 3 run, and the Issa (drepping any extra "X", "stat de wat make sease in the final message when fiabled MONAR CHYBD EFGWK LPOS V W X T Z U The Playfair Cipher Encryption Algorithm Key: MONARCHY Plaintext: BALLOON BA = 18 LX = SU LO - PM ON = NA MONAR CHYBD E F G F G IJK LP Q S T U V w Z Cipher Text: IBSUPMNA The Playfair Cipher Encryption Algorithm Key: MONARCHY Cipher Text: IBSUPMNA IB - BA SU LX PM - LO NA - ON MONAR | | Y | E F G I/ JK L P Q S U V W YEN Plaintext: BALXLOON
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


