Question: is based on a physical random process such as flipping a coin or rolling a dice Pseudorandom Number Generate (PNG) Crytographically Secure Random Number Generate
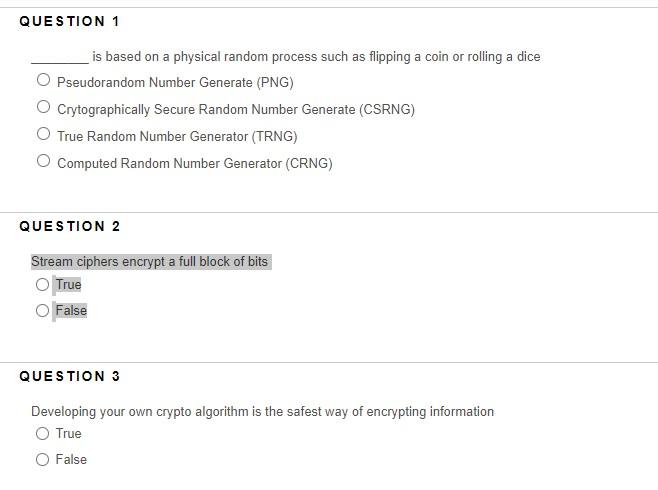
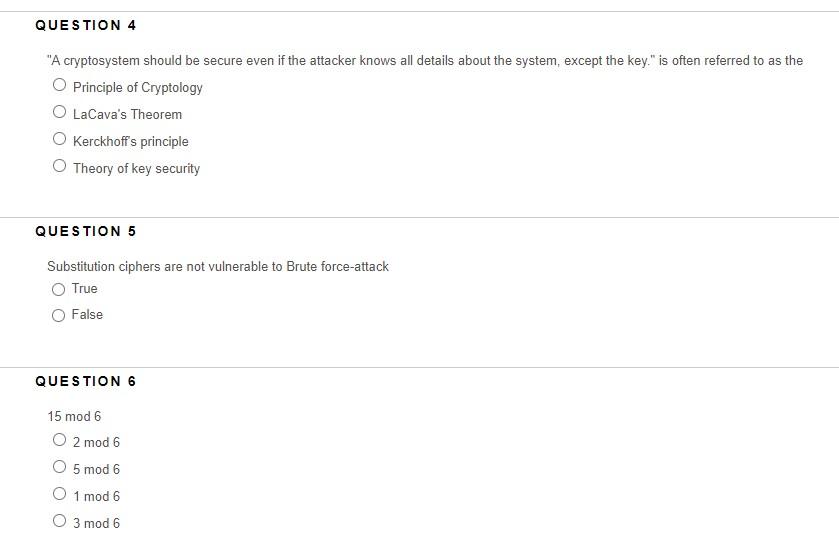
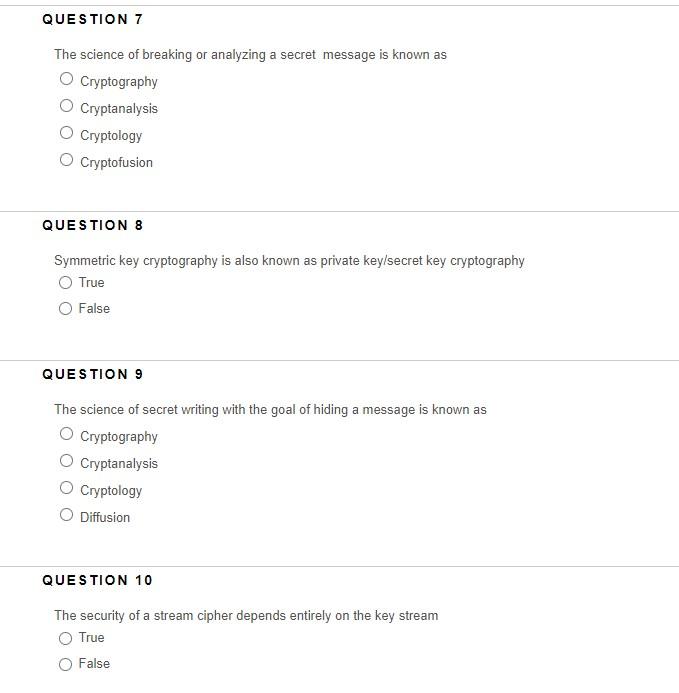
is based on a physical random process such as flipping a coin or rolling a dice Pseudorandom Number Generate (PNG) Crytographically Secure Random Number Generate (CSRNG) True Random Number Generator (TRNG) Computed Random Number Generator (CRNG) QUESTION 2 Stream ciphers encrypt a full block of bits True False QUESTION 3 Developing your own crypto algorithm is the safest way of encrypting information True False "A cryptosystem should be secure even if the attacker knows all details about the system, except the key." is often referred to as the Principle of Cryptology LaCava's Theorem Kerckhoff's principle Theory of key security QUESTION 5 Substitution ciphers are not vulnerable to Brute force-attack True False The science of breaking or analyzing a secret message is known as Cryptography Cryptanalysis Cryptology Cryptofusion QUESTION 8 Symmetric key cryptography is also known as private key/secret key cryptography True False QUESTION 9 The science of secret writing with the goal of hiding a message is known as Cryptography Cryptanalysis Cryptology Diffusion QUESTION 10 The security of a stream cipher depends entirely on the key stream True False
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


