Question: IT 6823 Information Security Concept and Administration Home Work 1, Marks: 100 Python code please 1. Write a program in any language you like (Python)
IT 6823 Information Security Concept and Administration
Home Work 1, Marks: 100
Python code please
1. Write a program in any language you like (Python) to implement Vigenere Ciphering and deciphering schemes. [50 Marks]
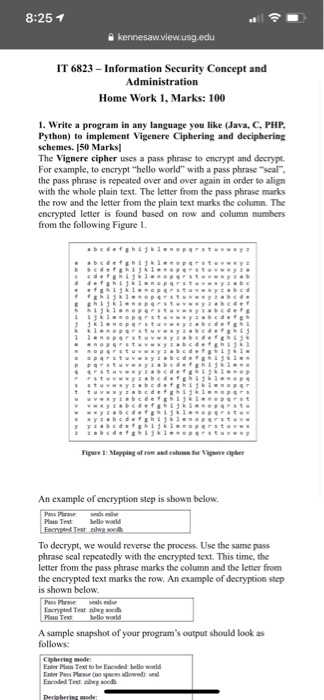
The Vignere cipher uses a pass phrase to encrypt and decrypt. For example, to encrypt hello world with a pass phrase seal, the pass phrase is repeated over and over again in order to align with the whole plain text. The letter from the pass phrase marks the row and the letter from the plain text marks the column. The encrypted letter is found based on row and column numbers from the following Figure 1.
An example of encryption step is shown below.
To decrypt, we would reverse the process. Use the same pass phrase seal repeatedly with the encrypted text. This time, the letter from the pass phrase marks the column and the letter from the encrypted text marks the row. An example of decryption step is shown below.
A sample snapshot of your programs output should look as follows:
2. Write a program that ciphers a plain text message using double transposition scheme and vice versa. [50 Marks]
The program should accept five tuples of input: plain text, row, column, permutation of row and columns. An example of encrypted text for the plain text attack at dawn is shown below.
Similarly, your program should decrypt the encrypted text given the encrypted text, matrix row and column sizes, row and column permutation order. An example snapshot of output is shown below:

8:25 1 kennesaw.view.usg.edu IT 6823 Information Security Concept and Administration Home Work 1, Marks: 100 1. Write a program in any language you like (Java, C, PHP, Python) to implement Vigenere Ciphering and deciphering schemes. [50 Marks] The Vignere cipher uses a pass phrase to encrypt and decrypt. For example, to encrypt "hello world" with a pass phrase "seal". the pass phrase is repeated over and over again in order to align with the whole plain text. The letter from the pass phrase marks the row and the letter from the plain text marks the column. The encrypted letter is found based on row and column numbers from the following Figure 1. bedete Figure 1: Mapping of rew and columa fr Vigre cier An example of encryption step is shown below. Pass Parane e bello world Plain Test Encryted Test zil To decrypt, we would reverse the process. Use the same pass phrase seal repeatedly with the encrypted text. This time, the letter from the pass phrase marks the column and the letter from the encrypted text marks the row. An example of decryption step is shown below. Pass Phrse seals ealse Encrypted Test alwg aed Plain Text belle world A sample snapshot of your program's output should look as follows: Ciphering mode: Enter Plain Text to be Encoded bello world Enter Pass Phrase (no spaces allowed): seal Encoded Test alwg aocdh Decpbering mede 8:25 1 kennesaw.view.usg.edu Figure 1: Mapping of rem and columa fer Vignere cipher An example of encryption step is shown below. Pas Phrave Plain Test as eale bello world Encrypted Test zilwg, M To decrypt, we would reverse the process. Use the same pass phrase seal repeatedly with the encrypted text. This time, the letter from the pass phrase marks the column and the letter from the encrypted text marks the row. An example of decryption step is shown below. Pas Phrae seals eale Eacrypted Test nlwg aocdh Plain Text bello world A sample snapshot of your program's output should look as follows: Ciphering mode: Enter Pan Test to be Encoded bello world Enter Pass Phrase (no spaces allowed): seal Eacoded Test alwg aoeda Deciphering mode: Ester Encoded Test to be Decoded zilwg aoedh Enter Pass Pee (no spaces allowed): seal Decoded Plain Text bello world 2. Write a program that ciphers a plain text message using double transposition scheme and vice versa. [50 Marks The program should accept five tuples of input: plain text, row, column, permutation of row and columns. An example of encrypted text for the plain text "attack at dawn" is shown below. Plain test aack at dew Matrix ow sizr S Matrix colmn se Row pemutation order. 3,5, 1,4,2 Colan pemutation order 1.3,2 Enerypted tret twnattadake Similarly, your program should decrypt the encrypted text given the encrypted text, matrix row and column sizes, row and column permutation order. An example snapshot of output is shown below: Lacrypted text xtawattadake Matrix row size5 Matrix coln size Row pemautation crder 3,5, 1,4,2 Coln pentation order 1. A2 Plain test attack at drun
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


