Question: IT Auditing course The answers here it is correct just I need only justification for each question Case study A The IS auditor has been

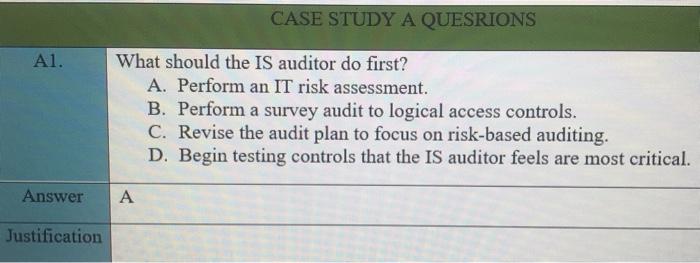
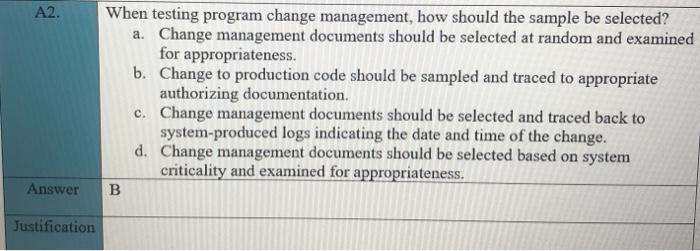
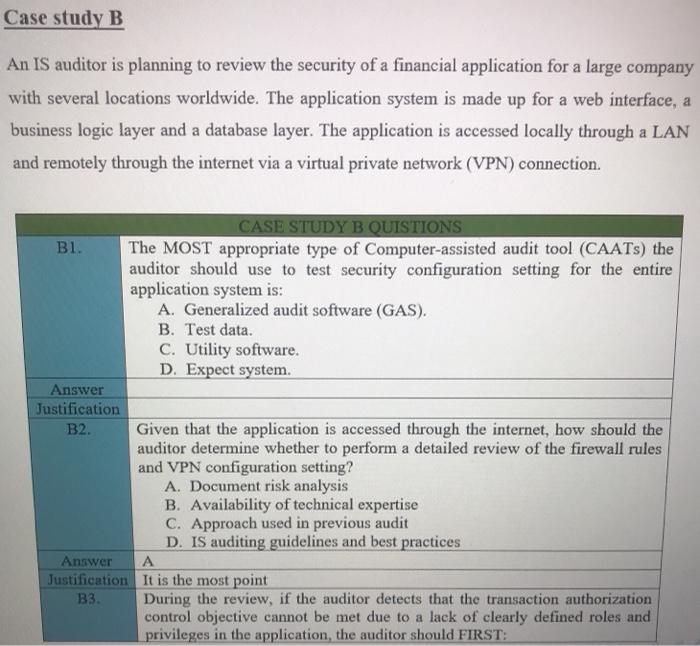


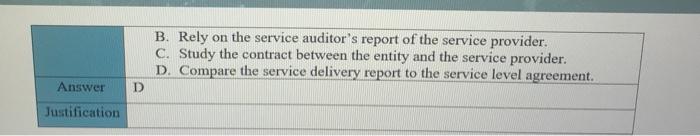
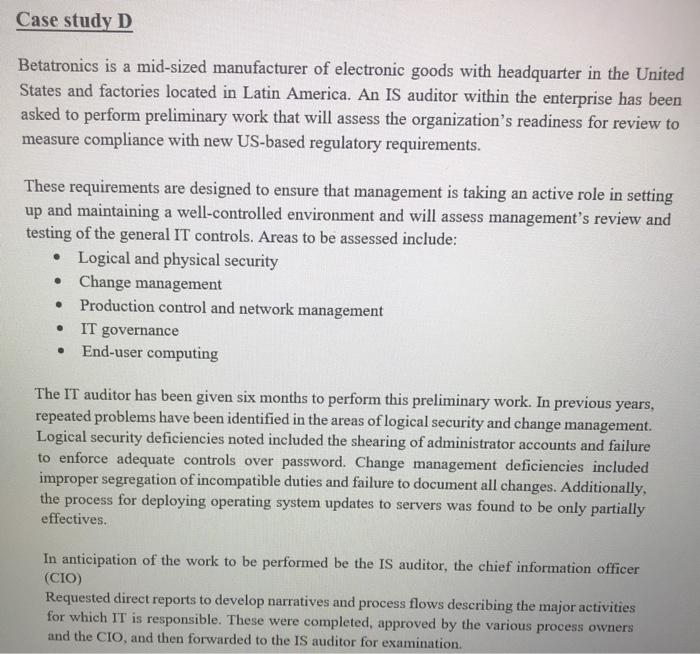
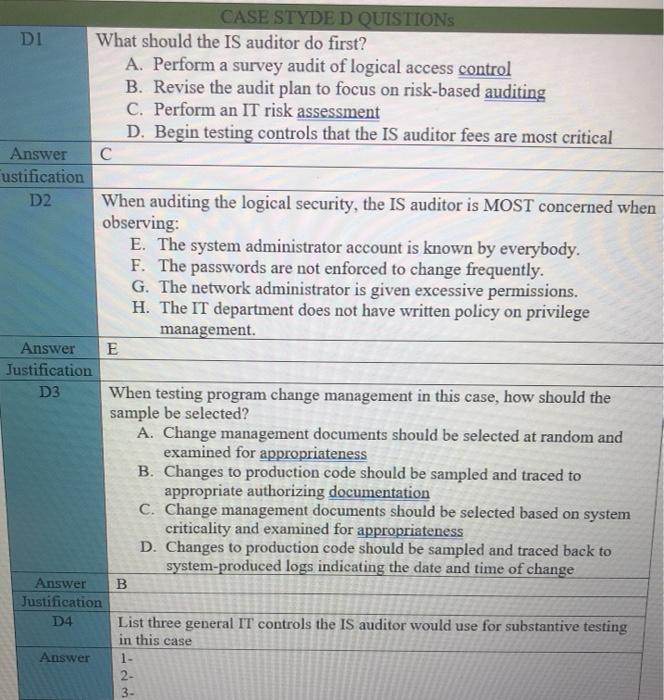
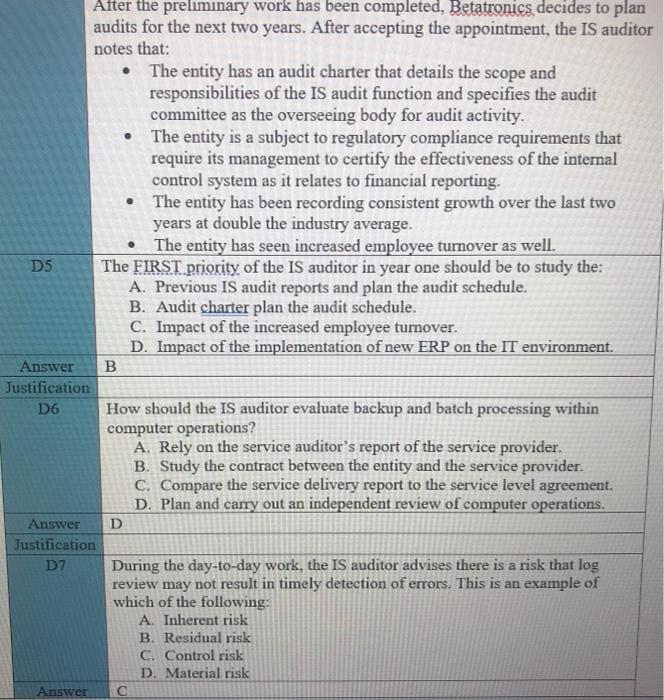
Case study A The IS auditor has been asked to assess the readiness of the organization for a review to measure compliance with new regulatory requirements. These requirements are designed to ensure that management is taking an active role in setting up and maintaining a well-controlled environment, and accordingly, will assess management's review and testing of the general IT control environment. Areas to be assessed include logical and physical security, change management, production control and network management. IT governance, and end-user computing The IS auditor has been given six months to perform this preliminary work, so sufficient time should be available. It should be noted that in previous years, repeated problems have been identified in the areas of logical security and change management, so these areas will most likely require some degree of remediation. Logical security deficiencies noted included the shearing of administrator account and failure to enforce adequate controls over passwords. Change management deficiencies included improper segregation of incompatible duties and failure to document all changes. Additionally, the process for deploying OS updates to servers was found to be only partially effective. In anticipation of the work to be performed by the IS auditor, the chief information officer (CIO) requested direct reports describing the major activities for which IT is responsible. These were completed, approved by the various process owners and CIO, and then forward to the IS auditor for examination. CASE STUDY A QUESRIONS Al. What should the IS auditor do first? A. Perform an IT risk assessment. B. Perform a survey audit to logical access controls. C. Revise the audit plan to focus on risk-based auditing. D. Begin testing controls that the IS auditor feels are most critical. Answer A Justification A2. When testing program change management, how should the sample be selected? a. Change management documents should be selected at random and examined for appropriateness. b. Change to production code should be sampled and traced to appropriate authorizing documentation c. Change management documents should be selected and traced back to system-produced logs indicating the date and time of the change. d. Change management documents should be selected based on system criticality and examined for appropriateness. Answer B Justification Case study B An IS auditor is planning to review the security of a financial application for a large company with several locations worldwide. The application system is made up for a web interface, a business logic layer and a database layer. The application is accessed locally through a LAN and remotely through the internet via a virtual private network (VPN) connection. CASE STUDY B QUISTIONS B1. The MOST appropriate type of Computer-assisted audit tool (CAATs) the auditor should use to test security configuration setting for the entire application system is: A. Generalized audit software (GAS). B. Test data. C. Utility software. D. Expect system. Answer Justification B2. Given that the application is accessed through the internet, how should the auditor determine whether to perform a detailed review of the firewall rules and VPN configuration setting? A. Document risk analysis B. Availability of technical expertise C. Approach used in previous audit D. IS auditing guidelines and best practices Answer A Justification It is the most point B3. During the review, if the auditor detects that the transaction authorization control objective cannot be met due to a lack of clearly defined roles and privileges in the application, the auditor should FIRST: A. Review the authorization on a sample of transaction. B. Immediately report this finding to upper management. C. Request that auditee management review the appropriateness of access rights for all users. D. Use GAS to check the integrity of the database. A Answer Justification Case study C An IS auditor has been appointed to carry out IS audits in an entity for a period of two years. After accepting the appointment, the IS auditor noted that: The entity has an audit charter that detailed, among other things, the scope and responsibilities of the IS audit function and specifies the audit committee as the overseeing body for audit activity. The entity is planning a major increase in IT investment, mainly on account of implementation of a new Enterprise resource planning (ERP) application, integrating business processes across units dispersed geographically. The ERP implementation is expected to become operational within the next 90 days. The servers supporting the business applications are hosted offsite by a third-party service provider. The entity has a new incumbent as chief information security officer (CISO) who reports to the chief financial officer (CFO). The entity is subject to regulatory compliance requirements that require its management to certify the effectiveness of the internal control system as it relates to financial reporting. The entity has been recording consistent growth over the last two years at double the industry average. However, the entity has seen increased employee turnover as well. CI. CASE STYDE C QUISTIONS The FIRST priority of the IS auditor in year one should be to study the: A. Previous IS audit reports and plan the audit schedule. B. Audit charter and plan the audit schedule. C. Impact of the new incumbent as CISO. D. Environment and plan the audit schedule. B or D Answer Justification C2. How should the IS auditor evaluate backup and batch processing within computer operations? A. Plan and carry out an independent review of computer operations. B. Rely on the service auditor's report of the service provider. C. Study the contract between the entity and the service provider. D. Compare the service delivery report to the service level agreement. Answer D Justification Case study D Betatronics is a mid-sized manufacturer of electronic goods with headquarter in the United States and factories located in Latin America. An IS auditor within the enterprise has been asked to perform preliminary work that will assess the organization's readiness for review to measure compliance with new US-based regulatory requirements. These requirements are designed to ensure that management is taking an active role in setting up and maintaining a well-controlled environment and will assess management's review and testing of the general IT controls. Areas to be assessed include: Logical and physical security Change management Production control and network management IT governance End-user computing The IT auditor has been given six months to perform this preliminary work. In previous years, repeated problems have been identified in the areas of logical security and change management. Logical security deficiencies noted included the shearing of administrator accounts and failure to enforce adequate controls over password. Change management deficiencies included improper segregation of incompatible duties and failure to document all changes. Additionally, the process for deploying operating system updates to servers was found to be only partially effectives. In anticipation of the work to be performed be the IS auditor, the chief information officer (CIO) Requested direct reports to develop narratives and process flows describing the major activities for which IT is responsible. These were completed, approved by the various process owners and the CIO, and then forwarded to the IS auditor for examination CASE STYDED QUISTIONS DI What should the IS auditor do first? A. Perform a survey audit of logical access control B. Revise the audit plan to focus on risk-based auditing C. Perform an IT risk assessment D. Begin testing controls that the IS auditor fees are most critical Answer ustification D2 When auditing the logical security, the IS auditor is MOST concerned when observing: E. The system administrator account is known by everybody. F. The passwords are not enforced to change frequently. G. The network administrator is given excessive permissions. H. The IT department does not have written policy on privilege management. Answer E Justification D3 When testing program change management in this case, how should the sample be selected? A. Change management documents should be selected at random and examined for appropriateness B. Changes to production code should be sampled and traced to appropriate authorizing documentation C. Change management documents should be selected based on system criticality and examined for appropriateness D. Changes to production code should be sampled and traced back to system-produced logs indicating the date and time of change Answer B Justification D4 List three general IT controls the IS auditor would use for substantive testing in this case Answer 1- 2- B 3- D5 After the preliminary work has been completed, Betatronics decides to plan audits for the next two years. After accepting the appointment, the IS auditor notes that: The entity has an audit charter that details the scope and responsibilities of the IS audit function and specifies the audit committee as the overseeing body for audit activity. The entity is a subject to regulatory compliance requirements that require its management to certify the effectiveness of the internal control system as it relates to financial reporting. The entity has been recording consistent growth over the last two years at double the industry average. The entity has seen increased employee turnover as well. The FIRST priority of the IS auditor in year one should be to study the A. Previous IS audit reports and plan the audit schedule. B. Audit charter plan the audit schedule. C. Impact of the increased employee turnover. D. Impact of the implementation of new ERP on the IT environment. Answer . Justification D6 How should the IS auditor evaluate backup and batch processing within computer operations? A. Rely on the service auditor's report of the service provider. B. Study the contract between the entity and the service provider. C. Compare the service delivery report to the service level agreement. D. Plan and carry out an independent review of computer operations. Answer D Justification D7 During the day-to-day work, the IS auditor advises there is a risk that log review may not result in timely detection of errors. This is an example of which of the following: A. Inherent risk B. Residual risk C. Control risk D. Material risk
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


