Question: IT454: INFORMATION SECURITY AUDIT AND FORENSICS FIVE QUESTION Ringer LL QUESTIONS Question 1 a) During an investigation, evidence needs to be gathered. In digital forensics,

IT454: INFORMATION SECURITY AUDIT AND FORENSICS
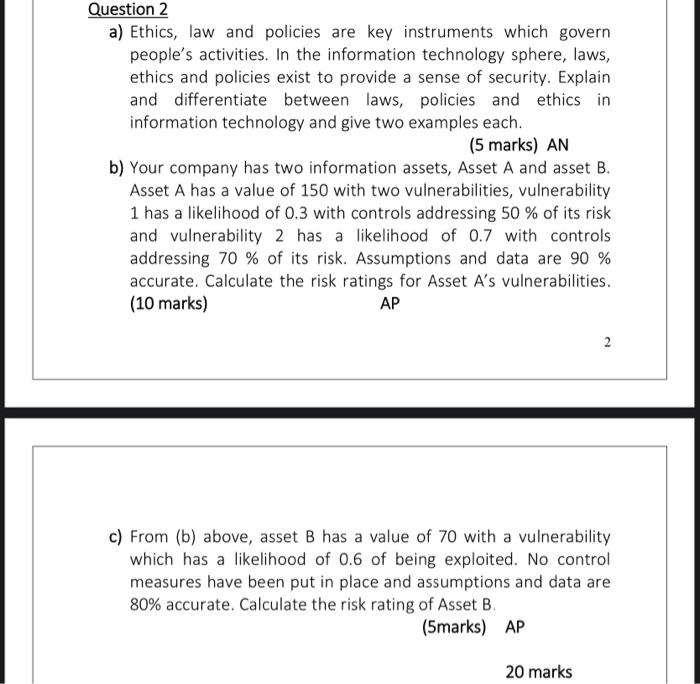
FIVE QUESTION Ringer LL QUESTIONS Question 1 a) During an investigation, evidence needs to be gathered. In digital forensics, evidence is usually intangible and in the form of data which needs to be acquired from the offender's computer. Describe in your own words the methods you can use to acquire data for digital evidence. (8 marks) AP b) In responding to a computer forensics incident, one of the first things you need to do is to secure the incident scene. Explain why it is necessary to secure the incident/crime scene. (6 marks) AN c) Describe three actions you can take to secure and incident/crime scene as part of your response to the computer forensic incident/crime. (6 marks) AN 20 marks Question 2 a) Ethics, law and policies are key instruments which govern people's activities. In the information technology sphere, laws, ethics and policies exist to provide a sense of security. Explain and differentiate between laws, policies and ethics in information technology and give two examples each. (5 marks) AN b) Your company has two information assets, Asset A and asset B. Asset A has a value of 150 with two vulnerabilities, vulnerability 1 has a likelihood of 0.3 with controls addressing 50 % of its risk and vulnerability 2 has a likelihood of 0.7 with controls addressing 70 % of its risk. Assumptions and data are 90 % accurate. Calculate the risk ratings for Asset A's vulnerabilities. (10 marks) AP c) From (b) above, asset B has a value of 70 with a vulnerability which has a likelihood of 0.6 of being exploited. No control measures have been put in place and assumptions and data are 80% accurate. Calculate the risk rating of Asset B. (5marks) AP 20 marks
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


