Question: Knowledge Check Content Suppose you get to the office, open your email, and find this message waiting for you: table [ [ From: ,
Knowledge Check Content
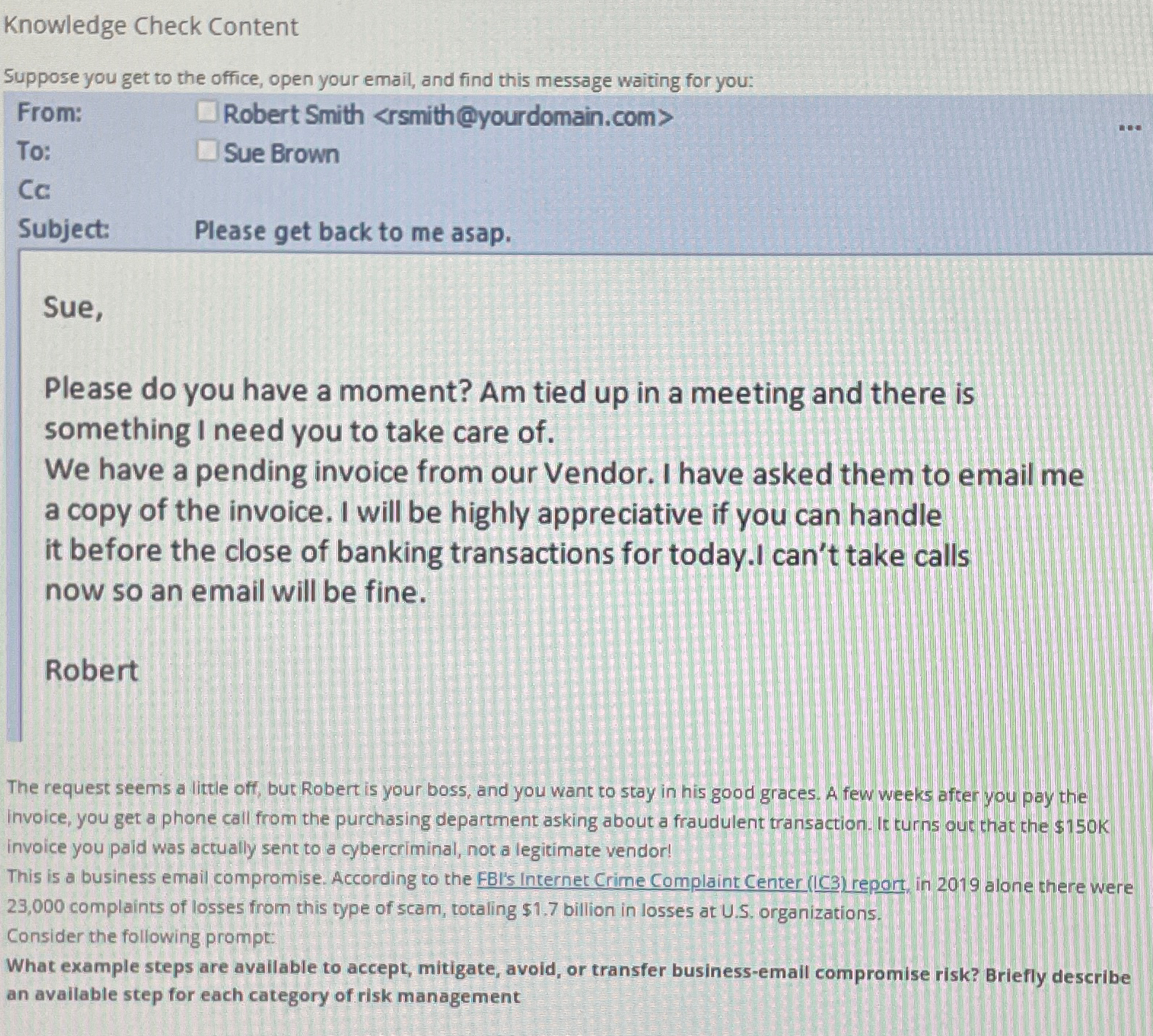
Suppose you get to the office, open your email, and find this message waiting for you:
tableFrom:Robert Smith
rsmith@yourdomain.comTo:Sue BrownCcSubject:Please get back to me asap.
Sue,
Please do you have a moment? Am tied up in a meeting and there is something I need you to take care of
We have a pending invoice from our Vendor. I have asked them to email me a copy of the invoice. I will be highly appreciative if you can handle
it before the close of banking transactions for today.I can't take calls now so an email will be fine.
Robert
The request seems a little off, but Robert is your boss, and you want to stay in his good graces. A few weeks after you pay the invoice, you get a phone call from the purchasing department asking about a fraudulent transaction. It turns out that the $ invoice you paid was actually sent to a cybercriminal, not a legitimate vendor!
This is a business email compromise. According to the FBI's Internet Crime Complaint Center IC report, in alone there were complaints of losses from this type of scam, totaling $ billion in losses at US organizations.
Consider the following prompt:
What example steps are avaliable to accept, mitigate, avoid, or transfer businessemail compromise risk? Briefly describe an available step for each category of risk management
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


