Question: Let F be a pseudorandom function and G be a pseudorandom generator with expansion factor p(n) = n +1. Suppose the shared key is
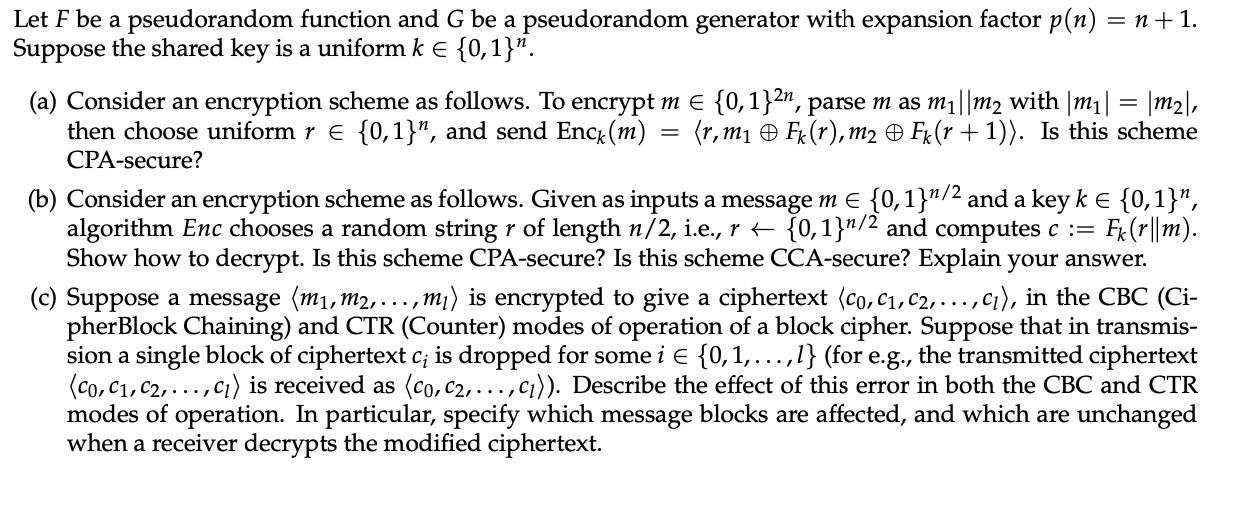
Let F be a pseudorandom function and G be a pseudorandom generator with expansion factor p(n) = n +1. Suppose the shared key is a uniform k = {0,1}. (a) Consider an encryption scheme as follows. To encrypt m = {0,1}2n, parse m as m||m2 with |m| = |m|, then choose uniform r = {0,1}", and send Enck (m) (r,m Fk (r), m2 Fk (r + 1)). Is this scheme CPA-secure? = (b) Consider an encryption scheme as follows. Given as inputs a message m = {0,1}/2 and a key k = {0,1}", algorithm Enc chooses a random string r of length n/2, i.e., r t [0,1]/2 and computes c := Fk (r||m). Show how to decrypt. Is this scheme CPA-secure? Is this scheme CCA-secure? Explain your answer. (c) Suppose a message (m, m2,..., .,m) is encrypted to give a ciphertext (co, C, C2, ...,c), in the CBC (Ci- pher Block Chaining) and CTR (Counter) modes of operation of a block cipher. Suppose that in transmis- sion a single block of ciphertext c; is dropped for some i {0, 1,...,1l} (for e.g., the transmitted ciphertext (co, C, C, ..., c) is received as (co, c2, ..., c)). Describe the effect of this error in both the CBC and CTR modes of operation. In particular, specify which message blocks are affected, and which are unchanged when a receiver decrypts the modified ciphertext.
Step by Step Solution
There are 3 Steps involved in it
a The given encryption scheme is not CPAsecure An adversary can distinguish between two encryptions ... View full answer

Get step-by-step solutions from verified subject matter experts


