Question: Library Resources D Question 1 2 pts Time Elapsed: Hide 0 Minutes, 20 Seconds What is considered the first step in formulating a security policy?
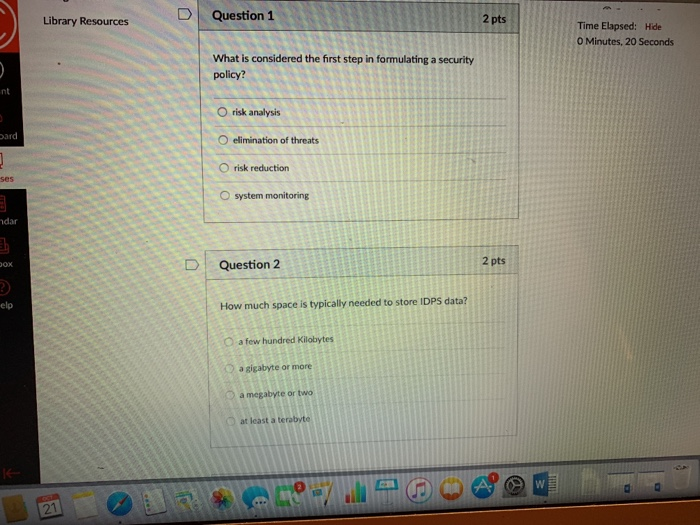
Library Resources D Question 1 2 pts Time Elapsed: Hide 0 Minutes, 20 Seconds What is considered the first step in formulating a security policy? nt O risk analysis Oelimination of threats O risk reduction O system monitoring ard dar DQuestion 2 2 pts elp How much space is typically needed to store IDPS data? O a few hundred Kilobytes a gigabyte or more a megabyte or two D at least a terabyte
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


