Question: Match each attack with its definition. The attacker executes code in the underlying data store by means of a web form The attacker leaves some
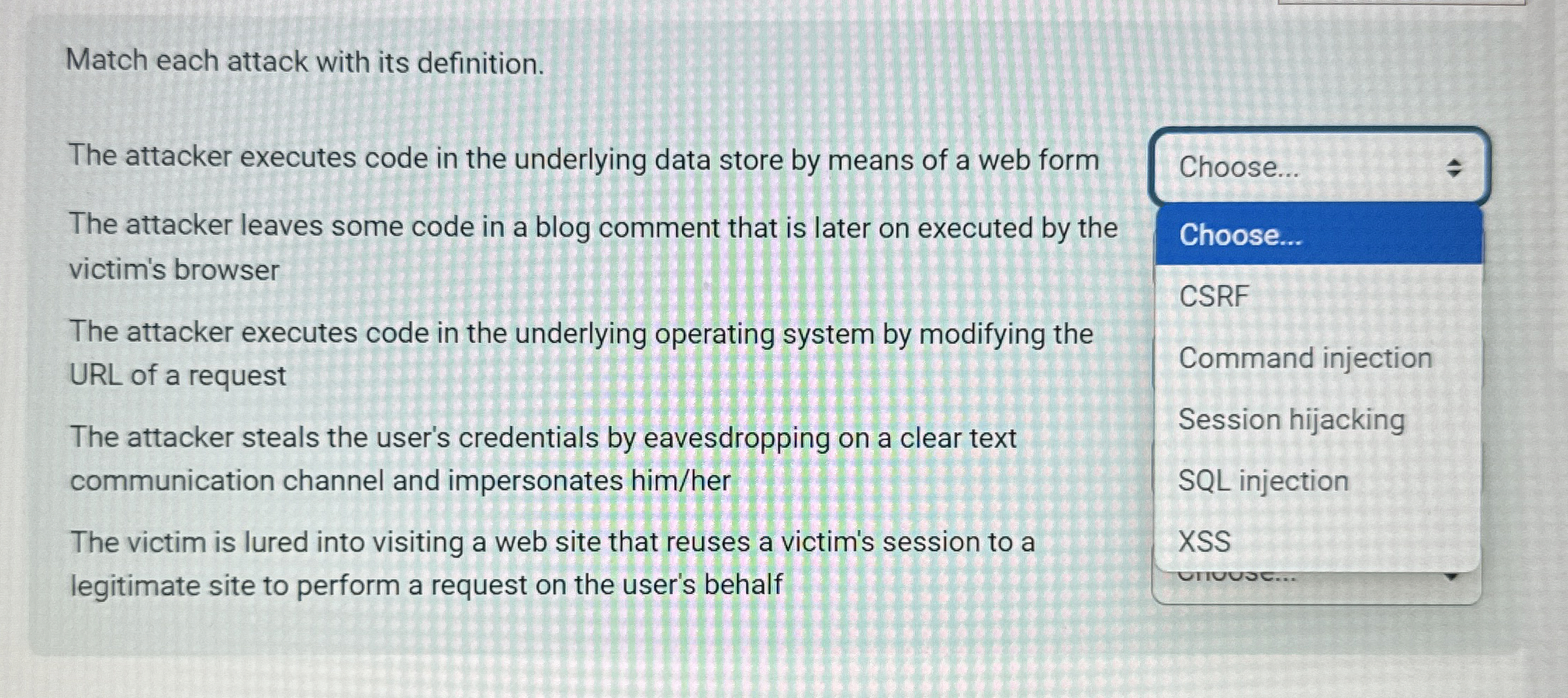
Match each attack with its definition.
The attacker executes code in the underlying data store by means of a web form
The attacker leaves some code in a blog comment that is later on executed by the victim's browser
The attacker executes code in the underlying operating system by modifying the URL of a request
The attacker steals the user's credentials by eavesdropping on a clear text communication channel and impersonates himher
The victim is lured into visiting a web site that reuses a victim's session to a legitimate site to perform a request on the user's behalf
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


