Question: match the threats to cloud computing to the description.Match the threats to cloud computing to the description. occurs when user accounts or access privileges are
match the threats to cloud computing to the description.Match the threats to cloud computing to the description.
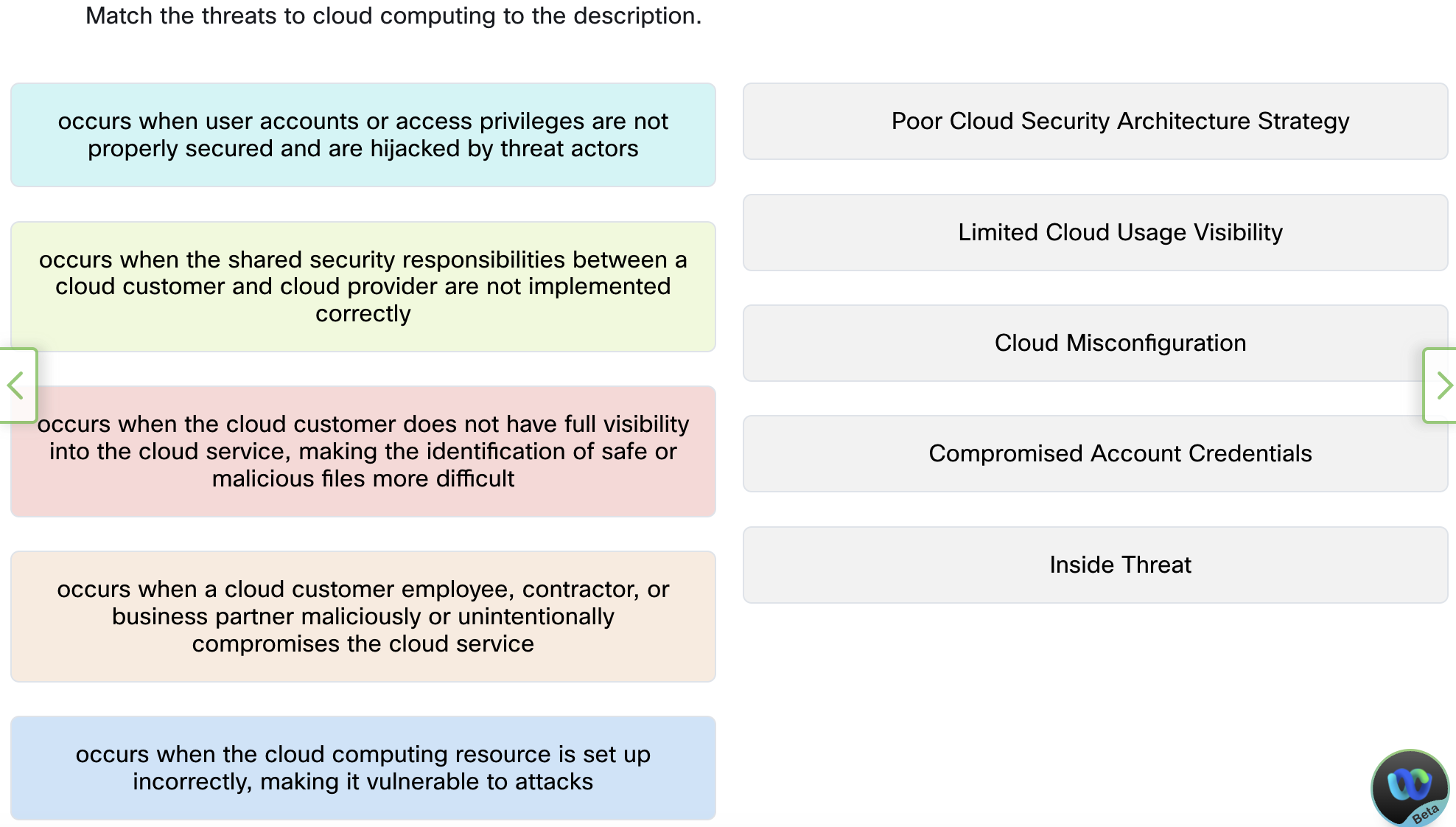
occurs when user accounts or access privileges are not
properly secured and are hijacked by threat actors
occurs when the shared security responsibilities between a
cloud customer and cloud provider are not implemented
correctly
occurs when the cloud customer does not have full visibility
into the cloud service, making the identification of safe or
malicious files more difficult
occurs when a cloud customer employee, contractor, or
business partner maliciously or unintentionally
compromises the cloud service
occurs when the cloud computing resource is set up
incorrectly, making it vulnerable to attacks
Poor Cloud Security Architecture Strategy
Limited Cloud Usage Visibility
Cloud Misconfiguration
Compromised Account Credentials
Inside Threat
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


